What Is Security Governance In Cloud Computing
Cloud Security GovernanceCloud security governancesecuritycloud
. Also know, what is security monitoring in cloud computing?
Monitoring is a critical component of cloud security and management. Typically relying on automated solutions, cloud security monitoring supervises virtual and physical servers to continuously assess and measure data, application, or infrastructure behaviors for potential security threats.
Also Know, how do we provide security in cloud computing? 5 Tips for Securing Your Cloud Computing System
Similarly, you may ask, what are the security benefits of cloud computing?
5 Benefits of a Cloud Computing Security Solution
- Protection against DDoS. Distributed denial of service attacks are on the rise, and a top cloud computing security solution focuses on measures to stop huge amounts of traffic aimed at a company’s cloud servers.
- Data security.
Governance Policy In Cloud
What is governance in cloud computing?
The cloud is vulnerable to various risks developed in the technological environment. There is a need to control these risks. The governance policy provides a regulatory framework to the enterprise, controls, and monitors any deviation from the organizational goals.
The governance policy facilitates risk management. It guides to achieve the business objectives without compromising the shareholders needs. It enables the optimum utilization of the cloud infrastructure.
Governance policy ensures that the management is accountable, effective, and compliant with the framework.
Regulatory requirements and Standards generally address various levels of compliance being subject to assurance. The policy refers to the standards of operating platforms, applications, activities on the operating platform, operating systems, and cloud computing basic service models.
Final Thoughts: Keeping Your Data Safe In The Cloud
As you continue on your cloud adoption journey, especially if you start to rely on the hybrid multi-cloud, your environment will grow more complex. Data security in cloud computing is a critical aspect of minimizing your organizations risks and protecting not only your data but also your brand reputation.
To safeguard against the ever-evolving cloud threats, consider implementing solutions for managing cloud access and entitlements. Additionally, integrate these solutions into your overall IAM strategy for a comprehensive approach to identity management.
A holistic, identity-centered approach ensures that youre enforcing access control consistentlyand applying governance more intelligently whether your data resides on premises or in the cloud. Youre also benefitting from automation and other features that make identity more efficient and save costs.
A leader in identity security for the cloud enterprises, SailPoint provides technology that helps your organization manage cloud risks in todays dynamic, distributed workplace. Learn more about SailPoints cloud governance solution.
Don’t Miss: Money For Homeschooling From The Government
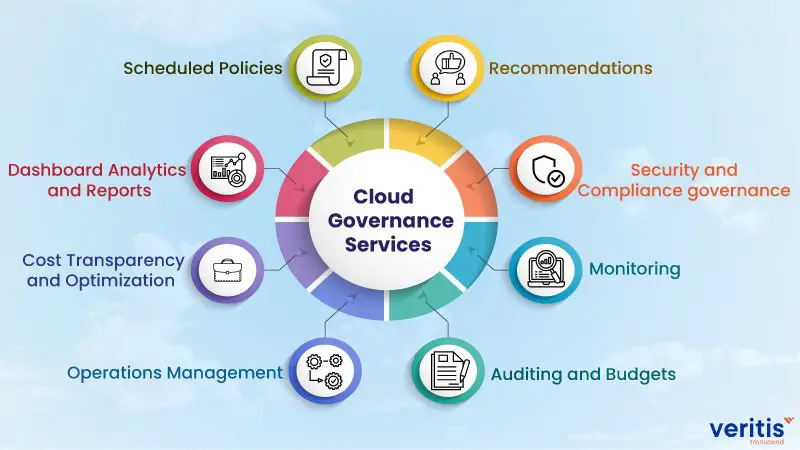
What Is Cloud Governance And Why Is It Important
Cloud governance is a set of practices that help ensure users operate in the cloud in ways that they want, that the operations are efficient, and that the user can monitor and correct operations as needed. A cloud governance framework is not a new set of concepts or practices, but simply the application of existing governance practices to cloud operations.
Human And Civil Rights
This basket of issues focuses on concerns arising from the clouds emergence as a huge depository of data and provider of increasingly essential services individual citizens and groups within society may find their privacy and rights infringed upon, and their data and services disrupted, mined, manipulated, or otherwise leveraged by governmental authorities as well as commercial and criminal actors.
