Why Is Governance Risk And Compliance Important In Business
So now that weve covered the boring stuff, why is Governance, Risk and Compliance important in business? Well, basically it comes down to streamlining and organising the business. Implementing GRC ensure that you are meeting the necessary regulations that you may need to adhere to.
A lot of the larger industries, such as banking, legal, healthcare all need to meet various regulations, implementing GRC within the business helps with this.
Not only this, but you will also realise that 9 times out of 10, you will identify risks, assets and more which you didnt realise you had. This is especially true with regards to more people working from home at the moment.
The biggest mistake most companies try and make when looking at GRC is that they try and do everything in one big bang approach. They then get overwhelmed and stop the project.
What you should do, it piece it out. Be proactive, plan and design your framework, piece out the work and build upon it. Look at the areas of the business, identify the risks within the business, what can be resolved, what can be changed to reduce the risks. Who are going to be responsible for this project?
Ask yourself all the questions before you start and then build a plan to iterate though all the steps and eventually you will have a GRC framework which will help you and the business success and reduce your overall risk.
Virtual Machine Security Updates And Strong Passwords
Ensure policy and processes enable rapid application of security updates to virtual machines.
Attackers constantly scan public cloud IP ranges for open management ports and attempt âeasyâ attacks like common passwords and unpatched vulnerabilities.
Enable Microsoft Defender for Cloudto identify missing security updates & apply them.
Local Admin Password Solution or a third party Privileged Access Management can set strong local admin passwords and just in time access to them.
Integrating Governance Risk And Compliance With The Nist Csf
For leaders looking to integrate their governance, enterprise risk management, and compliance activities, there is another reason to use the NIST CSF as the principled performance standard for compliance: using the NIST portfolio of frameworks and publications integrates all activities of GRC under one banner. As my co-founder discussed in his webinar on harmonizing privacy, risk, and cybersecurity, we can see that the NIST CSF is designed to integrate with the NIST Risk Management Framework and new Privacy Framework. Further, the NIST CSF’s outcome-based approach supports the translation of tactical cybersecurity risk and compliance activities into business outcomes – a critical function for today’s cybersecurity leader.
Also Check: Where To Cash A Government Check For Free
Assign Privileges For Managing The Environment
Grant roles with operational responsibilities in Azure the appropriate permissions based on a clearly documented strategy built from the principle of least privilege and your operational needs.
Providing clear guidance that follows a reference model will reduce risk because by increasing it provides clarity for your technical teams implementing these permissions. This clarity makes it easier to detect and correct human errors like overpermissioning, reducing your overall risk.
Microsoft recommends starting from these Microsoft reference models and adapting to your organization.
Grc Has A Symbiotic Relationship
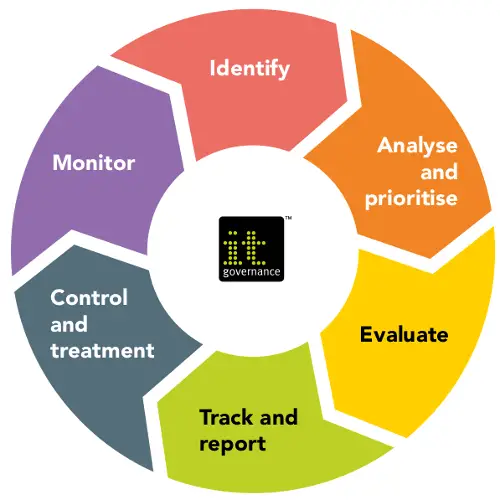
Whilst governance, risk and compliance are often viewed as separate functions, taking a holistic view on these fundamental components demonstrates the symbiotic relationship they share.
Governance ensures that organizational activities are aligned in a way that supports the organizations business goals. Risk that is associated with any organizational activities is identified and addressed in a way that supports an organizations business goals. Compliance allows all organizational activities to be operated in a way that meets the laws and regulations impacting those systems. And all three aspects work together to create an approach which will enable security architecture, engineering, and operations to be aligned with the wider business goals, while effectively managing risk and meeting compliance objectives.
But, how do you scale a GRC program and ensure it is embedded within your organization?
