Implementing Iam In The Enterprise
Before any IAM system is rolled out into the enterprise, businesses need to identify who within the organization will play a lead role in developing, enacting and enforcing identity and access policies. IAM impacts every department and every type of user , so it’s essential the IAM team comprises a mix of corporate functions.
IT professionals implementing an IAM system largely on-premises and largely for employees should become familiar with the OSA IAM design pattern for identity management, SP-010. The pattern lays out the architecture of how various roles interact with IAM components as well as the systems that rely on IAM. Policy enforcement and policy decisions are separated from one another, as they are dealt with by different elements within the IAM framework.
Organizations that want to integrate non-employee users and make use of IAM in the cloud in their architecture should follow these steps for building an effective IAM architecture, as explained by expert Ed Moyle:
Difference Between Iam And Iga
The goal of IAM solutions is to assist organizations with managing all user access to systems and data, with the emphasis on maintaining the confidentiality and integrity of the data. IAM also incorporates features to effectively achieve risk and compliance objectives. Unfortunately, IAM solutions typically do not effectively monitor user activity within the application to detect anomalies and threats. Identity Governance & Administration fulfilled this lack of internal control.
IGA is defined by Gartner as an activity within the identity and access management function that concerns the governance and administration of a unique digital representation of a user, including all associated attributes and entitlements.
Simply stated, IAM capabilities help organizations manage user access to applications and data, while IGA capabilities help organizations monitor and govern user activities within the application, to detect and respond to user anomalies or policy exceptions. Together, IAM and IGA can enable a more holistic solution to enable identification, detection, prevention, response, and recovery.
Workforce Productivity: Manage User Lifecycle And Workflows And Reduce It Friction
In any healthy, dynamic business, employees and contractors will frequently join, leave or change roles. As a result, you will also need to plan and build corporate services that are secure, flexible and efficient.
A robust solution will enable automation for tasks and streamline actions such as approvals. This includes:
- provisioning users to the right applications at the right time so they can be immediately productive
- modifying access rights to applications or digital assets when users transition to a different role
- removing access for users leaving organization
Timely provisioning contributes to a companys topline and bottomline. Altering or removing access is vital to protecting company assets, eliminating the risk of unnecessary data breaches and reducing security liability.
User lifecycle can be fully integrated with HR systems or IT helpdesk processes so that your HR and IT teams can collaborate effectively to onboard and offboard employees and contractors. Any advanced HR or IT related workflows can also be supported to ensure any complex user activation to remediation efforts.
Doing this right requires that you plan, design and deploy the right user lifecycle system that streamlines user lifecycle and reduce IT friction. Such lifecycle management is a part of a modern identity, governance and administration framework.
Read Also: Free Credit Score Through Government
Hitachi Id Bravura Identity
Hitachi ID is an industry leader with decades of experience in supporting enterprises including Fortune 500 companies all over the world in their efforts to secure access to systems both on-premises and in the cloud. Hitachi IDs Bravura Identity product comes with a mature set of IGA features that cater to the typical needs of organizations, including a broad set of provisioning connectors.
Hitachi IDs Bravura Identity is an integrated solution designed to manage identities, groups and security entitlements across applications and systems. The solution includes capabilities such as the automated granting or revoking of access in the event of a change to a system o record being detected, a web portal that allows users to review the status and access rights of other users alongside profile updates and certifications, and full lifecycle management for roles and groups on target systems.
With the workflow manager, certain users are invited to oversee and review requests, complete tasks and review access, and the solution also includes policy informants which relate to RBAC, SoD, risk scores, privacy protection and more. With the reports, dashboard and analytics Hitachis solution provides, organizations can also examine trends, access rights, consistency of data, and policy compliance, making it easier to identify and rectify any issues that may occur.
