Mining Social Media Data For Policing The Ethical Way
By Chris Bousquet April 26, 2018
INTRODUCTION
Social media posts are full of data that, when made accessible to governments, can make interventions quicker, more effective, and more representative. From pictures of emergency conditions to posts about crimes in progress, users constantly inundate Facebook, Instagram, Twitter, and other platforms with posts that may contain rich and timely information about events relevant to public safety. Using social media mining that leverages advances in natural language processing and machine learning to pull useful data from text and images, cities can transform these social posts into data points ripe for analysis.
Policing is one area that seems an obvious fit for social mining initiatives. Social monitoring has great potential to make policing more proactive, targeting incidents before they escalate into tragedies. By deploying software that can sift through mountains of posts and identify relevant keywords, governments can track posts indicative of danger or criminal activity and intervene.
Yet even without accessing back-end data, police departments can mine readily available information from user news feeds. Even public feeds are full of data that can make policing more effective, from posts about crimes in progress to damning evidence offered freely by criminals and even live videos of crimes.
COLLECTING VALUABLE INFORMATION WHILE MAINTAINING PRIVACYRESPECTING FREE SPEECHPREDICTING WITHOUT PREJUDICE
Governance And Compliance Are Not Ethics
Compliance, therefore, is critical to your organization and especially your data mining efforts. But simply complying with a checklist of rules may not be enough if you don’t include ethics in data mining as a priority and pay it more than lip service. Enron had a code of ethics practices 64 pages long, but I wonder if any company today would aspire to its ethical standards.
My friends at Castlebridge — an Irish consultancy specializing in governance and ethics — like to quote social work pioneer Jane Addams: “Action indeed is the sole medium of expression for ethics.” In other words, corporate ethics will not be found in your company’s procedures, policies or legal compliance. Nor will you find ethics in your corporate motto.
While software tools can help with formal issues, ethics in data mining requires a more human touch.
For many years, Google’s unofficial motto was “Don’t be evil.” However, ethics is more about what you do. In 2015, Google’s newly formed parent company, Alphabet, adopted “Do the right thing” as its new motto to form the opening of its code of conduct.
While software tools can help with formal issues, ethics in data mining requires a more human touch. The Enron case should warn us that codes of conduct by themselves will not suffice. We need to align the motivations of data users with good practices, such as fairness, equity, transparency and benefit.
Next Steps
Navigating The Gray Areas
Unfortunately, there’s no simple black-and-white answer to the question of what social media data can be used. “It’s incredibly contextual,” noted Omer Tene, vice president and chief knowledge officer at the International Association of Privacy Professionals. “It depends on the location, applicable laws, the context of the platform and the rules and the kind of data.”
Data practitioners not only need to be concerned about the data they collect, but also the primary as well as the secondary uses of that data and from whom the data is collected.
“There are a lot of aggregators out there scraping social media sites and the information they collect, they resell or they buy,” Sreewastav explained. “That data gets aggregated, and enterprises get that second or thirdhand data, so you’re not only protecting the integrity of the data you’re acquiring, you have to understand who you’re buying it from and what their level of compliance is.”
Gartner predicted that, by next year, “the backup and archiving of personal data will represent the largest privacy risk for 70% of organizations,” compared to just 10% in 2018. “Over the next two years,” Gartner added in a report on privacy issues, “organizations that don’t revise data retention policies to reduce the overall data held, and by extension the data that is backed up, will face a huge sanction risk for noncompliance as well as the impacts associated with an eventual data breach.”
You May Like: Free Government Grants For New Businesses
Recent And Prospective Legislation
During her presentation, Mary Baily asserted that implementation of effective access and confidentiality policies requires carefully constructed social mechanisms. Paramount among these is a consistent national legal framework, designed to indicate to both data producers and users what standards are appropriate and to aid in imposing sanctions for misuse. The need for such a framework, which does not now exist, is a recurrent theme in the literature on privacy and data use. Confirming Baily’s assessment, Donna Eden provided an overview of recent and prospective legislative developments. Speaking primarily about health data, Eden observed that coordinated federal privacy legislation to protect health records does not yet exist. This is somewhat of a surprise, given that Congress has been working to enact
Suggested Citation:Improving Access to and Confidentiality of Research Data: Report of a Workshop
comprehensive privacy legislation in health and other areas for many years. In fact, in the Health Insurance Portability and Accountability Act of 1996, Congress set an August 1999 deadline for the enactment of privacy legislation to protect health records, and provided that if that deadline were not met, the Secretary of Health and Human Services would be required to issue regulations to protect the privacy of certain health data.