Recommended Reading: Government Contract Specialist Job Description
Policy Review / Development
Policies are critical to the success of a cybersecurity program. CyberClan can provide templates as well as customized policies that are tailored to your specific organization. If you have policies already in place, we can review those policies for any gaps that might expose the organization to risk.
What Is The Need For Sap Grc
With the SAP GRC solution, organizations can supervise and manage regulation, compliance, and risk in business processes. Cybersecurity is not necessarily the focus of this functionality. SAP Governance, Risk, and Compliance is more about taking care of business risks like helping organizations enhance cross-border supply within the limits of international trade management.
You May Like: Talent Management System Federal Government
Discover & Replace Insecure Protocols
Discover and disable the use of legacy insecure protocols SMBv1, LM/NTLMv1, wDigest, Unsigned LDAP Binds, and Weak ciphers in Kerberos.
Authentication protocols are a critical foundation of nearly all security assurances. These older versions can be exploited by attackers with access to your network and are often used extensively on legacy systems on Infrastructure as a Service .
Here are ways to reduce your risk:
-
Discover protocol usage by reviewing logs with Microsoft Sentinelâs Insecure Protocol Dashboard or third party tools
-
Restrict or Disable use of these protocols by following guidance forSMB,NTLM,WDigest
We recommend implementing changes using pilot or other testing method to mitigate risk of operational interruption.
Governance Risk & Compliance Courses
A good cyber governance, risk and compliance programme is fundamental to securing the business-critical assets of an organisation. GRC includes the management of cyber risks for an organisation to achieve their security and compliance objectives.
Notwithstanding existing regulations and compliance, the new UK Telecommunications Bill introduced at the end of 2020 intends to boost the security standards of the UKs telecoms networks, which will now be monitored by Ofcom. Telecoms companies in the UK must follow tougher security rules or face fines of up to 10% of turnover, up to £100,000 per day.
QA’s range of GRC courses include the popular CISM, CISMP, CISA and CRISC certifications, the ISO/IEC 27001 and ISO/IEC 22301 Lead Implementer and Auditor qualifications, EC-Council’s CCISO programme, IAPP’s Certified Information Security Manager and Auditor qualifications, and the NIST NCSP certifications.
You May Like: Government Grants For Veterans With Ptsd
Assess Risk With The Vision Of The Possible
Finally, lets keep in mind the need for something that may seem whimsical, but is essential to cold, hard decision-making: Imagination. Most of us have read about NASAs Apollo 1 tragedy, where three astronauts died in a training exercise. A blue-ribbon commission was assembled to study the cause of the accident and to make recommendations to prevent future occurrences. Frank Borman, at that time one of the senior members of the astronaut corps and a member of the commission, was asked at a Congressional hearing his opinion why this tragedy took place. His succinct answer: A failure of imagination.
His point was well taken. Just because this kind of development had never occurred, considering the possibility of something that seemed so remote never entered the collective minds of NASA. Bormans answer served as a rallying cry from that day forwardto not take anything for granted, however remote its chances or unprecedented it may have been.
In cybersecurity, being imaginative is a core competency to properly understand risk. I encourage you to push your imagination to its boundaries in identifying, evaluating, measuring, and minimizing risk.
Learn more in the four-part series on answering your boards top cybersecurity questions.
Sherry Hunyadi is chief security architect at Chevron.
Get Outside Help To Assess Your Cyber Risk
While Im not necessarily an advocate of outsourcing key IT functions, I am a huge proponent of using experienced and proven outside organizations to evaluate an organizations risk exposure and its impact on the business. For a variety of reasons, organizations often struggle to account for every source of cybersecurity risk in their environment. Maybe they arent collaborative by nature and overlook the input of stakeholders from all corners of the enterprise, or maybe they just havent seen and felt the impact of a cyberattack up close and personal, so they have a hard time accounting for its impact or even its presence.
Having the guidance of a qualified third party is gold, when given the time and ability to dive deep enough into the details to fully understand your companys risks. They lend a perspective that few internal organizations can match. The reality is that an outside opinion counts for a lot with C-suite executives and board members. After all, organizations routinely employ outside auditors to give their opinions on the accuracy and completeness of a companys financial statementsit makes sense that this kind of assessment should be handled similarly.
