Good Cybersecurity Means Good Info Governance
schedule
Cybersecurity: the word conjures up images of software engineers in lab coats feverishly analyzing cryptographic code in an effort to thwart an attack from a country somewhere on the other side of the globe. Seemingly daily reports of major data breaches are now coupled with warnings about a cybersecurity talent gap, meaning that there is a critical shortage of the highly technical professionals in the workplace who are specialized in cybersecurity.
This is true. However, much of the work necessary to protect business data does not fall within the purview of the technical cyber-specialists. The foundation of any good information security program is good information governance. In short, before you secure your data, you have to know your data. You have to know what data you have, where you have it, why you have it and how you use it. This may seem like a seductively simple task, but often it is not.
Why Do You Need To Know Your Data?
In the Event of a Potentially Major Data Breach, an Organization Needs Immediate Forensic and Legal Cybersecurity Support
When it happens, organizations that practice good information governance will be far better positioned to weather the storm than those that do not.
Information Governance And Cyber Security Go Hand In Hand
Proper information governance includes creating and revising policies and protocol relating to the handling of all data throughout its life cycle. This includes documenting with network diagrams, data flows and data maps, the responsibilities and roles of each user group, data retention and destruction policy, and incident response plan.
Information governance requires a combined team of high-level management, business, legal, and IT resources to review the organizations need for the information, who should have access, retention/deletion policies, andof significant importanceaccountability. New data types like collaboration applications can make information governance particularly tricky. Make sure you have a playbook for information governance and ediscovery.
Cyber security is inherently more manageable, and thus much more effective, when information governance includes a clear understanding of your organizations data storage, data backup, and data flow. Cyber security isnt just about technologyit is also about the people having access to the data and the process involved.
Restricting access of specific data to appropriate individuals enables targeted data encryption. For instance, data being held for document retention or litigation purposes will be protected differently from data for operational purposes. It can identify obsolete data that may be a cyber security liability.
What Is Information Governance And Why Is It Important
Information governance is the management of information usability, integrity and security. Gartner defines the term as the specification of decision rights and accountability frameworks to ensure appropriate behavior in the valuation, creation, storage, use, archiving and deletion of information. This is a thorough way of saying that an information governance policy and system helps your organization manage data for maximum compliance, security and accessibility. This differs from the data lifecycle in that information governance also covers the policies and procedures governing information across an entire organization.
Why is that so important? There are a few reasons:
Governance is such an important aspect of data-driven businesses that professionals are certified by authorized organizations. For example, the Association of Records Manager and Administrators International is a professional body of information governance experts that certify professionals, offer continuing courses and workshops and sponsor events. Likewise, the Certified Governance Officers Association is a similar organization for governance professionals on an international level.
Also Check: Grants To Start A Trucking Business
Network Security In Information Governance
Network security revolves around several devices, processes, and technologies. These components are conjoined through rules as well as configurations that are meant to cement the elements of the CIA triad of the companys data and computer networks through hardware and software technologies. While managing the network security sufficiently, it will be necessary to have information governance in place, regardless of the organizations size, infrastructure, or industry. Rasouli et al. noted that as the complexity of network architecture keeps growing as per the threat environment, it will be necessary to have policies that can manage as a move to contain ever-changing dimensions, attackers. Understanding network security paradigms and dictates will help tackle vulnerabilities that exist across data, networking devices, applications, devices, and users. Therefore, due to this, there are several management tools for managing network security that can be used in addressing cyber threats within an organization.