Suggested Citation:Improving Access to and Confidentiality of Research Data: Report of a WorkshopSuggested Citation:
What Is Data Mining And How Does It Work
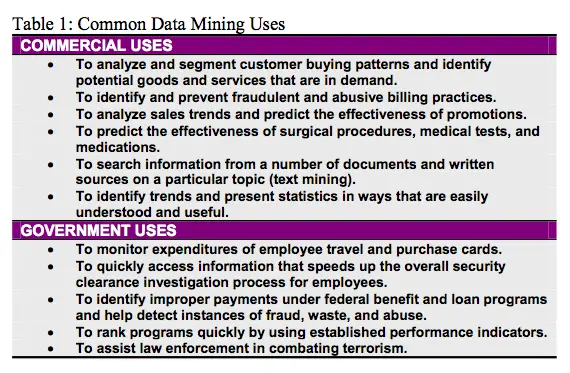
Data mining is a process used by companies and data scientists to extract information and find trends in raw data. The data used in mining can come from multiple sources such as online surveys, data collected through cookies, or public records.
But not all data sets are equally beneficial. The data needs to be accurate and without bias, consistent with as few gaps as possible, and large in volume to get authentic results.
Because you work with raw data instead of pre-made statistics, data mining can be a versatile tool. You can process the same data set multiple times in different ways, looking for various trends. That makes the insights from a single data set virtually unlimited.
Theres no clear-cut data mining technique, as extracting underlying trends requires a lot of creativity and skill. But the process can be broken down into five main steps.
Don’t Miss: Government Says Aliens Are Real
Data Protection Laws In India
Data Protection refers to the set of privacy laws, policies andprocedures that aim to minimise intrusion into one’s privacycaused by the collection, storage and dissemination of personaldata. Personal data generally refers to the information or datawhich relate to a person who can be identified from thatinformation or data whether collected by any Government or anyprivate organization or an agency.
The Constitution of India does not patently grant thefundamental right to privacy. However, the courts have read theright to privacy into the other existing fundamental rights, ie,freedom of speech and expression under Art 19 and right tolife and personal liberty under Art 21 of the Constitution ofIndia. However, these Fundamental Rights under the Constitution ofIndia are subject to reasonable restrictions given under Art19 of the Constitution that may be imposed by the State.Recently, in the landmark case of Justice K S Puttaswamy & Anr. vs. Union of India and Ors., the constitution bench ofthe Hon’ble Supreme Court has held Right to Privacy as afundamental right, subject to certain reasonable restrictions.
India presently does not have any express legislation governingdata protection or privacy. However, the relevant laws in Indiadealing with data protection are the Information Technology Act,2000 and the Contract Act, 1872. A codified law on thesubject of data protection is likely to be introduced in India inthe near future.
Relevant Authorities And Legislation
1.1 What regulates mining law?
The US legal system consists of many levels of codified and uncodified federal, state, and local laws. The Governments regulatory authority at each level may originate from constitutions, statutes, administrative regulations or ordinances, and judicial common law. The US Constitution and federal laws are the supreme law of the land, generally pre-empting conflicting state and local laws. In many legal areas, the different authorities have concurrent jurisdiction, requiring regulated entities to comply with multiple levels of regulation. Mining on federal lands, for example, is generally subject to multiple layers of concurrent federal, state, and local statutes and administrative regulations. Increasingly, the executive branch of the federal Government has made use of Presidential Executive Orders to impact mining policy and procedure.
1.2 Which Government body/ies administer the mining industry?
1.3 Describe any other sources of law affecting the mining industry.
The National Environmental Policy Act , 42 U.S.C. §§ 4321-4370m-12, requires federal agencies to prepare an environmental impact statement for all major federal actions significantly affecting the quality of the human environment. Mining operations on federal lands or with a federal nexus generally will involve an EIS or a less intensive environmental assessment examining environmental impacts. The NEPA process involves consideration of other substantive environmental statutes.
