How Much Does Federal Government Spend On Cybersecurity
Everybody talks about cybersecurity, but does anybody spend $28 billion to do something about it?
Well, yes, the U.S. government spends about that much, according to budget watchdog group Taxpayers for Common Sense. That organization recently unveiled its cyber spending database, which breaks down in detail all unclassified government cyber spending.
Until now, there hasnt been an easy way to track this information, according to the organizations blog. Furthermore, the fragmented nature of cybersecurity programs means there is no central authority for tracking amounts or efficiencies of spending.
To build its database, the group pored over publicly available federal budget submissions to Congress and budget justification documents. Researchers sought to identify individual budget lines that contain programs that the government acknowledges relate to cyber spending. In cases where budget documents were not available in a searchable format, we relied on congressional bills and reports for dollar figures. We reviewed only public documents. We did not seek out nor did we review any classified or Sensitive but Unclassified documents, according to the site.
At the top line, the group finds cyber spending rose from $7.5 billion in 2007 to $28 billion in 2016.
Other Top Areas Of Investment
Besides network and cloud security, some other areas of heavy investment include:
Endpoint protection: Endpoint detection and response was the third top priority in fighting new threats. Additionally, a 2019 AT& T Cybersecurity survey found that 76% or organizations found endpoint security more important compared to 12 months before, and 41% increased their endpoint security budget.
Employee training: In the SANS survey, staff skills training was ranked in the top three categories for spending increase in the areas of cloud security, protection against new threats, and privacy and security regulatory compliance. Since the complexities of IT environments are constantly growing, ensuring that your security analysts, engineers and other specialists have current knowledge is one of the best ways to keep up with best practices.
Strong authentication: Authentication is another top priority, based on a Microsoft survey which found that 59% of 100 IT executives across industries planned to invest in or expand their multifactor authentication in 2020. More organizations are also adopting a zero-trust approach, which is based on the premise that no device, connection or user should be trusted until its authenticated.
Shifting Operations: From Keep At Bay To Always Verify
As government organizations start working within large ecosystems, they should also shift their operations to keep pace. The sheer number of interconnections in an ecosystem means that old models of security built on keeping threats at bay outside of networks simply do not work. Rather, security is beginning to shift toward models such as zero trust that assume breaches exist and look to verify that activity is authentic.
The impact of COVID-19 and the subsequent rapid shift to remote work accelerated the adoption of zero-trust models. One Deloitte survey of nearly 600 IT professionals found that 37% saw an acceleration in the adoption of zero trust due to COVID-19.21
And that initial interest is spreading. In the United States, 44 federal agencies have created dedicated teams with line-item funding to either do research in zero-trust or start implementing it.22 In the United Kingdom, the National Cyber Security Centre has released a beta version of its zero-trust principles on GitHub,23 which external organizations can use as a guide while developing their own information systems and networks.24
In this light, the adoption of zero-trust networks is not just another tool in the cybersecurity toolbox rather, it is an important signal of government adjusting to its new role in cyber ecosystems.
You May Like: Rtc Bus Driver Salary Las Vegas
Plan Your Cybersecurity Business Strategy
Cybercrime isnt going away anytime soon. By all accounts, its expected to grow more in number, reach, and sophistication in the years to come, with some help from the COVID-19 pandemic. Its great if your business has an effective cybersecurity system. To ensure fool-proof protection, an organization should have a culture of safety and cybersecurity excellence. Here are some of the essential takeaways from this selection of this years cybersecurity statistics:
- The global cybersecurity market will continue to experience substantial growth.
- The new preferred venue for criminals worldwide is the Internet.
- Cybercrime costs and damages are higher than those of natural calamities.
- Every technological innovation tends to open new opportunities for cybercriminals.
- Cybersecurity jobs will increase.
- Ransomware has become the hacking method of choice among cybercriminals.
- Hospitals are more vulnerable to cybercrime compared to other businesses.
- Cryptojacking is stifling the growth of bitcoin and other cryptocurrencies.
Every business should be aware of the various cyber threats that can impede its operations. With such a stance and knowledge, it will be easier to choose the correct cybersecurity solution for your business. With so many threats lurking in numerous places all the time, today, not tomorrow, is the best time to upgrade your cybersecurity system.
Costs Of Professional Cyber Security Services
There are several factors that determine the hours and cost of data protection from a cyber security company. You need to understand what you are paying for.
