Definitions Perspectives And Models
The lens provided in the introduction of this paper demonstrates the change in the ISG contextual boundaries towards embedded business and inter-organisational ISG approaches. In this explorative section, the aim is to structure the current body of knowledge on the ISG concept and to examine its underlying definitions, perspectives and models.
Governance And Security Operations
Security governance and security operations work together to provide complete visibility. They ensure that lessons learned from real world incidents are integrated into architecture, standards, and policy.
Governance and security operations provide complementary types of visibility.
- Security operations provide insight into the immediate risk of active attacks.
- Security governance provides a broad or long view of risk from potential future attacks and attack vectors.
The security architects within the governance function help identify lessons learned from incidents. For example, the root cause of major incidents. They capture the lessons into your organization’s standards to ensure consistent application across the enterprise.
For more information, see Security integration.
Note
Some organizations place monitoring of security posture in security operations. We recommend having this monitoring in governance. This placement creates a better relationship with the IT engineering and operations teams that apply the standards. This relationship often results in higher quality communications and better security outcomes. Otherwise, you have a governance team that never sees the real world impact of their standards.
Understand The Difference Between What Can And Should Be Shared
A good program must continually assess and review who needs access to what types of information. Privacy and security teams should work with their IT counterparts to automate controls around enterprise systems to make it easier for employees to do the right than wrong or simply neglect the consequences of their actions. Once youve implemented your plan, be sure that you maintain regular and ongoing assessments.
Want more tips on information governance and risk management? !
Recommended Reading: Student Loan Forgiveness For Government Employees
How To Govern Information Security
The ISO position is evolving from a primary technical position to one that combines both technical and managerial functions. Today IT security is an institutional imperative with critical policy and operational aspects with attention dedicated from the CIO, general counsel, internal auditor and executive leadership. While the list of tasks for the ISO continues to grow, unfortunately the authority and challenges to that authority of the role are often institutionally handled with senior administrators, legal counsel or law enforcement. The ISO must rely on institutional policy and legal compliance in order to effectively control IT security. Building a relationship and consensus with many groups on campus is a key to having security policy compliance. One progressive step is the growing recognition of department managers to accept responsibility for their data and its protection. Shifting the role of the ISO from compliance dictator to offering assistance realizes the concept of security as a service .
Governance frameworks, COBIT, ITIL, the ISO 17799 information security management standard, and the ISO 9000 quality management standard – are used in the IT governance processes and structures. ITIL and ISO 17799 are the most common frameworks in use.
Organizational Structure
IT governance-related committees include :
Governance structures depend on desired outcomes
CERT GES desribes structure based on desired outcomes.
Information Security Governance Structures
Policy
What Is Governance Risk And Compliance
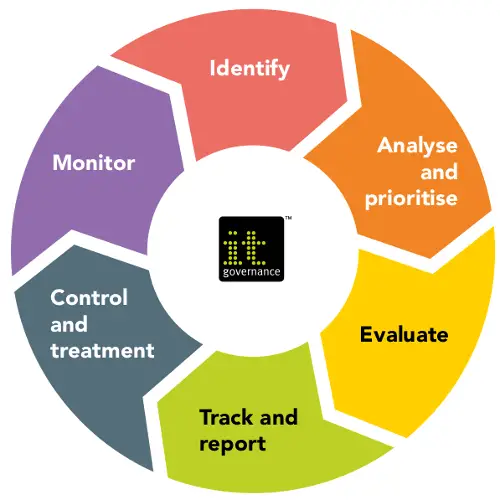
What is cybersecurity governance, risk, and compliance ?
If you have been digging into cybersecurity, and particularly if you are utilising the NIST cybersecurity framework to guide your companys protocols, you have probably heard the acronym GRC. But what IS GRC, and what do its constituent parts mean for your companys cybersecurity infrastructure?