Why Information Security Governance Is Needed
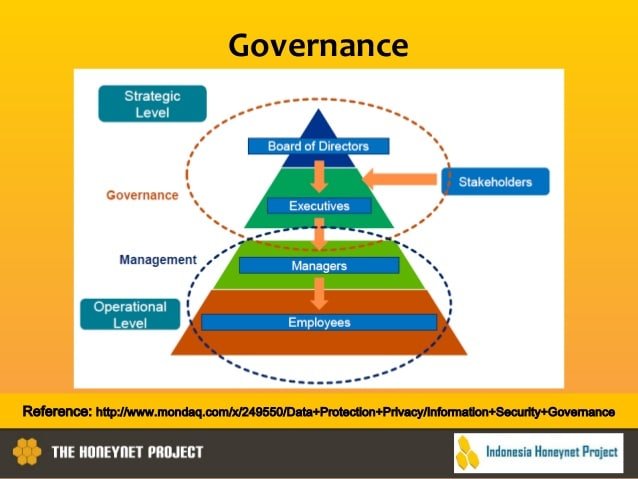
Why is IT governance important
- Financial payoffs
Benefits of information security governance
- Increased predictability and reduced uncertainty of business operations
- Protection from the potential for civil and legal liability
- Structure to optimize the allocation of resources
- Assurance of security policy compliance
- Foundation for effective risk management.
- A level of assurance that critical decisions are not based on faulty information
- Accountability for safeguarding information
Question to engage institutional leaders
Thought provoking questions that institutional leaders can ask to determine the state of their security governance efforts.
- Questions to uncover information security issues
- Does the head of security/CISO routinely meet or brief institutional leaders?
- When was the last time top managers got involved in security-related decisions?
- Do managers know who is responsible for security?
- Would people recognize a security incident? Would they know who to call?
Read Also: Polk Real Foreclosure
What Is An Information Governance Framework
An information governance structure provides a birds-eye view of how your org is creating and managing information assets . This framework is a combination of measures that include policies, procedures, administrative training, technology, compliance demands, risk management and business goals that impact how your data is used.
There are several key components of an information governance framework, which include:
What Is Information Governance Software
Information governance software provides the automated tools the organization needs to comply with vast information governance demands. Identifying, analyzing, adopting, and implementing the right software is crucial in the realization of information governance objectives.
Information technology governance software often includes process and workflow automation solutions that digitize the repetitive and mundane elements of information governance.
Read Also: Government Grants To Start Trucking Business
Information Governance And Cyber Security
Information Governance is a complex idea or system that helps out one organization to make its organizational structure to be risk-free. The main goal of the system is to provide and implement a strategy that can strengthen the security and safety measures especially when it comes to cyber security. In the age of digitalization, it is important to make the cyber walls of the company to be thicker so that it cannot be penetrated by criminals and no breaching can take place. It is highly connected with the Risk management programs. Most security standards, like HIPAA, assert that full compliance is neither possible nor desirable when following a cookie-cutter approach, urging organizations to examine the entire culture and mindset of their offices. This includes periodic audits, simulated scenarios, and so forth. The dairy farming business gives identity to rural women. India is one of the leading dairy product suppliers in the world and the industry in India is dominated by a big farm located in the state of Gujarat. Dairy consumption has plunged worldwide in the past two decades.