Below is a breakdown of hours needed to complete common cyber cyber security services and assessments:
Vulnerability assessment
A vulnerability assessmentcan help an organization understand where it is most exposed and where the most significant risks are for cyber threats. A cyber security architect will have to:
Expected cost for a vulnerability assessment: $1,500 $6,000 for a network with 1-3 servers and $5,000 $10,000 for a network with 5-8 servers.
As cyber threats continue to evolve, theres a lot of value in periodic vulnerability assessments.
Web application assessment
Most businesses rely on the internet to function and generate revenue. A web application assessment is conducted to ensure web applications portals are secure from potential threats. This service can be a one-time cost or a recurring fee depending on your security budget and the requirements of your organization.
Security architecture review
Security program development
Threat monitoring
Recommended Reading: Government Grants To Start Trucking Business
The Total Request Of $174 Billion For Fiscal 2020 Compares With $166 Billion The Administration Sought In 2019
The White House is seeking a 4.7 percent boost in cybersecurity spending across all federal agencies for fiscal year 2020 with the Pentagon and the State Department getting the largest increases, according to details of the request released this week.
The total request of $17.4 billion for fiscal 2020 compares with $16.6 billion the administration sought in 2019. The Pentagon is seeking $9.6 billion or a 10.4 percent increase, and State is seeking $400 million or a 10.2 percent increase. The Justice Department is asking for a 7 percent increase in fiscal year 2020 for a total of $881 million.
The White House said that some elements of the larger federal budget for cybersecurity remained classified because of the sensitive nature of the activities involved.
In 2018 the Trump administration released a National Cybersecurity Strategy and President Donald Trump also authorized the U.S. Cyber Command to more actively push back against attempts by Russia and other countries to interfere in American elections.
In fiscal 2019 the Trump administration sought an 11 percent increase in cybersecurity spending compared with the year before. While federal spending on cybersecurity has steadily grown, state and local governments continue to struggle to fund such programs, the White House said.
Also Watch: Why presidential budget requests are usually dead on arrival, explained
About Aria Cybersecurity Solutions
ARIA Cybersecurity Solutions recognizes that better, stronger, more effective cybersecurity starts with a smarter approach. Our solutions provide new ways to monitor all internal network traffic, while capturing and feeding the right data to existing security tools to improve threat detection and surgically disrupt intrusions. Customers in a range of industries rely on our solutions each and every day to accelerate incident response, automate breach detection, and protect their most critical assets and applications. With a proven track record supporting the Department of Defense and many intelligence agencies in their war on terror, and an award-winning portfolio of security solutions, ARIA Cybersecurity Solutions is committed to leading the way in cybersecurity success
1Dark Reading, 2019 Security Spending Outlook, Ericka Chickowski, February 12, 2019.2Gartner, 2019 Worldwide Security Spending Projection.
Also Check: Government Jobs For History Majors
A Better Chance For Working Capital Funds
Usually any discussion about IT and cyber starts with the TMF. But for this one, lets start with that other piece of the Modernizing Government Technology Act that has the potential for more impactful, working capital funds. Over the last few years, several agencies have asked for this authority from Congress, but only the Small Business Administration has received it.
The Labor Department is asking for authority to create an IT working capital fund using MGT Act authority. This IT WCF would include all activities currently financed through the WCF, as well as the development and operational costs for agency-specific applications currently funded directly by agencies. Shifting these activities into an IT WCF has no impact on total spending at the department.
Labor is asking for $37.2 million for IT modernization efforts in 2022, up from $29 million in 2021 and $26 million in 2020.
The Office of Personnel Management also seems to be requesting authority for an IT WCF too. The budget says it plans to transfer salaries and expenses extra funding into the IT WCF.
OPMs CIOs office asked for $73 million in 2022, up from $39 million in 2021 and $46 million in 2020.
The U.S. Agency for International Development also is seeking IT WCF authority for at least a third year in a row. It is asking to transfer 5% or up to $30 million to the fund.
The CIOs office is asking for $17.7 million in 2022.
What Should I Expect From A Cyber Security Services Company
Now that you understand the cost of cyber security for your business, you may be wondering what is right for you and the next steps.
Every business needs to take action now to make sure they have basic levels of protection. Whether you see the value in the paid products in services, the free protection tips are an excellent place to start to make a big difference.
Proven Data is passionate about helping businesses avoid cyber attacks and keeping them secured with the best cyber security tools & techniques used in the industry today. We can help you identify what security practices are best to meet your budget and business needs.
