Simplify Governance Of User Access Automate Provisioning And De
- Data Access Governance RSA Data Access Governance provides IT organizations with the ability to monitor, report on and certify the legitimacy of user access permissions to unstructured data resources stored on Microsoft Windows, Linux and UNIX file servers network-attached storage devices and Microsoft SharePoint servers.
- Role Management RSA Business Role Manager delivers top-down and bottom-up role discovery, creation, modeling and suggestions. It helps streamline access based on birthright entitlements associated with specific functional roles so that, for example, HR managers receive access to HR systems. It also enables a metrics-driven approach to role modeling based on pattern analysis and policy validation.
Please Sign In Via Linkedin To Access Your Free
Signing in also unlocks access to the dynamic version of the Data Quadrant, which plots vendors based on verified user reviews! Customize the Data Quadrant according to the features and sentiments that matter most to you.
Please note: the dynamic version of the Data Quadrant continues to collect data after report publication, and may show new data that will appear in next years report.
This offer is available until May 31, 2020. These reports are intended for internal strategic use only and are not authorized for redistribution. For permission to reuse content, please contact .
Rsa Identity Governance And Lifecycle: A Phased Approach To Success
RSA Identity Governance RSA Identity Governance simplifies how user access is governed across the enterprise. RSA Identity Governance makes it possible to achieve sustainable compliance by fully automating the monitoring, reporting, certification and remediation of user entitlements.
- Gain enterprise-wide visibility into all user access privileges and high risk applications
- Identify orphan accounts and inappropriate user access to reduce risk of audit failure and data breaches
- Transfer access certification responsibility and accountability to the people who understand access needs bestthe business. Business-driven certification negates access approval rubber stamping.
- Automate access review and certification processes for greater operational efficiency, cost and time savingsflag issues between formal review campaigns
- Implement security and compliance controls to ensure policy objectives are continuously met
RSA Identity Lifecycle RSA Identity Lifecycle streamlines access request and fulfillment processes using business language to ensure users, both new and those changing roles, gain timely and appropriate access to the resources they need in accordance with compliance objectives.
- Bridge the gap between IAM and GRC
- Reduce enterprise risk
Read Also: What Do Government Contractors Do
Securid An Rsa Business Proceed Zero Trust Hybrid Workforce Security And Protection
SecurID, the trusted identity platform and an RSA business, today announced innovations that empower security-sensitive organizations to work dynamically, accelerate their cloud journeys and advance zero trust security with the general availability of SecurID Governance and Lifecycle Cloud.
As the trusted identity platform, our customers continue to rely on SecurID to manage and protect their data, users and applications. That trust continues fueling our innovation agenda and our commitment to offer choice to our customers. SecurID Governance and Lifecycle Cloud will enable customers to consume this solution from the cloud or on-premises to address todays ever-growing identity challenges, said RSA CEO Rohit Ghai.
Businesses everywhere are grappling with the need to secure hybrid workforces, the accelerating pace of digital transformation, and increasingly complex regulatory environments. These challenges are exacerbated by ransomware syndicates and other advanced threats that exploit cybersecurity professionals limited resources and bandwidth, frequently by targeting vulnerabilities in identity and access management and identity governance and administration . These pressures require new solutions that both deliver immediate business value and advance organizations long-term strategies.
Availability
About SecurID
News Summary:
For Latest Updates Follow us on
Achieve A Sustainable Identity Access Management Program
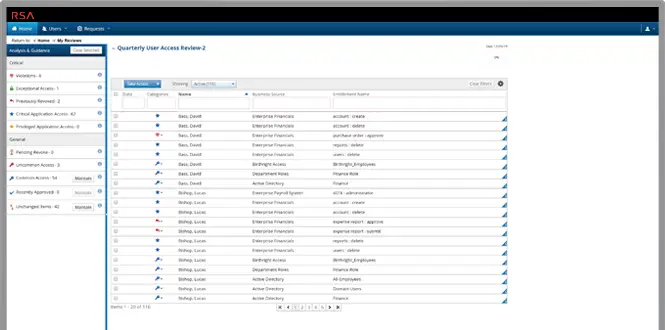
RSA Identity Governance and Lifecycle helps lower costs and boost operational efficiencies so organizations can achieve a sustainable IAM program.
With RSA Identity Governance and Lifecycle, staff can configure connections to applications and data, on-going policy administration, certification campaigns and system maintenance. All of this without costly customized coding means reduced costs to deploy and maintain as well as rapid time-to-value to deliver business results
- Attain more efficient operations at lower cost
- Develop and manage measureable and enforceable access policies
- Drive business adoption with interoperability with widely-used service desks like ServiceNow
- Achieve process optimization for governance and lifecycle
Also Check: Practice Test For Government Jobs
Rsa Identity Governance And Lifecycle On Demand Od Subscription Level 1
Subscriptions include all of the On-Demand self-paced training that is available under the specific subscription level during the entire one year subscription period. Under a Level 1 subscription, the subscription holder can consume On-Demand Classroom, On-Demand Labs and On-Demand Learning offerings during the one year subscription period.
