The Early Years: User Provisioning And Mounting Regulations
To understand IGA, its important to understand what provisioning is and how user data was initially stored. User provisioning is the process that ensures that user accounts are created with the proper permissions. IT administrators use provisioning to monitor and control access to systems and applications.
In the early years of the digital age , user provisioning was rather straightforward as it focused solely on users within an organization. Access to users outside an organization, like customers or citizens, was not common. Additionally, there werent as many systems within an organization to manage access to, making the provisioning process relatively manageable.
During this time, servers housed user accounts and identity data centrally on on-premises systems within the enterprise. However, in the mid-late 1990s as the .com market rapidly took off and external user access to systems and applications became ubiquitous, more sensitive user data such as name, address, social security number, country code, email address, bank account number, etc. were collected by global organizations. The need to protect this personally identifiable information , the systems and applications that hosted this information quickly became critical. To address these requirements, new regulations were enacted that mandated stricter security protocols for user access permissions, required improved controls and policies to prove to auditors that the protocols had been implemented.
What Are The Ways And Means Of Managing Identities
dentity management is a combination of processes and software/database tools that enable the creation and management of individual identities. Most of the identity management functions are based on a strong foundation of unified personnel data. This database is used to create and manage privilege rights to the personnel based on their roles in the organization. Once an identity is established for an individual, it is modified on an ongoing basis depending on the roles the person undertakes in the organization. Various ID management systems and tools enable the administrator to create a user id, track it on an ongoing basis and make changes as and when required. Periodic audits are mandatory to ensure that the IDs are functioning in the proper manner.
Several tools that enable the administrator to manage identities include password management, reporting and monitoring systems, provisioning software and signature management. Several organizations have gone a step further to introduce smart card and biometric access mechanisms that incorporate identity data for the individual.
Identity management has also been taken to the next level wherein the same identity is managed across wide range of devices that are carried by an individual to work environment. By creating a single identity and imposing access rights, no matter what device the user logs in, the access rights and criteria remain the same based on the single central identity management system.
-
Overview
Make Iam Easy With Strongdm
Security and compliance concerns consume a ton of time, money, and resources from enterprises every year. Often, these initiatives need so much attention that they can stymie an organizations ability to set more ambitious operations goals. As organizations continue evolving, they need security and compliance tools that can scale rapidly, enhance productivity, and support new technologies, tools, and platforms for hybrid and remote workforces.
strongDM makes IAM easy for any organization. Its Infrastructure Access Platform manages access for all users, with authentication, authorization, networking, and observability, all built right into a single control plane.
Recommended Reading: Access Wireless Order Replacement Phone
What You Will Learn
| Learn the basics of Identity Access Management Solutions and Strategies. |
| Learn about Identity Governance. |
| Discover the methods of WI-FI Hacking. |
| Get acquainted with IAM Standards like ISO 27001 and NIST. |
| Perform Cloud based IAM solutions. |
| Make use of IAM Technology Architectures like OAuth v2, OpenID, SCIM, Kerberos, PKI and many more. |
| Learn the basics of Identity Access Management Solutions and Strategies. |
| Implement Authentication and Authorization IAM Controls |
| Perform Cloud based IAM solutions. |
| Learn about Identity Governance. |
| Get acquainted with IAM Standards like ISO 27001 and NIST. |
| Make use of IAM Technology Architectures like OAuth v2, OpenID, SCIM, Kerberos, PKI and many more. |
Shift Your Security Methodology And Perspective
Transitioning to an IAM framework involves looking at IT, governance, and compliance in a new way.
Put identity authentication and a zero-trust security approach at the center of your security initiatives, instead of network security and protecting your security perimeter. This change in mindset may require significant education and training for users and stakeholders throughout the organization. However, shifting this focus early on can help foster buy-in and adoption throughout your implementation.
Similarly, its important to clearly illustrate the connection between IT security practices and compliance management. If ITs focus was previously centered on network security, it may not be clear to users how IAM technology and identity-first security simplify compliance and governance.
Don’t Miss: Government Jobs Vegas
What Are Pasm And Pedm
As Privileged Access Management has evolved, Gartner has established two further classifications to highlight different mechanisms of PAM solutions. These include Privileged Account and Session Management and Privilege Elevation and Delegation Management . Both PASM and PEDM use the principle of least privilege, which mandates that users only have the access necessary to their job functions, but have different mechanisms in how the target account is protected and accessed.