Table 1 The Separate Roles Of Boards Of Directors And Management
|
Boards Roles |
|
|---|---|
|
|
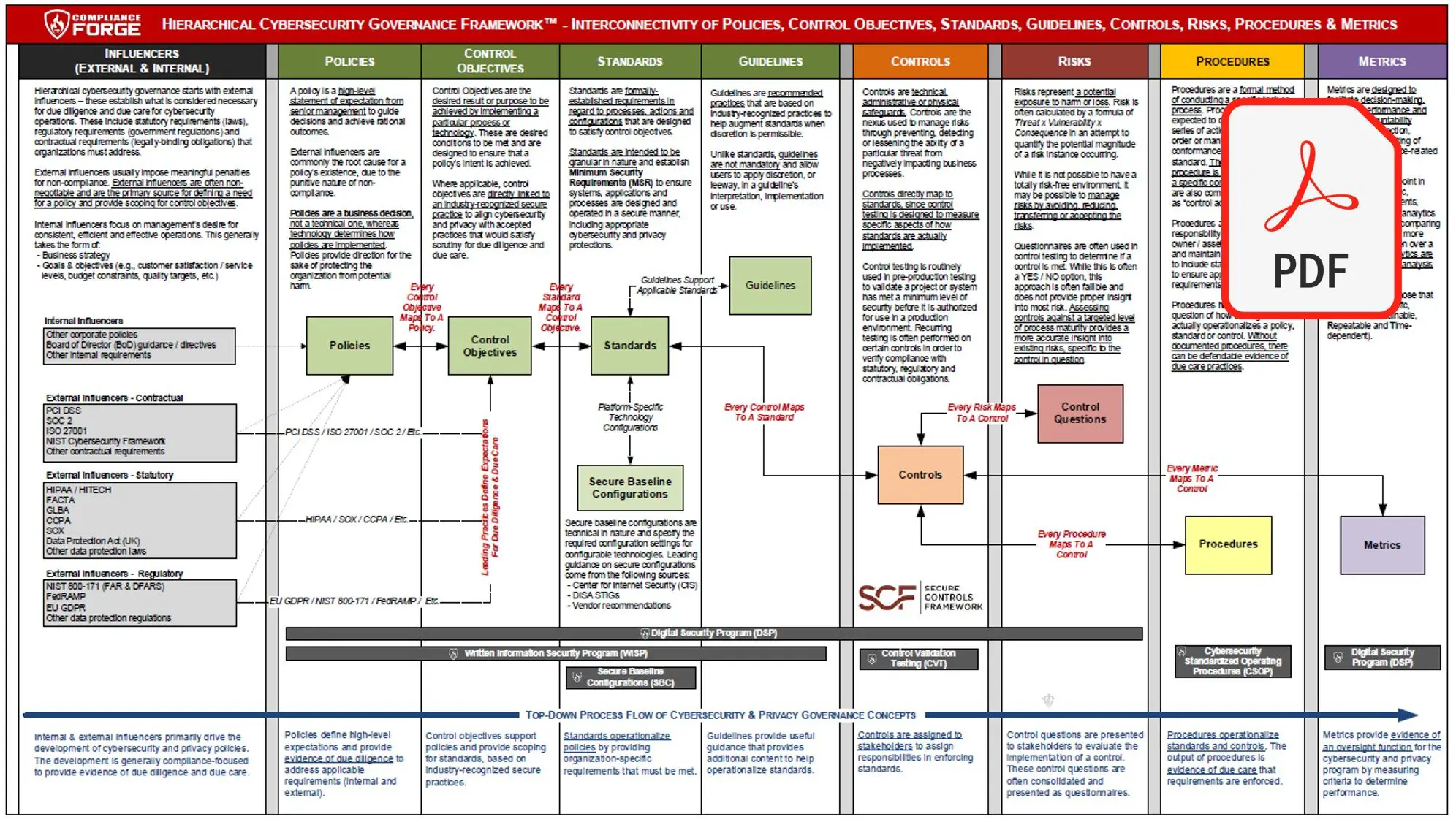
In general, governance is the set of responsibilities and practices exercised by those responsible for an enterprise with the goal of providing strategic direction, ensuring that objectives areachieved, ascertaining that risks are managed appropriately and verifying that the enterprises resources are used responsibly.4 Risks and resources can be associated with different domains , and different domains require specialized expertise in order to manage risks. Thus,enterprise governance frequently is organized by domain.5
Cyber security governance refers to the component of enterprise governance that addresses the enterprises dependence on cyberspace in the presence of adversaries.6 Cyber security governance thus encompasses information systems security governance whether information systems security governance can be identified with information security governance dependsupon how narrowly or broadly the enterprise construes information security.7 However, while aspects of information security governance may address information outside of cyberspace, the flow of information between the non-cyber and cyber realms is so prevalent that in general it ispreferable for cyber security governance to encompass information security governance.
The ICGM utilizes a Plan, Do, Check & Act approach that is a logical way to design a governance structure:
Don’t Miss: Government Jobs For History Majors
How To Govern Information Security
The ISO position is evolving from a primary technical position to one that combines both technical and managerial functions. Today IT security is an institutional imperative with critical policy and operational aspects with attention dedicated from the CIO, general counsel, internal auditor and executive leadership. While the list of tasks for the ISO continues to grow, unfortunately the authority and challenges to that authority of the role are often institutionally handled with senior administrators, legal counsel or law enforcement. The ISO must rely on institutional policy and legal compliance in order to effectively control IT security. Building a relationship and consensus with many groups on campus is a key to having security policy compliance. One progressive step is the growing recognition of department managers to accept responsibility for their data and its protection. Shifting the role of the ISO from compliance dictator to offering assistance realizes the concept of security as a service .