This is yet another issue that predates the emergence and widespread adoption of cloud services, yet is rising in prominence because of the increased use of cloud-enabled technologies. Public concern is rising over who can access user data and for what purposes, alongside increased scrutiny of functions such as facial recognition and location tracking. Cloud services, which enable or empower many of these applications and activities, are consequently in the crosshairs of privacy and human rights advocates . Advocates will likely push at the very least for more robust reporting and transparency requirements surrounding data collection and storage arrangements, as well as guardrails pertaining to the applications they are put to . More ambitiously, they might push for a higher level of access, discretion, and control by individuals over their own data, regardless of where it is located.
Read Also: Best Places To Work In The Federal Government
Cloud Broker & Cloud Agent
A cloud broker is a third-party individual or business that acts as an intermediary between the purchaser of a cloud computing service and the sellers of that service.
A cloud broker is a software application that facilitates the distribution of work between different cloud service providers. This type of cloud broker may also be called a cloud agent.
The broker’s role may simply to save the purchaser time by researching services from different vendors and providing the customer with information about how to use cloud computing to support business goals. Cloud broker also provides the customer with additional services, like deduplication, encryption and transfer of the customer’s data to the cloud.
Principles Of It Governance The Bases For The Cloud Governance#
Every governance starts from principles. Also for cloud governance is necessary to define adequate principles. One good start point is from the ISO/IEC standard 38500 it shows six principles:
- Responsibility: the responsibility of the use of the IT system, should be assigned clearly to individuals o groups
- Strategy: the organization business strategy, from a high level, should consider and define the IT direction, given the base for a correct alignment of activities with the organization need
- Acquisition: the decisions to invest and get IT assets should be taken considering valid reasons and success factors. These factors are not only for managing the ongoing business but they should consider future changes and challenges
- Performance: the IT service demand and capacity both for day by day operation than for new system development should be balanced for ensuring a good level of performance
- Conformance: all the policies and practices, internal or external, relative to the IT use must be formally identified, defined, clearly communicated, implemented and enforced
- Human behaviour: people inside the process, IT policies, practices and decisions, must be always respected.
Nowadays, there are many IT governance frameworks, among which the most important are:
Cloud computing governance is intended as a subset of IT governance and Enterprise Architecture governance. It contains all the unique features that are essential for Cloud governance.
Don’t Miss: Government Help For Single Pregnant Mothers
Protecting The Integrity Of Business Services
The integrity of business services entails two parts:
- Ensuring individual transactions and operations in the cloud function as expected without compromising the confidentiality of those transactions and operations
- Ensuring cloud services are available as expected and as agreed to in SLAs
Confidentiality in the Cloud
What level of confidentiality should a cloud consumer expect when using cloud resources? For example,
- Who will have access to the data transmitted between the cloud and outside data stores?
- Who will determine who will have access to data stored in cloud storage?
- What efforts are made to reduce the risk of inadvertent disclosure of data?
- Under what circumstances will normal confidentiality protections be suspended in order to prevent or investigate malicious activities in the cloud?
It is the responsibility of the governing body to specify policies that answer these and similar questions that will arise.
In one part of a policy, we state that cloud consumers, not administrators, can decide on the level of security they desire for communications. In another part, the policy states that vulnerable software should not be deployed, and this limits cloud consumer choices. It is not unusual for complex policies to lead to seemingly contradictory indications. In these situations, one part of the policy has to take precedence over the other. In this example, protecting the cloud resources and its users is worth constraining the options of users.
Key Principles Of Cloud Computing
Three key principles of cloud computing are i) abstraction, ii) automation and iii) elasticity:
Abstraction
IT providers have tried to standardize their operations so they can concentrate on optimizing their IT. Cloud computing has found a way to break out of this as cloud gives a few basic but well-defined services.
Now the burden of managing the software services falls onto the developer or user. The key point is that well-defined abstraction layers between clouds and developers or users acts as grease, that lets both side to operate efficiently and completely independent of each other. There are three layers of abstraction in clouds, they are:
i)Application as a Service , ii) Platform as a Service and iii) Infrastructure as a Service .