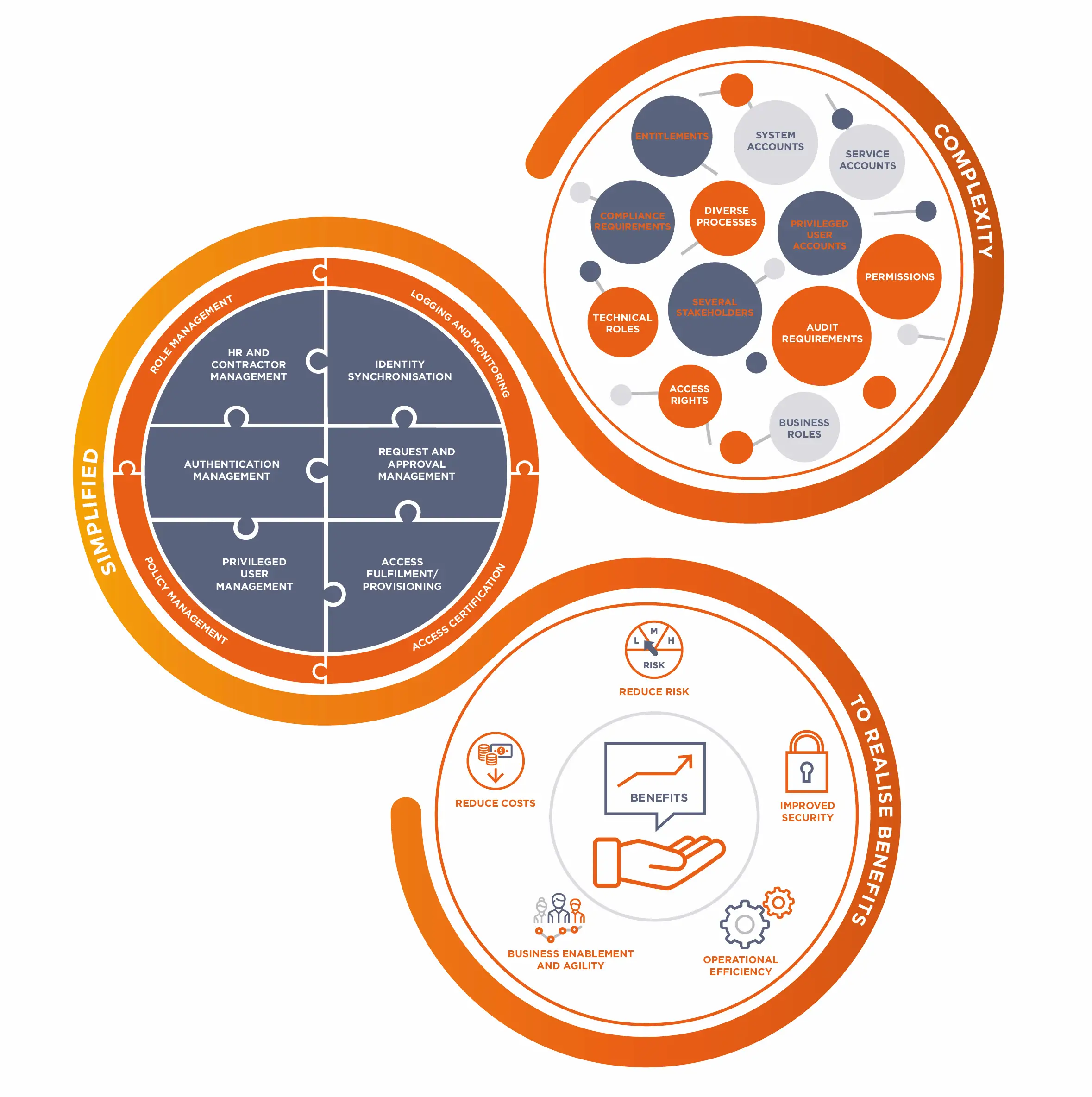
Modern Identity Governance And Administration
The move towards cloud applications, M& As, and remote working, in addition to continuous requirements from the business to onboard new applications are key challenges for many organizations how to maintain control, manage risk, and ensure compliance without restraining business efficiency and collaboration. With the acceleration of digitalization, IT departments are facing an ever increasing workload, where it becomes harder to keep track of compliance and stay in control of security requirements.
Modern identity governance solutions are based on zero trust security principles, but also provide automated implementation of business workflows and processes that enable efficiency, such as automated provisioning, self-service access requests and approvals.
Three business value drivers have created the need for a full-featured identity governance solution
- Compliance the key driver for regulated industries who need to document compliance for authorities and auditors
- Efficiency the key driver for non-regulated industries who need to onboard applications and ensure timely access to a large number of identities
- Security a prerequisite for both to ensure transparency and control of exactly whos allowed to access what and when
Identity governance is the new perimeter
You May Like: Cash For Old Cars Government Program
Ping Intelligent Identity Platform
Overview IAM solution combines security with ease of use, across public cloud, private cloud, and third-party software.
Credential management Secure password self-management single sign-on , social login, and unified authentication for customers, employees, and partners.
Analytics Risk management features to detect suspicious behavior via AI and ML PingIntelligence for APIs to analyze API traffic for possible threats.