When framed correctly among all stakeholders, a qualified outside opinion can provide confidence, clarity, and consistency in identifying, assessing, and accounting for cybersecurity risk.
Don’t Miss: Government Grants For Hot Water Heaters
Governance Risk And Compliance Services
Thales provides the following Governance, Risk and Compliance Services:
- Governance: Documentation review of Cyber Security governance including documents such as policies, risk & audit, risk register, training, and security frameworks
- Information Security Management System review to evaluate implementation of security policies and governance and identify risks and gaps against standards. Standards examples: Information Security Forum , ASD Information Security Manual , International Standards Organisation .
- Cyber Strategy & Policy Development: Development of cyber security governance documents such as policy and strategy
Quicklinks
Core Services Reference Permissions
This segment hosts shared services utilized across the organization. These shared services typically include Active Directory Domain Services, DNS/DHCP, System Management Tools hosted on Azure Infrastructure as a Service virtual machines.
Security Visibility across all resources â For security teams, grant read-only access to security attributes for all technical environments. This access level is needed to assess risk factors, identify potential mitigations, and advise organizational stakeholders who accept the risk. SeeSecurity Team Visibility for more details.
Policy management across some or all resources â To monitor and enforce compliance with external regulations, standards, and security policy, assign appropriate permission to those roles. The roles and permissions you choose will depend on the organizational culture and expectations of the policy program. See Microsoft Cloud Adoption Framework for Azure.
Central IT operations across all resources â Grant permissions to the central IT department to create, modify, and delete resources like virtual machines and storage.
Resource Role Permissions â For most core services, administrative privileges required to manage them are granted via the application itself , so no additional Azure resource permissions are required. If your organizational model requires these teams to manage their own VMs, storage, or other Azure resources, you can assign these permissions to those roles.
Don’t Miss: How To Get A Government Job Without A Degree
What Is It Governance Risk And Compliance
Your security team is well aware of the cyber risk faced by your organization. The CISO and other upper management is tasked with making sure your IT organization is aligned with business goals. Various roles throughout your IT organization are responsible for maintaining compliance with laws and regulations governing data and information security. Your third-party relationship manager is responsible for risks associated with your extended enterprise.
Unless your organization has an IT GRC strategy, all of your risk and compliance capabilities will exist in different silos. That can make it difficult for your business to quickly deal with risk and uncertainty within its information technology organization.
Why Compliance Standards Exist
To understand the role that compliance standards play in an integrated risk and compliance program, think of compliance standards as the physiological requirements in Maslow’s hierarchy of needs: the foundational requirements like food, water, and shelter. The function of compliance standards set forth by governing bodies is to ensure that participants in that industry have implemented goodenough security practices to participate in the industry and keep the ecosystem secure. Often, we see standards in highly-regulated industries, places where the failure of these functions is not an option – energy and utilities, banking and finance, defense and aerospace.
Also Check: Government First Time Home Buyer Down Payment Assistance
Governance Risk Management And Compliance
|
|
Governance, risk management and compliance is the term covering an organization’s approach across these three practices: governance, risk management, and compliance. The first scholarly research on GRC was published in 2007 by Scott L. Mitchell, Founder and Chair of OCEG where GRC was formally defined as “the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty and act with integrity.” The research referred to common “keep the company on track” activities conducted in departments such as internal audit, compliance, risk, legal, finance, IT, HR as well as the lines of business, executive suite and the board itself.
Governance Risk Compliance For Cybersecurity For Sap
SAP GRC stands for Governance, Risk, and Compliance and essentially describes the processes of an SAP product and the product itself. SAP GRC experts and related SAP GRC jobs are sought after by many organizations and are therefore in high demand. In this article, we explore the relevance of SAP GRC in the context of the necessary measures for cybersecurity. But before we start, here are a few basics.
Recommended Reading: Federal Government Solar Tax Credit
Maximise Investments And Integrate Discreet Silos Of Information To Enable Strategic Decision
While cyber security is at the forefront of many senior executivesâ minds, IT and security teams must capitalise on this opportunity by demonstrating prudent risk management measures and proactive support of business initiatives.
This may involve cyber transformation initiatives, and KPMGâs Cyber Governance, Risk & Compliance practice is positioned to help.