Read Also: State Of Ohio Government Nursing Jobs
In The Ethical Mining And Analysis Of Data Governance Compliance And Ethics Are Mistakenly Taken As One In The Same Data Managers Need To Be Aware Of The Critical Differences
- Donald Farmer,TreeHive Strategy
There’s a maze of technical terms to navigate in the world of data today — business intelligence, data analytics, data science, data mining. I often tell CIOs and other technology leaders that, in most cases, we could use an older, more inclusive term — . However new, our technologies support us in making better decisions that result in better business outcomes.
But when mining and using customer data, making good decisions may not suffice. Socially, commercially and legally, we see increasing value placed on the ethics of our data mining systems and processes. And along with the talk of ethics in data mining and analytics, we face heightened demands for governance and compliance.
Yet it’s important that analytics teams know how ethics, governance and compliance differ, especially because ethics in data mining can be inadvertently overlooked in the rush for more objective standards.
Registration Formalities And Prior Approval
6.1 Is there a legal obligation on businesses to register with or notify the data protection authority in respect of its processing activities?
Both Vermont and California require data brokers to register with the state attorney general. The Vermont requirement, which went into effect in 2019, defines a data broker to include entities that knowingly collect and sell or license to third parties the personal information of a consumer with whom the business does not have a direct relationship . Californias requirement went into effect in 2020, and similarly applies to the knowing collection and sale of personal information regarding consumers with which the business does not have a direct relationship .
6.2 If such registration/notification is needed, must it be specific or can it be general ?
6.3 On what basis are registrations/notifications made ?
Data broker registrations are made on a per legal entity basis.
6.4 Who must register with/notify the data protection authority ?
Within the states for which it applies, registrations are required based on the business falling within the definition of a data broker pursuant to state law. Generally, a data broker is defined as a business that knowingly collects and sells the personal information of a consumer with whom the business does not have a direct relationship.
6.5 What information must be included in the registration/notification ?
See question 6.2 above.
6.7 What is the fee per registration/notification ?
Read Also: What Is The Return On Government Bonds
Ethical And Legal Requirements Associated With Data Dissemination
Session II of the workshop was structured to provide an overview of the ethical and legal issues related to data dissemination. Mary Ann Baily, Institute for Ethics, American Medical Association, presented a paper, commissioned for the workshop, titled Regulating Access to Research Data Files: Ethical Issues. Donna Eden, Office of the General Counsel, U.S. Department of Health and Human Services, outlined her assessment of recent and prospective legislative developments. Finally, Thomas Puglisi of the Office for Protection from Research Risks , National Institutes of Health, provided an overview of the role of institutional research boards .
Social Media Provides A Fertile Landscape Of Information And Insight Into Consumer Behavior But Collecting And Analyzing That Data Carries All Sorts Of Privacy Pitfalls
Social media data can help improve a company’s marketing ROI by targeting consumer behavior, demographics, personas, sentiment and social trends, but the road to fulfilling these critical goals is fraught with potential privacy hazards.
Individual social media profiles tend to include personally identifiable information and other sensitive data, making it imperative that data scientists understand what they can and can’t useand for what purpose. Issues surrounding social media data privacy can vary depending on the type of data collected and how it’s used. Applicable laws and regulations, social media platform contracts, the data subject’s expectations of privacy, the use case and the organization’s values, all factor into decisions on collecting and using social media data.
“We ask clients three questions: What is the purpose for processing or using the data? What is your legal basis? Does it feel creepy?” said Rita Zurbrigg, an analyst at Info-Tech Research Group.
Not all social media data is equally usable, so it shouldn’t be collected or used as if it were.
“Understanding what kind of data meets the depth of protection is critical,” said Kiran Sreewastav, vice president of data management and architecture at Cognetik, a data science and analytics company based in Cary, N.C. ” the different tiers of sensitive data and personal data and then build your practices around that.”