Governance frameworks, COBIT, ITIL, the ISO 17799 information security management standard, and the ISO 9000 quality management standard – are used in the IT governance processes and structures. ITIL and ISO 17799 are the most common frameworks in use.
Organizational Structure
IT governance-related committees include :
Governance structures depend on desired outcomes
CERT GES desribes structure based on desired outcomes.
Information Security Governance Structures
Policy
Data Governance And Cybersecurity Defined
Think of data governance and cybersecurity as overlapping circles. Though distinct concepts, they share common goals and depend on each other.
Data governance involves an organization knowing what data it owns, where that data lives and who owns and uses it. It also encompasses the processes of ensuring the integrity and availability of data, as well as its classification.
Cybersecurity, on the other hand, refers to protecting networks and data from unauthorized access and criminal use. It involves a combination of technology, people and processes working together to prevent and mitigate cyber-attacks.
Data governance and cybersecurity share a common goal of protecting valuable data assets, making quality data available to the right people at the right time. In an environment increasingly influenced by privacy regulations and big data, proper handling of data can have significant repercussions.
You May Like: Money For Homeschooling From The Government
How To Improve Information Governance And Cyber Security
Australian government research shows cyber-crime is costing the Australian economy approximately $3.5 billion a year.
In fact, the government is considering whether to impose personal liability on corporate directors for the cyber-attacks on their organisations.
While cyber-risk has been a key issue for many years, research shows that corporate boards do not appropriately understand itcreating a much larger risk for the Australian economy.
Eliminate Content With No Business Value
A good records management or targeted cleanup process will do wonders to get rid of content that has little value but a lot of potential cost. If the goal is risk reduction, eliminating just the large-volume, short-retention-period data will have a big impact on storage costs and help eliminate unnecessary stuff, which shrinks your risk profile.
Also Check: City Of Las Vegas Government Jobs
What Is Cybersecurity Governance
Do you want to create a cybersecurity governance program for your organization? Are you looking for the right information to make your strategy?
Cybersecurity governance relates to the strategies used by any organization to protect its IT infrastructure. It’s an acknowledgment by the top management that the organization is vulnerable to cyber threats. The actual process is much nuanced and entails a number of factors that we will discuss. In short, cybersecurity governance:
- Is a set of policies and standards
- Differs from one organization to another
- Needs a careful analysis of your present threats and security protocols
- Is usually a management-related activity
- Needs adept knowledge of latest cybersecurity threats and developments
- Differs from programs such as operational cybersecurity as it’s a daily activity
- Needs transparency and setting accountability across stakeholders
- Faces challenges like lack of expertise and budget
You can learn all about cybersecurity governance and its nuances in our blog. So, sit tight as we take up each topic one by one and explain them to you. By the end of this post, you will become an expert on cybersecurity governance.
So, let’s start with the most important question.
Focus Your Searching Efforts
Using a targeted tool like Nuix Data Finder lets you find private data much faster than traditional indexing tools because it only looks for specific data elements rather than trying to account for everything. If your goal is strictly to find and quantify your crown jewels, this approach can save you years.
If you need a broader or more iterative solution, Nuix Data Finder works within Nuix Workstation.
Recommended Reading: Grants For Trucking Companies
Is Cybersecurity Governance Only Applicable To Businesses
Cybersecurity governance is an approach based on a set of principles. You can use the process for any organization or even governments. It doesn’t always have to be a business to adopt a governance program. Any organization that needs to protect its users, data, systems, or networks can adopt cybersecurity governance.
You can follow the principles of security governance to create a protection plan for any entity or agency.
How To Develop A Proper Cybersecurity Governance
You can’t follow any standard procedure for cybersecurity governance. Every organization is different and needs a tailored approach to govern its cybersecurity.
However, some common tenets can help you devise excellent cybersecurity governance. Here are some tips to help you out-
- Tie your security approaches to your organizational objectives
- Identify and empower staff to carry out cybersecurity decisions
- Set up accountability
- Ensure a process of feedback
You should first take a look at the probable threats that apply to your organization. You can then devise fitting strategies to counter those threats.