External integrations 1500+ IAM integrations as part of the integration directory, featuring first-party apps as well as integrations with SaaS apps and AWS enablers.
Data security User consent collection for data privacy secure data access through agents or proxy data access governance with customer data privacy compliance.
Pricing Starts at $5 per user per month for workforce solutions.
Implementing Iam Helps Organisations With The Following Benefits:
- Access privileges are granted according to policies and groups set, and all individuals and services are properly authenticated, authorised, and audited.
- Organisations whose identities are properly managed have greater control of user access, which reduces the risk of data breaches both internally and externally.
- Automating IAM systems allows businesses to operate more swiftly by decreasing the effort, time, and money that would be required to manually manage user access to their resources.
- In terms of security, the use of an IAM structure can make it easier to enforce policies around user authentication, validation and privileges, and address issues regarding privilege creep.
- IAM systems help companies better comply with government regulations by allowing them to prove corporate information is not being misused. Companies can also demonstrate that any data needed for auditing can be made available on-demand for security checks and audits.
Companies can also gain a competitive edge by implementing IAM tools with best practices. For example, IAM technologies allow the business to provide non-employee users outside the organisation like customers, partners, contractors, and suppliers access to its network across mobile applications, on-premises applications, and SaaS without compromising security. This enables better alliance, improved productivity, efficiency, and reduced. operating costs.
You May Like: Us Government Senate And House Of Representatives
Does Iam Improve Regulatory Compliance
Security is also a matter of law, regulation, and contracts. Data protection standards like Europe’s General Data Protection Regulation and HIPPA and the Sarbanes-Oxley Act in the U.S. enforce strict standards for data security. With an IAM solution, your users and organization can ensure that the highest standards of security, tracking, and administrative transparency are a matter of course in your day-to-day operations.
Customer Identity: Secure And Enhanced Customer Or Consumer Experience
A great customer experience drives customer delight and sales.
Customer experience is important to acquire new customers and retain existing customers. This is true for both transactional as well as subscription-based businesses.
Delivering great experiences actually reduces the cost to serve customers. Unhappy customers are more expensive because they are likely to return products, require more support and may even bruise a well-crafted reputation.
One of the best ways to improve customer experience and delight customers is to offer outstanding digital experiences that include personalized marketing and seamless engagement that is consistent throughout the customer journey.
Customers expect that their digital experience with your enterprise will at least be as good as the best consumer grade apps on the market. This is vital to maintaining your appeal to the market and competitive edge.
However, security must also be a major focus. Unauthorized access that leads to data breaches of customer information and account credentials could hurt your business. Using a robust service layer that allows customers seamless access to various cloud or on-premise digital assets is key to an excellent customer experience. A solution that offers enhanced authentication and seamless customer experience without adding complexity is available today.
Also Check: Government Jobs In Victorville Ca
Iam Vendors And Products
IAM vendors range from large companies — such as IBM, Microsoft, Oracle and RSA — to pure-play providers — such as Okta, Ping and SailPoint. Selecting the best IAM product or service for your organization requires legwork to determine the features that address your needs, such as centralized management, single sign-on, governance, compliance and risk analytics. Check out our 2020 IAM vendor, product and feature listing.
Also read how Okta is going up against giants Microsoft and Google with its passwordless IAM offerings. Okta’s strategy is to implement non-password factors in conjunction with contextual access, with the goal of an improved user experience.
Role Of The Identity And Access Management Team In Data Governance
Because data governance is mainly about data and access management, the identity and access management team ensures accountability through the implementation and documentation of certain security protocols. This can be done through:
- Data Segmentation This involves identifying the types of data flowing through your organization and segmenting depending on what needs protection.
- The Principle of Least Privilege This involves which roles need access to what data and setting permissions around those needs.
- Access Request Process This involves establishing data request processing outside of the normal scope.
Data governance is essential for any organization today. It not only allows for the effective flow of data within the company to enhance productivity, but it also ensures that data does not fall into the wrong hands. Increasing regulations and contractual agreements are forcing companies as the primary drivers to think about data governance. Do you have a data governance strategy in place? If not, it might be time to implement one.
Don’t Miss: Federal Government Contracts For Bid
Identity Governance And Administration
Complete, business-driven governance for identity, data andprivileged permissions
See how you can implement enhanced identity governance and administration capabilities to better manage all users for your on-prem, hybrid and cloud environments. Satisfy audit and compliance initiatives, and easily provide management with a clear view of your governance posture. Meet attestation and recertification requirements with ease. Quickly access data about internal, external and privileged accounts that have access to your on-premises, cloud and hybrid applications to easily pass audits.