- Access certification
Add the products you would like to compare, and quickly determine which is best for your needs.
ReturnsOffers^DELL PREFERRED ACCOUNT :
Nsa Dual: Ec: Drbg Backdoor
From 2004 to 2013, RSA shipped security softwareBSAFE toolkit and Data Protection Managerthat included a default cryptographically secure pseudorandom number generator, Dual EC DRBG, that was later suspected to contain a secret National Security Agencykleptographicbackdoor. The backdoor could have made data encrypted with these tools much easier to break for the NSA, which would have had the secret private key to the backdoor. Scientifically speaking, the backdoor employs kleptography, and is, essentially, an instance of the Diffie Hellman kleptographic attack published in 1997 by Adam Young and Moti Yung.
Nevertheless, NIST included Dual_EC_DRBG in its 2006 NIST SP 800-90A standard with the default settings enabling the backdoor, largely at the behest of NSA officials, who had cited RSA Security’s early use of the random number generator as an argument for its inclusion. The standard did also not fix the unrelated problem that the CSPRNG was predictable, which Gjøsteen had pointed out earlier in 2006, and which led Gjøsteen to call Dual_EC_DRBG not cryptographically sound.
At the 2014 RSA Conference, former RSA Security Executive Chairman Art Coviello defended RSA Security’s choice to keep using Dual_EC_DRBG by saying “it became possible that concerns raised in 2007 might have merit” only after NIST acknowledged the problems in 2013.
You May Like: California Government Tort Claim Form
How Was The Initial Setup
The initial setup is straightforward and it is definitely easy to deploy. That said, there are some complexities in the setup that are inherent to any security product.
The length of time for deployment depends on how many devices you are trying to integrate with. One of my deployments involved 2,500 users with 500 devices, and it took between 20 and 25 days to complete.
Home Security Bloggers Network How Rsa Identity Governance And Lifecycle Improves Remote Work How Rsa Identity Governance And Lifecycle Improves Remote Work
Password management can be an overlooked IAM function until you need it. Slow down the pace and cost of Service Desk requests to reset users? passwords and onboard new users with RSA Identity Governance and Lifecycle.
*** This is a Security Bloggers Network syndicated blog from RSA Blog authored by RSA Blog. Read the original post at:
Don’t Miss: City Of Las Vegas Government Jobs
Extend The Value Of Your Rsa Portfolio Investments
Todays solutions are being asked to solve bigger security challenges than originally intended. RSA Identity Governance and Lifecycle helps reduce identity risks with complementary RSA solutions to extend the value of your RSA investments.
Works with RSA SecurID Access to provide a complete, integrated Identity & Access Assurance solution that removes the need to tradeoff between convenience and security and eliminates Islands of Identity
Works with RSA Archer Suite for:
- Continuous monitoring of identity controls to reduce risk
- Appropriate access decisions based on application risk
- Improved incident response with business and identity context
Works with RSA NetWitness Suite to:
- Provide general identity context for the security analyst including access logs
- Make identity information available to better inform the investigative process
- Provide identity information to the behavior analytic engine as input data to discover risky user behavior
- Provide privileged user information to the security monitoring system
How Rsa Identity Governance And Lifecycle Improves Remote Work
Think fast: whats the most critical element of a robust Identity and Access Management strategy?
Ask any security team and Ill wager that their answers will be all over the map. One key element thats sometimes overlooked is password management. But take a closer look and youll likely agree its a critical capability, especially in our current environment of a mostly remote workforce. If organizations want to realize a better business experience, reduce Service Desk costs and enhance ROI from remote work, then they need modern password reset and management functionalities. Here are a few use cases for how the RSA Identity Lifecycle module can help:
Self Service User Onboarding with Password Reset
Lets say theres a new joiner to your organization. RSA Identity Lifecycle can provide one-time onboarding and Identity confirmation of an employee. The new user can quickly and easily enroll their challenge questions from an extensive list of options. As they enroll, the system will email the employee with notifications confirming their completed workflows. RSA Identity Lifecycle can also provide self-service Active Directory password reset from a browser, Windows login or lock-screen. It also can ensure password policy enforcement across the platform, from the strength of passwords to the frequency of changes.
Self Service Password Changes Outside of AD
Learn more about RSA Identity Governance and Lifecycle here.