Our team helps organisations to work with prominent GRC technology vendors to maximise their investments, and to integrate discreet silos of information to enable strategic decision-making.
Increase Automation With Azure Blueprints
Use Azureâs native automation capabilities to increase consistency, compliance, and deployment speed for workloads.
Automation of deployment and maintenance tasks reduces security and compliance risk by limiting opportunity to introduce human errors during manual tasks. This will also allow both IT Operations teams and security teams to shift their focus from repeated manual tasks to higher value tasks like enabling developers and business initiatives, protecting information, and so on.
Utilize the Azure Blueprint service to rapidly and consistently deploy application environments that are compliant with your organizationâs policies and external regulations. Azure Blueprint Serviceautomates deployment of environments including RBAC roles, policies, resources , and more. Azure Blueprints builds on Microsoftâs significant investment into the Azure Resource Manager to standardize resource deployment in Azure and enable resource deployment and governance based on a desired-state approach. You can use built in configurations in Azure Blueprint, make your own, or just use Resource Manager scripts for smaller scope.
Several Security and Compliance Blueprintssamplesare available to use as a starting template.
Don’t Miss: Short Term Disability Government Assistance
Our Grc Service Portfolio
Manage risks effectively with a proactive cybersecurity governance approach that focuses on safeguarding critical business infrastructure while avoiding and reducing the impact of cyber-attacks.
Cybersecurity Governance
Manage risks effectively with a proactive cybersecurity governance approach that focuses on safeguarding critical business infrastructure while avoiding and reducing the impact of cyber-attacks.
Cyber OT
Our Cyber OT solution allows you to ensure safe operations across facilities, maintain control of physical assets, support secure IT/OT convergence, and build robust IoT device safeguards.
Advanced Threat Intelligence
Evolve your security posture address new threats as they arise by introducing automated real-time Advanced Threat Protection into your threat response processes and vulnerability management.
Regulatory Compliance
Collaborate with us and make certain your business adheres to compliance standards in accordance with state, federal, and international laws and regulations for relevant operations.
Insights
How We Can Help
Our Cyber GRC team works alongside our network of sector and domain experts to deliver a range of services across our clientsâ GRC lifecycles, including:
- GRC roadmap and strategy development
- target operating model development
- training material preparation and delivery
- organisational change management
Read Also: How Do I Sign Up For Government Assistance
Cybersecurity Specialization: Governance Risk And Compliance
Acquire the skills to design a system of governance to enforce compliance with laws, regulations, and company policies.
In an ever-changing political and criminal landscape, there is an increasing need for people with specialized and up-to-date knowledge of current cybersecurity laws, regulations, and best practices. The skills gap this need creates in an organization exposes the organization to liability.
Cybersecurity Specialization: Governance, Risk, and Compliance will give you an understanding of the current laws and regulations that drive the creation of a governance system of rules, practices, and processes by which a company is directed and controlled. Understanding the fundamentals of the implementation of a risk management strategy will help your organization achieve compliance through policy management, control creation, and assessment of the effectiveness of controls. In this course, you will learn to set up processes to enforce compliant behaviors in your organization, including the enforcement of a systemic culture of documentation, verification, audits, remediation, follow-through, responsibility, and authority.
The course uses a challenge-based design focusing on what a learner should be able to do at the end of the course and back on the job. The practice opportunities and challenge activities resembleas much as possibletasks the learner would be asked to perform in a real-life situation.
What Is Governance Risk And Compliance
Learn more about cybersecurity governance, risk, and compliance with StickmanCyber.
What is cybersecurity governance, risk, and compliance ?
If you have been digging into cybersecurity, and particularly if you are utilising the NIST cybersecurity framework to guide your companys protocols, you have probably heard the acronym GRC. But what IS GRC, and what do its constituent parts mean for your companys cybersecurity infrastructure?
According to CIO.com,
Governance, risk, and compliance refer to a strategy for managing an organizations overall governance, enterprise risk management and compliance with regulations. Think of GRC as a structured approach to aligning IT with business objectives, while effectively managing risk and meeting compliance requirements.
Even though governance, risk, and compliance are interrelated, and cybersecurity GRC should be considered jointly in your framework, lets discuss each component separately before circling back to GCR overall.
Recommended Reading: What Is Data Governance Model