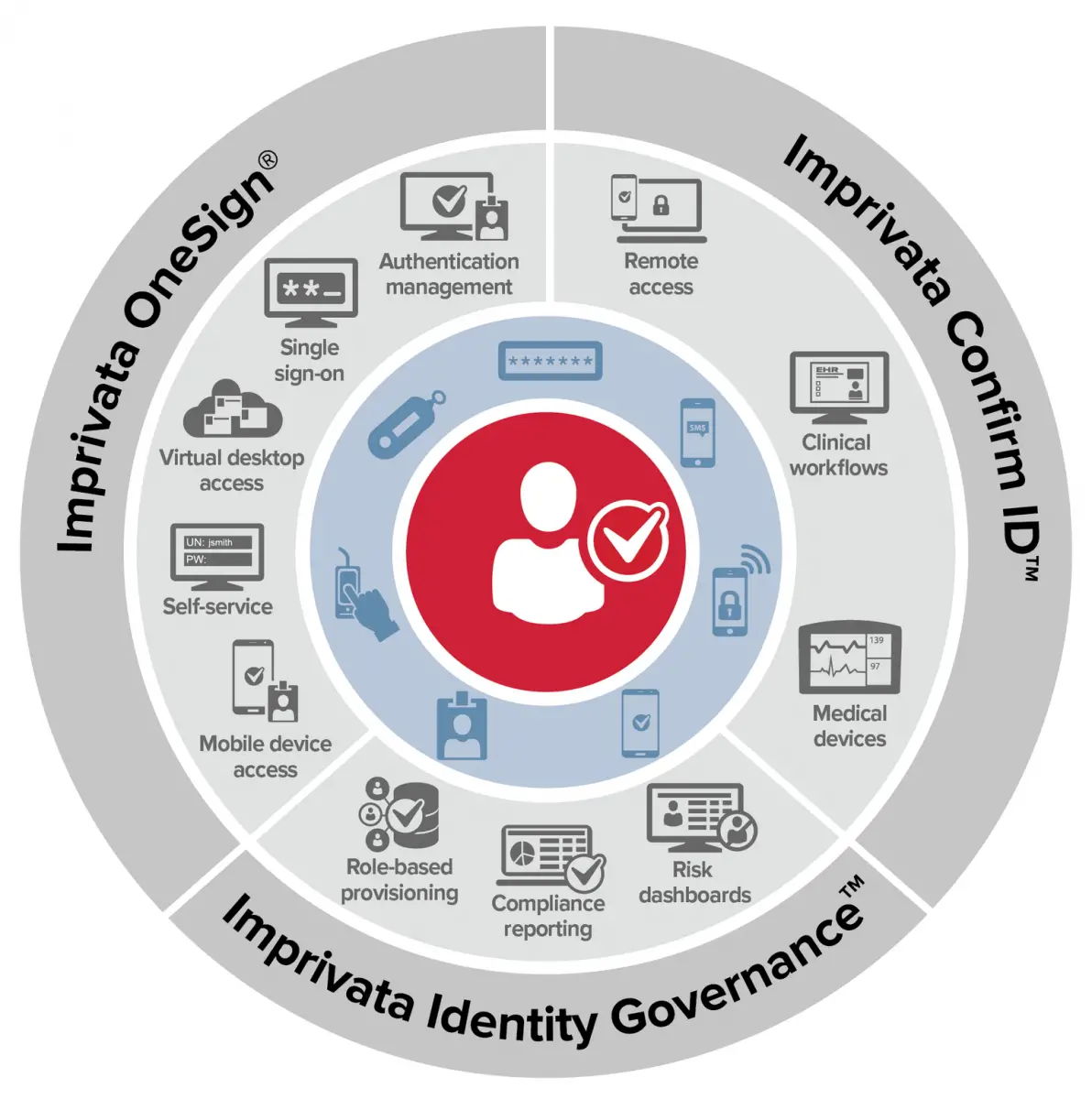
Basic Components Of Iam
An IAM framework enables IT to control user access to critical information within their organizations. IAM products offer role-based access control, which lets system administrators regulate access to systems or networks based on the roles of individual users within the enterprise.
In this context, access is the ability of an individual user to perform a specific task, such as view, create or modify a file. Roles are defined according to job, authority and responsibility within the enterprise.
IAM systems should do the following: capture and record user login information, manage the enterprise database of user identities, and orchestrate the assignment and removal of access privileges.