Tags:
Also Check: How To Apply For Government Subsidized Housing
Rsa Identity Governance And Lifecycle
This lab represents a demo and sandbox environment for RSA’s Identity Governance and Lifecycle suite . RSA IGL is a complete solution for managing digital identities, both inside and outside of the enterprise. The RSA solution covers all aspects of governance and identity lifecycle, including provisioning, entitlement assignment, access reconciliation and approval.
Note: This lab has been newly updated with the latest version of RSA IGL and additional functionality.
Secure Rsa Identity Governance And Lifecycle With Saaspasstwo
Secure access to RSA Identity Governance and Lifecycle with SAASPASS multi-factor authentication and secure single sign-on and integrate it with SAML in no time and with no coding. Log into yourRSA Identity Governance and Lifecycle services securely without ever having to remember passwords on both your computer and mobile with SAASPASS Instant Login .
You can enable RSA Identity Governance and Lifecycle login with SAASPASS secure single sign-on and provide your users the ability to login toRSA Identity Governance and Lifecycle and other SAASPASS integrated apps, all at once.
Enable RSA Identity Governance and Lifecycle login with SAASPASS secure single sign-on and allow users to login to RSA Identity Governance and Lifecycle and other SAASPASS integrated apps, all at once.
Two-step verification and secure single sign-on with SAASPASS will help keep your firmâs RSA Identity Governance and Lifecycle access secure.
Provide the easiest to use and most convenient secure access toRSA Identity Governance and Lifecycle with SAASPASS two-factor authentication and single sign-on with SAML integration. Integration requires no coding and takes a matter of minutes. Log into yourRSA Identity Governance and Lifecycle securely without remembering passwords on both your computer and mobile with SAASPASS Instant Login .
You can integrate SAASPASS with Active Directory. SAASPASS supports SAML and RESTful APIs as well.
Also Check: Data Strategy Vs Data Governance
Rsa Updates Identity Governance And Lifecycle Suite To Ease Compliance
RSA is expanding its Identity Governance and Lifecycle product suite with the new 7.1 update that provides improved analytics, as well as best practice recommendations for deployment and configuration.
RSA Identity Governance and Lifecycle provides organizations with multiple capabilities to help understand and manage identities and access within an enterprise. The need for identity governance is not a new one for enterprises, though with new compliance efforts such as the European Unions General Data Protection Regulation , it has become increasingly important.
RSA Identity Governance and Lifecycle has always provided visibility of who has access to what and the context of that access to help make decisions, James Ducharme, Vice President, Identity Products at RSA, told eWEEK.
Ducharme explained that in previous versions of RSA Identity Governance and Lifecycle, access reviews were enabled by providing business descriptions of the access and giving users an understanding of the risk an access represented. For example, the system could have alerted an administrator that a certain access event was likely a violation of compliance, based on the user entitlements. In the 7.1 release, RSA has now added an analytics layer to the access reviews in a bid to make it easier to use.
By incorporating advanced analytics, RSA has removed the frustrations and given the business user areas of focus, Ducharme said.
Varonis Dataprivilege And Rsa Identity Governance And Lifecycle
Inside Out Security Blog » Data Security » Varonis DataPrivilege and RSA® Identity Governance and Lifecycle
Were thrilled to announce interoperability between Varonis DataPrivilege and RSA® Identity Governance and Lifecycle, with a new Implementation Blueprint. This Implementation Blueprint will help the business to quickly detect security and compliance access risks and amend access entitlement issues associated with unstructured data.
How it Works
The Varonis Data Security Platform helps prepare enterprise data for RSA Identity Governance and Lifecycle by finding data owners, correcting inconsistent permissions, removing global security groups, and simplifying and maintaining permissions structures.
Companies that implement Varonis DataPrivilege interoperability with RSA Identity Governance and Lifecycle benefit from:
- Enhanced visibility and control of unstructured file systems directly within RSA Identity Governance and Lifecycle
- Meeting access control policies by helping to ensure that users have appropriate access permissions
- Reducing attack surfaces and assisting with compliance by limiting access privileges and deactivating stale/orphaned accounts and
- Automating attestations, provisioning and de-provisioning of access permissions.
Learn more
You May Like: Government In America Ap Edition 17th Edition
How Securid Helps
A phased approach
IGA covers a lot of ground, from access reviews to lifecycle management to role-based access control and more. SecurID Governance & Lifecycle offers a phased approach to deployment, in the cloud or on-premises, so you dont have to roll out everything at once.
Automated processes
Spreadsheets and other manual tools for IGA dont cut it when youre dealing with a constantly changing workforce, a growing number of resources and multiple access points. SecurID Governance & Lifecycle replaces slow, inefficient processes with fast, accurate automation.
Access visibility
Limited visibility into access makes effective governance impossible. SecurID Governance & Lifecycle provides the full visibility you need to uncover access anomalies and policy violations, and combines it with advanced analytics to prioritize problem areas for action.