According to CIO.com,
Governance, risk, and compliance refer to a strategy for managing an organizations overall governance, enterprise risk management and compliance with regulations. Think of GRC as a structured approach to aligning IT with business objectives, while effectively managing risk and meeting compliance requirements.
Even though governance, risk, and compliance are interrelated, and cybersecurity GRC should be considered jointly in your framework, lets discuss each component separately before circling back to GCR overall.
Recommended Reading: Environmental Social And Governance Esg Factors
Risk Assurance And Risk Maturity
The next way in which effective information governance supports risk management is assurance. Risk assurance is simply evidence that your risk approach is both appropriate and effective. You need high-quality information to show that risk management is working well. For example:
- People who oversee/authorise your project need to be assured that you are managing your risks well.
- Auditors/the Audit Committee/trustees need to be assured that corporate-level risk management is working.
Because risk assurance is entirely evidence-based you must be able to provide high-quality information and manage it effectively to support this crucial element of risk management.
Finally, all risk management activities can be assessed for their maturity. Risk management is an ongoing cycle, and the collation and analysis of information to define, evaluate and manage risks should be continuous. To be effective risk management must be:
Think About How You Are Going To Use And Maintain This Data
Here you should consider inappropriate access, ensure that the data subjects choices are properly honored, address concerns around a potential new use or even misuse, consider how to address concerns around breach, and also ensure that you are properly retaining the data for records management purposes.
Read Also: Government Help For House Repairs
Information Security Starting At The Top
The Board of Directors of an organisation is ultimately responsible for the protection of the company assets . They need to ensure correct governance of the organisation is being deployed with a risk management process in place and an effective system of internal controls in place to support this risk management process. There are many legal obligations for which the Board and its directors are responsible and there are stiff penalties for failing to meet these legal
What Is Information Security Governance
Information security governance is a process of making sure the security policies. Also, standards and guidelines.
To ensure optimal security, an organization must follow a specific set of rules. Also, guidelines.
A combination of policies, standards, and guidelines make up. It is the information security governance structure.
When we talk about information security governance, we are referring to standards and policies. It guides the organization in how it manages its information assets.
Why? It is in order to protect its people, systems, and intellectual property.
Read Also: How To Make A Resume For A Government Job
Organizations Need Cybersecurity Governance Programs That Make Every Employee Aware Of The Cybersecurity Mitigation Efforts Required To Reduce Cyber
- Pam NigroGuest Contributor
In an increasingly challenging threat landscape, many organizations struggle with developing and implementing effective cybersecurity governance.
The “Managing Cybersecurity Risk: A Crisis of Confidence” infographic by the CMMI Institute and ISACA stated: “While enterprise leaders recognize that mature cybersecurity is essential to thriving in today’s digital economy, they often lack the insights and data to have peace of mind that their organizations are efficiently and effectively managing cyber risk.”
Indeed, damages from cybercrime are projected to cost the world $7 trillion in 2022, according to the “Boardroom Cybersecurity 2022 Report” from Cybersecurity Ventures. As a result, “board members and chief executives are more interested in cybersecurity now than ever before,” the report stated, adding that the time is ripe for turning awareness into action.
How, then, can board leaders have confidence that their organizations are prepared against cyber attacks? The first order of business for most organizations is to enable a strong cybersecurity governance program.
This article is part of
The Importance Of Implementing
Is it important to implement information security governance and risk management? Yes, it is important to implement it.
Why? Because you need to put the right processes in place. To help you manage information security risks. So this will help you achieve your information security goals.
Also, it helps you achieve better business results. Moreover, It will help you comply with industry and regulatory requirements.
Then, it will help you manage information security more effectively. Furthermore, governance and risk management.
It helps the organization move to a more comprehensive approach to information security governance. So it can benefit from a holistic view of the organizations risk exposure.
This leads to better risk management decisions. In addition, this leads to better business outcomes.
Moreover, it will help increase the effectiveness of your information security programs. Also, help increase the effectiveness and efficiency of your information security teams.
This will help improve your ability to make decisions about information security investments. Moreover, improve your ability to make decisions about information security resources and staffing levels.