PASM solutions are often referred to as password vaulting. Privileged account credentials are securely created and distributed exclusively by the solution. When users need access to a specific server, they request access from the vault, and are given a temporary account with full administrative privileges. This account is only valid for a single session. Additionally, the session activity is monitored and recorded.
Leading distribute access privilege based on job roles. Instead of using temporary privileged accounts, PEDM tools assign permanent privilege to standard accounts. PEDM tools define who can have access to each part of a system as well as what they can do with that access. This approach scales much better, centralizes management, and enhances overall security.
Careers In Information Technology
A team of administrators and other technical staffers deploy and manage a company’s IT infrastructure and assets. IT teams depend on a range of specialized information and technology skills and knowledge to support equipment, applications and activities. Third-party contractors and IT vendor support personnel augment the IT team.
The information technology profession is extremely diverse. IT workers can specialize in fields such as software development application management hardware components server, storage or network administration network architecture and more. Many businesses seek IT professionals with mixed or overlapping skill sets.
There is a wide array of IT careers, each with varying technological and managerial requisites. Among the most common IT job titles are the following:
Don’t Miss: Congress Middle Class Mortgage Relief
Design Training To Support Change Management
Every implementation demands a degree of change management. However, introducing new tools and structures with IAM often requires workflow and mindset changes from users at all levels of the organization. Without that support throughout the implementation journey, adoption is a struggle theres a chance users will sidestep sanctioned policies with workarounds, thereby introducing or exacerbating security and compliance risks.
Explaining the reasoning behind your changes isnt enough. Users need to understand the changes in their workflows and how to effectively use IAM tools long before theyre fully rolled out. Prioritizing security training helps support your implementation, improve adoption, and reduce frustration as your organization shifts to an IAM approach. Continue to offer training as you change processes, use new capabilities, and introduce new tools to help users become willing partners towards achieving your organizations security and compliance goals.
Protect The Super Admin Account
The super admin account lets you create your.This admin account is therefore highly privileged. Best practices for thisaccount include the following:
- Create a new account for this purpose don’t use an existing user account.
- Create and protect backup accounts.
- Enable MFA.
For more information, seeSuper administrator account best practices.
Recommended Reading: Congress Stimulus Mortgage Program For Middle Class
Improve Compliance And Audit Performance
Identity governance and administrations alloworganizations to verify that the right controls are in place to meet thesecurity and privacy requirements of regulations like SOX, HIPAA and GDPR. They provide consistent business processes formanaging passwords as well as reviewing, requesting and approving access, allunderpinned by a common policy, role and risk model. With role-based accesscontrol, companies significantly reduce the cost of compliance, while managingrisk and establishing repeatable practices for a more consistent, auditable andeasier-to-manage access certification efforts.
Establish A Centralized System For Improved Visibility
IAM technology is most beneficial when it covers your IT infrastructure from end to end. Centralizing your system helps you manage all identities and access controls from one place, creating a single source of truth and making monitoring data and access across your entire IT infrastructure possible.
A centralized system can simplify automation and policy management, too. However, you may have to move on from some legacy systems or directories to make centralization a reality. Reducing data silos and combining as many resources into your centralized system as possible should be a primary objective in your IAM strategy. Often, that means restructuring some of your existing IT infrastructure to support centralization.
You May Like: Village Of Los Lunas Jobs
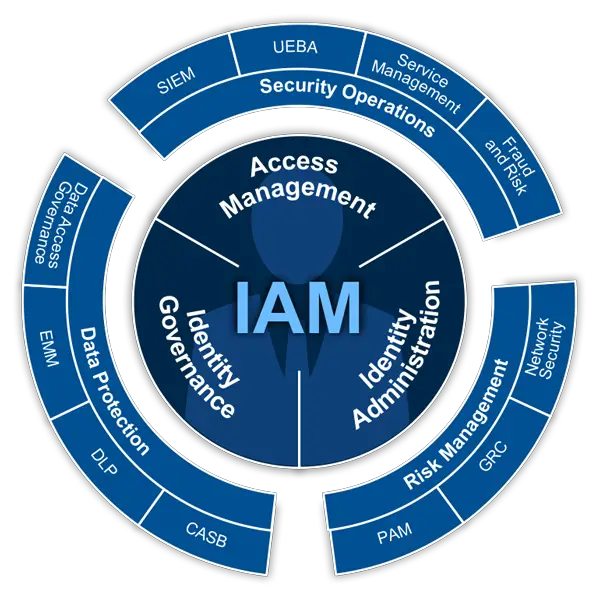
What Is Identity And Access Management Guide To Iam
Identity and access management is a framework of business processes, policies and technologies that facilitates the management of electronic or digital identities. With an IAM framework in place, information technology managers can control user access to critical information within their organizations.Systems used for IAM include single sign-on systems, two-factor authentication, multifactor authentication and privileged access management. These technologies also provide the ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared.