Were not here to up-sell you on the fanciest, shiniest new security product that you cant even pronounce. Our purpose is to protect your business with the proper level of cyber security services for now and the future.
Also Check: Rtc Jobs Las Vegas
Cybersecurity Spend Can’t Slow As Threats Continue To Grow
Jim RouthChief security officer CVS Health
Routh, who held top security posts at J.P. Morgan and American Express before joining Aetna, now CVS Health, thought the overall threat level would decrease moving from financial services to health care. “Turns out I was wrong,” he said.
The Anthem breach, which occurred between late 2014 and early 2015 and involved 79 million accounts, was the first example of a nation-state threat actor going after health care. Now it is a given that all companies face a diversity of threat actor tactics. “”Nation-state-sponsored threat actors are initiating attacks for political reasons that impact private industries as collateral damage from the cyberattack. There are many different players performing roles in the criminal cyber ecosystem today, including nation-state-sponsored activities to commit fraud for profit. Five years ago nation-state-sponsored cybercriminals weren’t as brazen in attacks on private infrastructure. Today that has fundamentally changed.”
Routh said one aspect of the cybersecurity risk that many people still do not understand is how easy it remains for criminals to access systems through simple methods and how even a low rate of success in hacking can be highly valuable.
While the password already is doomed to obsolescence as a method of authentication, that event is still a long way off.
“It will continue and drive the need for increased budget, and there is no evidence it will slow,” Routh said.
Cybersecurity Funding Winners And Losers
Atlas VPN reviewed the 2020 and 2021 cybersecurity budgets and found that, out of 25 federal agencies, 12 will see a decreased cybersecurity budget in 2021.
The biggest drop in the proposed budget is for the Department of Commerce, which will decrease by over 26%, from $514.3 million in 2020 to $378.1 million in 2021.
Don’t Miss: Entry Level Government Jobs Colorado
Why Is Cyber Security Important For Business
Businesses of all sizes are at risk.
You may think you are not a target because you are a small company, but smaller companies are the most vulnerable since they tend to have less protective security controls.
Ransomware affects 62% of small-medium sized businesses and 32% of larger organizations according to the Beazley Breach Briefing 2020. Ransomware can have a severe impact on those companies who least expect a cyber attack and have yet to develop an incident response plan.
Cyber criminals are constantly devising new ways to infiltrate a network via security vulnerabilities and inflict harm on innocent victims.
The overall number of new vulnerabilities in 2019 increased by 17.6% compared to 2018 and 44.5% compared to 2017, according to a vulnerability study. These numbers are concerning, and this upward trend is likely to continue.
Ransomware has proved to be a lucrative business for many organized cyber crime groups, some boasting as high as $2 billion in revenue. Since one of the main motives for cyber criminals is monetary gain, you can understand why they are actively looking for vulnerabilities.
- Accounting for third-party cyber vulnerability risk-assessment during mergers and acquisitions.
- Keeping client and business information secured to avoid a possible public shaming or brand damage that follows a successful cyber attack on your business.
Us Government Enlists Tech Firms’ Help On Cybersecurity
Microsoft Corporation is building up its government credentials.
The company is part of a trio of technology behemoths chosen for the Joint Defense Cyber Collaborative, an initiative focused on combating ransomware and cyberattacks in cloud computing platforms. The Cybersecurity and Information Security Agency is responsible for the program unveiled last week. The Senate has provided additional funding to CISA in its $1 trillion infrastructure bill for the initiative.
Recommended Reading: Trucking Business Grants
Formjacking & Cryptojacking Statistics
Formjacking and cryptojacking are relatively new forms of cybercrimes. They have already incurred significant losses and damages. Theyre have become very serious threats that Google will be banning all cryptocurrency mining extensions from Chrome.
- Out of 3,500 IT professionals, 17% reported that their organizations were victimized by cryptojacking .
- On average, formjacking codes compromise around 4,800 websites every month .
- Crytojacking accounts for 2.5% of malware among breaches .
- Although the incidence of cryptojacking is relatively low, crypto weaknesses are among the most common network vulnerabilities, with organizations registering a 39.7% vulnerability rate .
- The vulnerability rate for cryptojacking spikes up to 43.7% when it comes to external/public networks .
- The first hacker convicted of SIM swapping was recently sentenced to a 10-year prison sentence.
- A known symptom of cryptojacking is that applications take 5 to 10 times longer to load .