Don’t Miss: Political Science And Government Colleges
The Information Security Governance And Risk Management
What are information security governance and risk management? Information security governance and risk management is a set of processes.
Also, activities aimed at protecting confidentiality and integrity. Moreover, the availability of the organizations information assets.
It is a subset of governance and risk management. Which focuses on the three main dimensions of risk from the following:
So this approach to information security builds upon a framework. That also encompasses four main pillars from the following:
Therefore, the goal of information security governance and risk management. It is to manage information security risks so that they are acceptable to the business.
Some Thoughts For The Future
The insider threat is a problem that has been growing and is likely to continue to grow. Organisations need to be fully mindful of this situation and implement company-wide management framework to ensure that the protection of their information assets measures up to the risks they are facing.
Insecurity and security posed by the insider threat are related in the sense that they are two sides of the same coin a coin representing uncertainty. How much security we have versus how much insecurity
Edward Humphreys is a consultant, University visiting professor and lecturer, and a prolific writer on information security management. He is the Chair of the ISO working group responsible for the development and maintenance of all ISO standards on information security management including ISO/IEC 27001 and ISO/IEC 27002. He has been at the centre of the development of these information security management standards as well as the international development of third party certification audit
Recommended Reading: Government Funding For Family Caregivers
Advanced Degrees And Certification: Educating It Professionals And Executives On The Principles Of Risk Management
The current level of attention to governance and risk management is not something that has come easy to corporations and governments and has required adjustments at every level. Fortunately, many advanced degrees being offered today for both business and technology professionals include guidance on risk management and compliance principles.
Governance issues are a key part of the curriculum in graduate degree programs related to information systems, and it is considered a standard domain when studying cybersecurity at the masters level.
For IT staff that do not otherwise require advanced degrees, certification programs are now beginning to offer specific modules or domains dealing with information security risk management and governance.
The Certified Information Systems Security Professional track has a knowledge domain specifically dedicated to Information Security Governance and Risk Management, which covers:
- Risk management frameworks
- Risk analysis procedures
- Loss/risk assessment formulas and asset valuation
At all levels, IT departments can expect increased interaction with executive boards and corporate risk management specialists in order to adapt cybersecurity policies to address both technical and legal vulnerabilities.
How Does Data Governance Help Cybersecurity
In order to protect against threats, organizations need to know what data to protect and how to help keep it protected.. Information protection is at the core of security, but how can you protect it if you do not know what data you have, where your data is, how it is used, who it is shared with ? Businesses can no longer have perimeter protections in place and call it a day.the perimeter has expanded to suppliers, cloud vendors, partners, and so on. So managing your data in a structured, responsible, and law-abiding way will make it more efficient for security professionals to protect it.
You May Like: Do I Qualify For Government Housing
Weve Got Your Identity Governance And Administration Needs Covered
Take a look at the type of research you can expect at Gartner Identity & Access Management Summit 2023 in Grapevine, TX.
Leverage the latest identity governance and administration insights to effectively manage your organizations complex array of access rights and identity repositories giving the right people the right access in a highly connected IT environment.
A sample of recommended sessions include:
- Identity-First Security as the North Star for Your IAM Reimplementation
- Ask the Expert: Leading Practices for Authorization and Access Policy Management
- Technical Insights: implement the Right Identity Protocol in Your Apps, Services and APIs
- CIEM Is Paving the Way for Identity Immune Systems in the Cloud. What’s Next?
- Ask the Expert: IGA Deployments
This updated market guide for identity and access management and security leaders acts as an aid to anticipating future trends, features and integration capabilities in the IGA market, helping you to make better procurement decisions in light of the typical five-to-eight-year life span of IGA tools.
Key Findings
Lock Down Your Cybersecurity & Compliance
Protect, Certify & Grow & Your Business
Build resilient governance practices that can adapt and strengthen with evolving threats.