That means systems used for IAM should provide a centralized directory service with oversight and visibility into all aspects of the company user base.
Digital identities are not just for humans IAM can manage the digital identities of devices and applications to help establish trust.
In the cloud, IAM can be handled by authentication as a service or identity as a service . In both cases, a third-party service provider takes on the burden of authenticating and registering users, as well as managing their information. Read more about these cloud-based IAM options.
Also Check: How To Live For Free Off The Government
Top 10 Identity And Access Management Solutions
Credential theft and account takeover attacks form a disproportionately large share of cyberattacks. IT can mitigate these risks by using a strong identity access management solution. We list the top ten platforms for your consideration to find that perfect IAM solution for your company.
The recent Spotify attack showed exactly how critical identity access management is for enterprises. A malicious entity launched a credential-stuffing operation that could defraud over 300,000 Spotify accounts. In response, Spotify has initiated a rolling reset of passwords for targeted users. Attacks like these can be preempted by an enterprise IAM solution that keeps credentials safe, manages access, and reveals analytics insights into potential vulnerabilities.
If you look at the estimated total economic impact of leading IAM vendors, the numbers are staggering. Forrester reports that the Auth0 IAM software could deliver a massive 548% ROI, with $11.7 million worth of benefits, in less than six months. Similarly, OneLogins solution delivers a 482% ROI in only two months. Given these numbers, IAM investments must be a top priority for companies going into 2021.
Here, we shortlist top IAM software platforms available today and how they address key security requirements such as credential management, analysis, integrations, and data security.
How Does Iam Software Work
IAM software works by using a set of tools to facilitate, control and monitor authentication mechanisms. This involves account and password utilization and role-based access using single sign-on, multi-factor authentication most commonly consisting of a password combined with a hard or soft token providing a rotating PIN used for authentication or integration with large-scale directories such as Active Directory for ease of implementation and administration.
IAM solutions are implemented on both the source such as client workstations, mobile devices and local servers and target systems such as company VPNs and networks, local or remote servers and applications, and network devices so that access is based on a sort of handshake linking the two via permitted access. A common method to deploy IAM tools is to set up company-based access to the appropriate apps in the iOS App Store or Google Play Store, then instruct users on how to download and configure these apps.
Monitoring, logging and alerting features enable company staff to keep track of user access, identify access history and trends, and take action when critical events occur to maintain secure operations.
Read Also: Verizon Wireless Government Phone Number
Tools And Technologies Used In Identity And Access Management
IDENTITY GOVERNANCE & ADMINISTRATION
Identity Governance & Administration automates the creation, management, and certification of user accounts to streamline user provisioning, password management, policy management, access governance, and access reviews. IGA increases visibility into the identities of users to better manage who has access to what systems and when.
PRIVILEGED ACCESS MANAGEMENT
Privileged Access Management is a critical security control that enables organizations to simplify how they define, monitor, and manage privileged access across their IT systems, applications, and infrastructure. PAM solutions centralize management of administrator profiles and ensure least privileged access is enforced to give users only the access they need.
ACCESS INTELLIGENCE
Access intelligence tools enable organizations to maintain a continuous view of their systems, while improving compliance and prioritizing access risks. By providing a comprehensive analysis of the relationship between identities, access rights, and resources, organizations can identify access risks and leverage controls to manage risk within the business.
SINGLE SIGN ON
SSO is a common type of authentication service that allows its users to login to multiple software systems with a single ID generally a username and password. Although most SSO solutions do not widely offer this capability a true SSO solution only requires users to login to a single software system once in order to access them all.
Iga Is Only Relevant To Big Businesses
Thats inaccurate. Managing access controls and having a robust process for managing access to your systems is important regardless of your size. For small businesses that are looking to scale and grow their customer base, implementing IGA processes can ensure that they are proactively compliant with regulations that might target larger companies.
Dont Miss: Government Loans For College Students
Read Also: Government Of Canada Immigration Services
Onelogin Trusted Experience Platform
Overview A unified platform for customer identity, workforce identity, and developer experience management.
Credential management Single sign-on to securely access multiple apps with one set of credentials synchronization with directories like Workday, LDAP, etc., for credential porting.
Analytics Centralized audit trail and standard/custom reports Vigilance AI for entity and user behavior analytics threat intelligence to arrive at a risk score and power MFA.
External integrations An app catalog with 6000+ integrations developer portal with open APIs.
Data security Context-aware access management to filter access to sensitive data enterprise sandbox feature for production data cloning.
Pricing Features-based access starts at $2 per user per month .