Automation
Automation in the cloud means that the developers or users have complete automatic control over their resources. There is no human interaction, even from a developer or user perspective. In this environment when the user needs more servers, the load balancer intimates the cloud how many more to be provided. No need to wait for someone to unpack and cable your machine, no need to wait for your IT department to find the time to install. Everything is automatic.
Elasticity
Using the elasticity, peoples can easily scale up and scale down according to their daily usage.
Also Check: How To Get Free Grant Money From The Government
Principles Of Cloud Computing Governance
From a high level, the governance goal is to ensure that we are doing the right things in the right way. The questions we are trying to ask are the following:
- Are we doing the right thing?
- Are we doing it in the right way?
- How we can understand it?
Cloud computing governance its a comprehensive view of IT governance focused on responsibility, the definitions of the right decision and the balance between benefit/value. Risk and resources inside a Cloud ecosystem.The governance helps us to ensure that every expense relative to the Cloud are aligned with business objectives, it promotes data integrity, foster technology innovation and mitigate the risk of data loss or not compliance.
We can say that Cloud governance its an extension of IT governance, something we need to integrate into the existing one inside the organization and not replace.
We need to distingue between governance and management because sometimes we can confuse them. Governance defines the strategic direction and establishes an enabling system inside the organization. Management, use the governance enabling system to put in place the strategic direction of the governance.
Reasons Why Cloud Governance Is A Challenge: Should We Eradicate Shadow It
Another day, another report bemoaning shadow IT for cloud computing. SafeNets Challenges of Cloud Information Governance study, conducted by the Ponemon Institute, is the latest to put the blame of compromising data at the door of unapproved IT activity.
Shadow IT, which involves employees bypassing company policy on website and technology usage, has meant cloud security is stormy, according to the report. More than half of the 1,864 IT and IT security practitioners surveyed admitted they were not confident that IT knows all the cloud computing services in use at their company.
Respondents added that payment information was the data that presented the greatest security risk, ahead of customer information , consumer data and email . Payment info, however, was the least likely to be stored in the cloud, probably as a result of this risk.
Part of the problem for IT managers is that conventional security methods are difficult to enforce with cloud apps and products. 71% of respondents agreed with that statement, while around half believe its more difficult to control or restrict end-user access. Similarly, 61% said cloud increases the compliance risk, compared to only 8% who thinks it goes down.
You May Like: Cash For Clunkers Government Program
Challenges Of Cloud Governance
1) The complexity of numerous issues:
There is a combination of various issues that create complexities leading to inconsistencies. These issues get incorporate with the further conflicts in different regulatory interests and approaches.
2) Law enforcement:
The unimpeded access to the cloud is required by various sectors like military, security, and intelligence agencies to give protection against malicious threats, surveillance, and conduct cyber operations. However, this may conflict with standards and requirements implemented for security to cloud operations.
The above challenges are easily tackled by cloud governance.
3) Accountability:
The lack of control over employees and services creates problems relating to design, implementation, testing, and deployment. The organization gains computational resources as capital expenditures. These actions require monitoring by the organization under cloud governance.