Governance
In this context, cybersecurity governance relates to the organizational plan for cybersecurity and information security. As the University System of Georgia explains:
Effective security governance is managed as an organizational-wide issue that is planned, managed and measured in all areas throughout the organization. In IT Governance, leaders are accountable for and are committed to providing adequate resources to information security.
They go on to list a number of principles that should guide thinking on cybersecurity governance. These include the suggestion that companies should:
- Conduct an annual cybersecurity evaluation, review the evaluation results with staff, and report on performance.
- Conduct periodic risk assessments of information assets as part of a risk management program.
- Implement policies and procedures based on risk assessments to secure information assets.
- Establish a security management structure to assign explicit individual roles, responsibilities, authority, and accountability.
Once a system of governance has been established and clearly defined, the second component of cybersecurity GRC, an assessment of risk, can begin.
Risk
- Understand your specific business context and cybersecurity requirements
- Identify existing gaps and vulnerabilities in your security posture
Compliance
Don’t Miss: Government Dental Assistance For Seniors
Evaluating Risk And Defining Your Risk Approach
You must have a way of scoring risks, and this means you need the information to evaluate the likelihood and consequence of risk. There are different ways of scoring risks but one of them is to use a five-by-five matrix where likelihood and consequence go on a scale of one to five, which five being the most likely or greatest consequence. Multiplying the two together gives you a range of risk scores, going from one to 25.
The higher the risk score the greater the attention you are likely you want to pay to it and it is important to be sure you are using the information you must determine the right likelihood and consequence for any given risk. Otherwise, your risk approach may be the wrong one, and you may not be prepared if the risk becomes an issue.
Once you have made a well-informed attempt to score your risk you need to identify your risk approach that is, what are you going to do about the risk, if anything?
There are four main risk approaches:
One Of The Worst Failures Of Cybersecurity Governance In Us History
Christmas of 2013 was not a very merry one at U.S. retail giant Target.
The day after Thanksgiving, hackers had penetrated the stores internal network and installed a memory scraper named Reedum on every single one of the Point of Sale registers at every single store. During the 17 days the penetration went undetected, the hackers harvested more than 70 million customer credit card numbers.
When Targets IT staff noticed the breach and notified management, the company sat on the news for almost a week, trying to figure out how to handle it. Whatever conclusion they came to, it didnt help much when the news broke. Sales dropped by four percent, right in the middle of the busy Christmas rush. The company began laying off staff almost 500 by January. By February, the costs from the breach had exceeded $200 million. By May CEO Gregg Steinhafel was gone.
But that was just the beginning. The lawsuits started not long after, and kept coming. Banks, consumers, and shareholders had all suffered damages, and all filed suit alleging breach of fiduciary duty, gross mismanagement, and waste of corporate assets. In 2014, the suits expanded, directly naming the companys directors and officers. The failure, it was alleged, was not merely in the nuts and bolts of firewalls and password policy and IT department patching protocols it was a failure of governance and risk managementthe direct responsibility of corporate officers.
Also Check: Government Housing Grants For Low Income Families
Governance And Protection Disciplines
Protection disciplines include access control, asset protection, and innovation security. The security governance team provides standards and guidance to drive consistent execution of security best practices and controls.
In the ideal state, the protection teams apply these controls and provide feedback on what’s working, like challenges in applying the controls. The teams then work together to identify the best solutions.
What Is Data Governance
Data governance is the capability within an organization to help provide for and protect for high quality data throughout the lifecycle of that data. This includes data integrity, data security, availability, and consistency. Data governance includes people, processes, and technology that help enable appropriate handling of the data across the organization. Data governance program policies include:
- Delineating accountability for those responsible for data and data assets
- Assigning responsibility to appropriate levels in the organization for managing and protecting the data
- Determining who can take what actions, with what data, under what circumstances, using what methods
- Identifying safeguards to protect data
- Providing integrity controls to provide for the quality and accuracy of data
You May Like: Government Grants For Individuals With Disabilities