Recommended Reading: How Do I Get A Grant To Start A Trucking Company
Get To Know Who We Are
Information Governance Solutions supports organisations to meet jurisdictional legal obligations and international standards with strategic and policy solutions including staff training and awareness. For example, the requirements of the Data Protection Act and ISO standards across Africa and other global locations. We provide expert solutions to busines policy challenges linked to information governance and cyber security requirements.
Is Cybersecurity Governance The Same As Operational Cybersecurity
Some organizations may not make a difference between operational and governance cybersecurity. However, there is a subtle difference you must be aware of.
Cybersecurity governance is more focused on planning and strategies. Operational cybersecurity, on the other hand, involves day-to-day activities to prevent and fight cybercrime.
Making the difference is not essential if you have a solid cybersecurity plan. Your team can then implement the strategies on a daily basis for successful cybersecurity governance.
You May Like: City Jobs Las Vegas Nevada
Information Policies And Procedures
Information governance includes multiple distinct policies and procedures. The framework should explicitly enumerate the policies that affect information governance including information security policy, retention policy, disposal policy, archiving policy, privacy policy, ICT policy, remote working policy, and information sharing policy. Information procedures then determine and define how the organization and employees interact with information according to each policy stipulated.
What Is Information Security Governance And What It Is Not
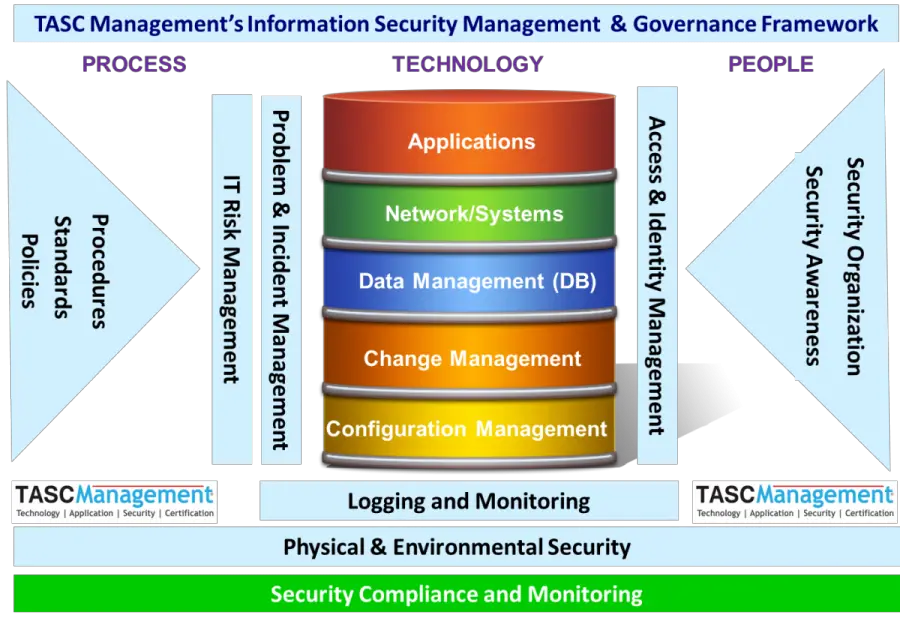
IT security governance is the system by which an organization directs and controls IT security . IT security governance should not be confused with IT security management. IT security management is concerned with making decisions to mitigate risks governance determines who is authorized to make decisions. Governance specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies. Governance ensures that security strategies are aligned with business objectives and consistent with regulations.
NIST describes IT governance as the process of establishing and maintaining a framework to provide assurance that information security strategies are aligned with and support business objectives, are consistent with applicable laws and regulations through adherence to policies and internal controls, and provide assignment of responsibility, all in an effort to manage risk.
Enterprise security governance results from the duty of care owed by leadership towards fiduciary requirements. This position is based on judicial rationale and reasonable standards of care . The five general governance areas are:
Recommended Reading: City Of Las Vegas Government Jobs