Cloud Governance And It
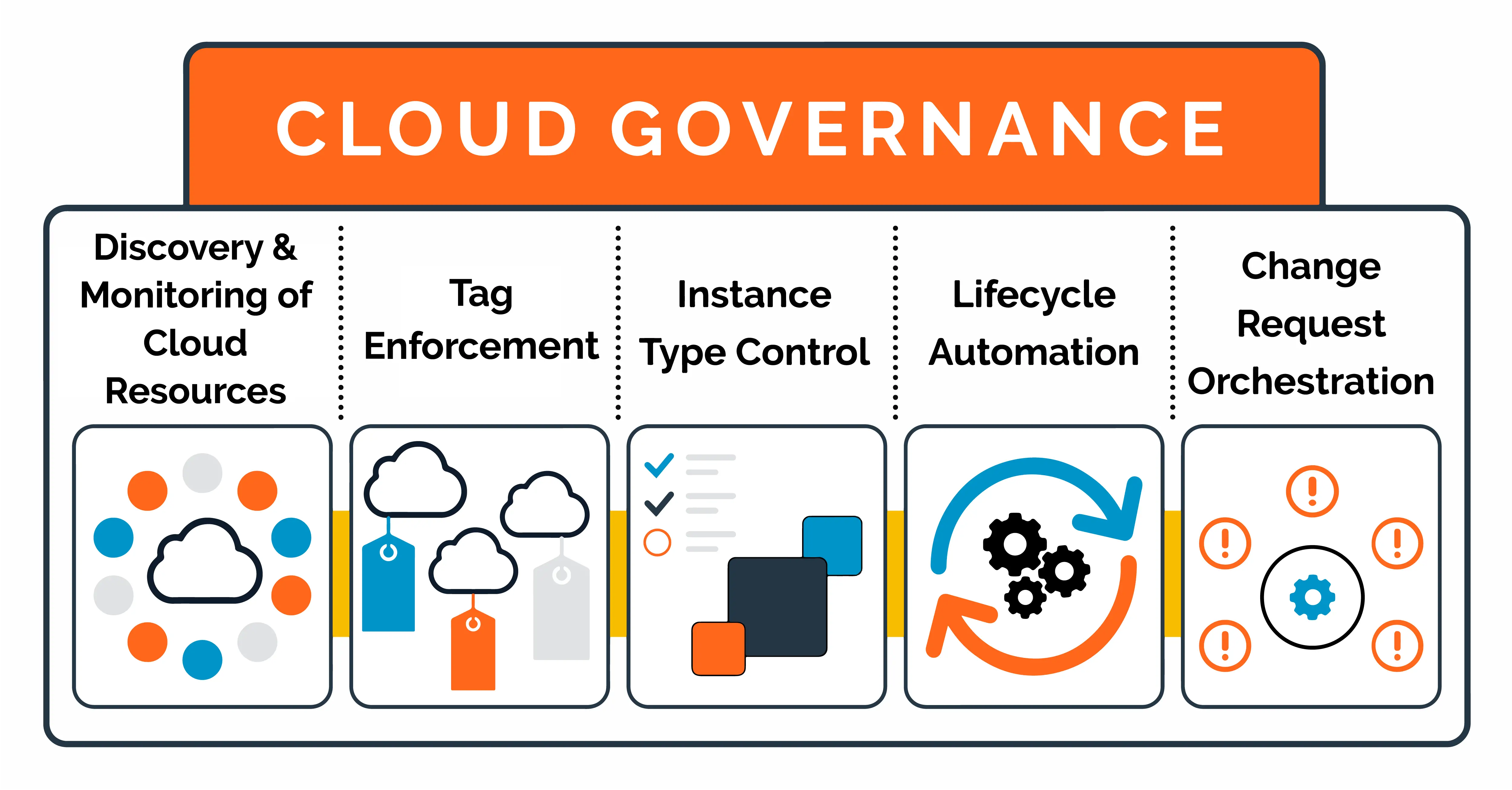
Cloud computing offers big efficiency gains and cost advantages for customers, but introducing a cloud computing strategy isnt a simple operation. This is where cloud governance comes in: the process of managing multiple cloud computing services for simplicity, integration, and cost control.
Cloud governance manages IT processes to receive maximum value from cloud computing investments. Although establishing cloud governance takes time and resources at the beginning, it should deliver significant cost savings wicth management processes and frameworks for cloud computing IT spend.
Cloud governance is a business-wide initiative because it involves compliance officers, risk managers, and senior executives as well as IT. However, cloud governance is closely related to IT, who is responsible for cloud computing.
Lets look at the COBIT model, which publishes five essential process areas both business-wide and for specific stakeholders including IT. They list ITs five process areas as strategic alignment, delivering value, managing resources, managing risk, and measuring performance.