- Cybercriminals can earn around $2.2 million monthly should they steal 10 credit cards from each of the reported 4,800 formjacked sites .
Cybercriminals will continue with their shadowy ways of coming up with novel and more sophisticated ways of attacking the vulnerabilities of digital systems, including common business software applications. Everyone should proactively protect his or her information at all times.
The Trump Administrations Fiscal Year 2021 Budget For Cybersecurity Is Flat Overall For The Coming Fiscal Year After A Significant Bump In Fy 2020
For the third fiscal year in a row the FY 2021 Presidents Budget Request includes detailed government-wide data on the Administrations intent to spend billions of dollars on cybersecurity across federal departments and agencies. Strengthening the cybersecurity posture of federal agencies remains a budget priority and a central component of the Trump Administrations information technology modernization efforts.
In the Analytical Perspectives section of the FY 2021 proposed budget which was released last week, the Office of Management and Budget includes a chapter specifically on Cybersecurity Funding. The inclusion of this funding detail is required under provisions included in the FY 2017 Consolidated Appropriations Act . OMBs analysis addresses that legislative requirement and covers cybersecurity activities and funding for all federal agencies, not just those carried out by the Department of Homeland Security and Department of Defense .
Total Federal Cybersecurity Funding
The FY 2021 budget requests a total of more than $18.7B for FY 2021, down $12.8M from the estimated $18.8B in the current 2020 fiscal year. However, the FY 2021 level would be an increase of more than $1.8B over the FY 2019 actual level of just over $16.9B. If the FY 2021 budget is enacted as requested, the spending level would represent a 0.1% decrease from FY 2020 but an 11% increase over FY 2019.
Is Federal Cyber- Budget Growth Slowing?
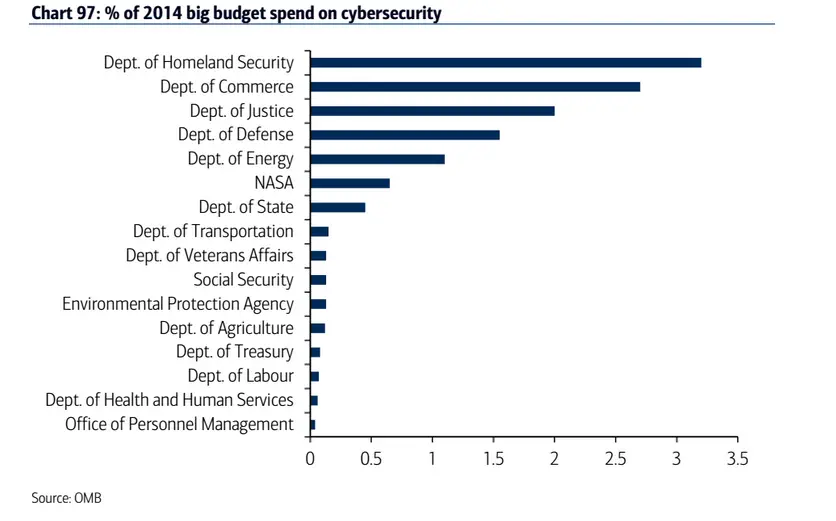
Top Departments and Agencies
About the Author
You May Like: City Of Las Vegas Government Jobs
Shifting Relationships: From Need To Know To Shared Info And Norms
Ecosystems are by definition composed of relationships. So, securing an ecosystem requires using those relationships to share information and set norms of behavior. This can be a significant shift for government agencies used to restricting sensitive data to only those with a need to know. But the shift toward greater sharing and collaborative decision-making is underway at every level.
Some ecosystems are formed at the international level, while others are limited to a specific country or a region. One example of international collaboration is CSIRTAmericas, a community of computer security incident response teams in the Americas region. Through sharing information and knowledge, often in real time, this group has put up a united response to emergencies such as the COVID-19 pandemic and the Wannacry ransomware attack.9
At the national level, organizations in the Netherlands drawn from government, business, the knowledge sector, and higher education have come together to form the Hague Security Delta, a cooperative body working for innovation in security.10 In the United States, the Multi-State Information Sharing and Analysis Center enrolled its 10,000th government organization in November 2020, a rise of about 9,000 organizations in the last seven years. MS-ISAC, a network of state, local, and territorial governments, is set up to exchange knowledge on the latest cyberthreats, share cyber hygiene practices, and get cyber risk assessment.11