You May Like: Government Program For Buying House
Appointment Of A Data Protection Officer
7.1 Is the appointment of a Data Protection Officer mandatory or optional? If the appointment of a Data Protection Officer is only mandatory in some circumstances, please identify those circumstances.
Appointment of a Data Protection Officer is not required under U.S. law, but certain statutes require the appointment or designation of an individual or individuals who are charged with compliance with the privacy and data security requirements under the statute. These include the GLBA, HIPAA, and the Massachusetts Data Security Regulation, for example.
7.2 What are the sanctions for failing to appoint a Data Protection Officer where required?
Potential sanctions are statute/regulator-specific.
7.3 Is the Data Protection Officer protected from disciplinary measures, or other employment consequences, in respect of his or her role as a Data Protection Officer?
This is not applicable in our jurisdiction.
7.4 Can a business appoint a single Data Protection Officer to cover multiple entities?
This is not applicable in our jurisdiction.
7.5 Please describe any specific qualifications for the Data Protection Officer required by law.
This is not applicable in our jurisdiction.
7.6 What are the responsibilities of the Data Protection Officer as required by law or best practice?
This is not applicable in our jurisdiction.
7.7 Must the appointment of a Data Protection Officer be registered/notified to the relevant data protection authority?
This is not applicable in our jurisdiction.
The United States And Data Mining Regulations

According to the John Marshall Journal of Information Technology and Privacy Law, the Federal Trade Commission is currently in charge of regulating data. The FTC and state laws have tried to protect consumer privacy, but many of these regulations are ineffective.
Right now, the FTC uses a framework based on simplified choice, privacy by design and greater transparency. During the Obama administration, it used a Privacy Bill of Rights to increase individual control, security, accuracy, and transparency. The goal was to help consumers have extra control about what information companies could collect and how the information was used.
Privacy by design laws mean that companies should implement policies that ensure consumer privacy. Meanwhile, simplified choice requires companies to give consumers the choice about whether their data is collected. With greater transparency rules, consumers are supposed to get simple, short privacy policies that they can actually understand.
Consumers often think of data mining as something that occurs when they use an online app or website. In reality, the consumers information is collected any time they use their credit card at the store. Companies collect personal information from the credit card and can sell it to third parties. Unfortunately, privacy protections are still in their infancy, so consumers may continue to face unwanted data mining.
Don’t Miss: Hotels On Government Blvd Mobile Al
Legal And Privacy Concerns Of Data Mining
In data mining, the privacy and legal issues that may result are the main keys to the growing conflicts. The ways in which data mining can be used is raising questions regarding privacy. Every year the government and corporate entities gather enormous amounts of information about customers, storing it in data warehouses. Part of the concern is that once data is collected and stored in a data warehouse, who will have access to this information? Oftentimes a consumer may not be aware that the information collected about him/her is not just shared with who collected the information. With the technologies that are available today, data mining can be used to extract data from the data warehouses, finding different information and relationships about customers and making connections based on this extraction, which might put customers information and privacy at risk. Data mining necessitates data arrangements that can cover consumers information, which may compromise confidentiality and privacy. One way for this to happen is through data aggregation where data is accumulated from different sources and placed together so that they can be analyzed.
Laws And Legal Issues With Data Mining
With the concept of data mining only being introduced in the 1990s and businesses only investing and utilizing it heavily within the last 15 years, it is not surprising that there are many questions that remain unanswered regarding the laws and regulations that apply to data mining. The laws that have had the most intersection with data mining are the Electronic Communications Privacy Act of 1986, the Fair Credit Reporting Act of 1970, and the Family Educational Rights and Privacy Act of 1974. While these laws have been used to answer some questions related to data mining, they were written at a time when people did not know that technology would grow at such an exponential rate. They did not know or foresee many of the issues that now need clear, unequivocal answers. New legislation and regulations are needed to address the array of issues currently being faced. The Federal Trade Commission has also weighed in on the issue, offering guidance and some oversight.
Electronic Communications Privacy Act “ECPA”
Fair Credit Reporting Act “FCRA”
Family Educational Rights and Privacy Act “FERPA” and Google:
The Federal Trade Commission:
You May Like: Government Funding For Small Business Owners