Don’t Miss: How To Do Government Contracting
Using Automation To Avoid The Loss Of Governance In Cloud Computing
Whether your business is in the process of preparing to migrate workloads to the cloud, or has already adopted the cloud by accident, its important to note that you cant have one governance policy for on-premises operations and a second governance policy for cloud operations. A unified governance policy is necessary in order to maintain the four key elements of governance and achieve the maximum benefit from migrating workloads to the cloud.
A second point to note is that, in the cloud, there are too many moving parts to manually monitor compliance with a unified governance policy. Users can launch assets with the click of a mouse and, although they may be doing what they think is best to get the job done, it makes it very difficult to manage costs, performance, and security effectively. For this reason, policy-driven automation is most frequently used to avoid the loss of governance in cloud computing.
We Are Pragmatic About What The Role Of Processes Are And What Impact They Can Have In An Organization:
- We will examine all current processes
- We will perform a gap analysis
- Process is not put in place a s red-tape but to truly improve the underlying services
- Define pragmatic, actionable and tailored roadmap for individual process that will really serve each organization and improve the offerings to end-client of IT services
You May Like: How To Make Money From Government Contracts
Security In The Cloud
Key considerations for longterm planning for security in the cloud are similar to those for other aspects of enterprise security:
- Identity management
- Vulnerability assessments
- Patching and image management
These are not fundamentally different from what needs to be done in other IT environments but, as is so often the case, different implementations of similar services and functionality bring with them varying dependencies and maintenance requirements.
Real Life Ghosts Of Cloud Computing
Here we have discussed some real life ghosts of cloud computing.
Data Security concern
When we talk about the security concern of the cloud technology, then a lot of questions remain unanswered. Multiple serious threats like virus attack and hacking of the clients site are the biggest cloud computing data security issues. Entrepreneurs have to think on these issues before adopting cloud computing technology for their business. Since you are transferring your companys important details to a third party so it is important to ensure yourself about the manageability and security system of the cloud.
Selecting the perfect cloud set-up
Choosing the appropriate cloud mechanism as per the needs of your business is very necessary. There are three types of clouds configuration such as public, private, and hybrid. The main secret behind successful implementation of the cloud is picking up the right cloud. If you are not selecting the right cloud then maybe you have to face some serious hazards. Some companies having vast data so they prefer private clouds while small organisations usually use public clouds. A few companies like to go for a balanced approach with hybrid clouds. Choose a cloud computing consulting service which is aware and clearly disclose the terms and conditions regarding cloud implementation and data security.
Real time monitoring requirements
Resolving the stress
Reliability on new technology
Cultural obstacles
You May Like: List Of Government Grants For Individuals In Usa
Poor Planning Governance Raise Data Breach Risks
Poor governance and infrastructure planning raise the risk of a data breach that is extremely costly financially and in terms of market reputation, putting C-level executives jobs at risk. According to fugue survey, 47 percent of respondents believe a CEO should be terminated after a data breach. CIOs should be on the chopping block, according to 32 percent of respondents. The vice president in charge of cloud systems should get the ax according to 31 percent while 11 percent of respondents believe corporate board members should lose their positions.
Safeguards For Data Security In Cloud Computing
Data security in the cloud starts with identity governance. You need a comprehensive, consolidated view of data access across your on-premises and cloud platforms and workloads. Identity governance provides:
- Visibilitythe lack of visibility results in ineffective access control, increasing both your risks and costs.
- Federated accessthis eliminates manual maintenance of separate identities by leveraging your Active Directory or other system of record.
- Monitoringyou need a way to determine if the access to cloud data is authorized and appropriate.
Governance best practices include automating processes to reduce the burden on your IT team, as well as auditing your security tools routinely to ensure continuous risk mitigation as your environment evolves.
In addition to governance, here are some other recommended data security safeguards for cloud computing:
Deploy encryption. Ensure that sensitive and critical data, such as PII and intellectual property, is encrypted both in transit and at rest. Not all vendors offer encryption, and you should consider implementing a third-party encryption solution for added protection.
Back up the data. While vendors have their own backup procedures, its essential to back up your cloud data locally as well. Use the 3-2-1 rule for data backup: Keep at least three copies, store them on at least two different media, and keep at least one backup offsite .
Don’t Miss: Federal Government Jobs In Virginia