IAM systems can be deployed on premises, provided by a third-party vendor through a cloud-based subscription model or deployed in a hybrid model.
On a fundamental level, IAM encompasses the following components:
- how individuals are identified in a system
- how roles are identified in a system and how they are assigned to individuals
- adding, removing and updating individuals and their roles in a system
- assigning levels of access to individuals or groups of individuals and
- protecting the sensitive data within the system and securing the system itself.
Align It And Business Needs With A Comprehensive Vision
IAM strategy should align with both IT security needs and overall business goals to guarantee the highest possible return on investment. Creating a vision for what a successful IAM implementation looks like starts with defining the objectives you need to meet.
Review auditing and compliance needs, access requirements by roles or attributes, and security gaps where IAM solutions can support your organization. Consider how your needs may change in the future and design your IAM practices to support scalability. Once you have a comprehensive vision, create an incremental implementation plan that aligns with your budget and keeps your data secure throughout the implementation process.
Don’t Miss: Mortgage Stimulus Program Middle Class
Modes Of Identity Management
Identity is conceptualized in three different modes, according to an analysis:from the FIDIS Network of Excellence:
In Bertino’s and Takahashi’s textbook, three categories of identity are defined that are to a degree overlapping with the FIDIS identity concepts:
- Me-Identity: What I define as identity
- Our-Identity: What others and I define as identity
- Their-Identity: What others define as my identity
Why Is Identity And Access Management Important
Today, with most organizations operating globally across geographies, political and physical boundaries, compliance and data security measures have grown in prominence. Any breach in such confidentiality can have far reaching ramifications both from brand and legal perspectives. Identity and access management procedures ensure that organizations can set the right access mechanisms in place to prevent any unintended exposure of sensitive data thereby helping them meet the rigorous compliance mechanisms. Further, by establishing guidelines and rules for access at various organizational levels, identity management ensures that each user of the system can access and manage the data that he is authorised to view, thereby imposing stringent monitoring and data protection mechanisms.
Don’t Miss: Dispensary Silver City Nm
How Fortinet Can Help
Critical components of an IAM system that prevent businesses from falling foul of these risks include:
Discover the IAM products that will secure your businesss identity and access management process. Contact us to learn how Fortinet helps businesses with identity and access and to see some of our successful customer identify management examples.
Iam Vs Am Vs Pam Vs Iga
IAM is far from the only strategy companies use to improve their security, governance, and compliance practices. There are many ways to reduce security risks through identity authentication and access management and, for some organizations, IAM isnt the best fit for their needs.
Some companies dont need the capabilities IAM provides, and others need capabilities far beyond the core IAM features. Many common IAM tools incorporate capabilities from these access management strategies and subsets without explicitly mentioning them by name.
Heres how IAM compares to some of the most common alternatives.
Recommended Reading: Government Jobs In Las Vegas Area
Weve Got Your Identity And Access Management Needs Covered
While we build the agenda, take a look at the type of research you can expect at Gartner Security & Risk Management Summit 2022.
The COVID-19 pandemic has raised the visibility of identity and access management because of the high priority in getting remote access secured and the increased protection needed around digital transformation initiatives. IAM leaders must improve governance and strengthen privileged access management practices to prevent breaches, establish more robust and agile authentication and authorization, and enhance consumer IAM to prevent fraud and protect privacy.
Gartner Predicts
5 Key Predictions for Identity and Access Management and Fraud Detection
Security and risk management leaders must face increasingly complex IAM challenges with a focus on customer-facing interactions and increased remote workers.
Modern Approaches to Identity Governance and Administration Role Modeling
Growth in the number of entitlements across on-premises, cloud infrastructure and SaaS applications creates role management challenges for IAM administrators. Security and risk management technical professionals should use modern tools and iterative processes to develop and optimize an IGA role model.
How Iam Benefits An Organization
- Enhance User Experience:Due to the growth of cloud-based applications employees need to remember the number of passwords for various applications that becomes a challenge for people. Through IAM Single sign-on people have an identity that provides access to different systems, external and internal applications, etc., and improves the user experience.
- Improves Business Productivity:The fully Automated provisioning and de-provisioning in IAM speed the implementation of strong security policies and facilitates access to all components of the system which helps to eliminate human error: and reduces delay in the delivery of access results in immediate business productivity.
- Reduced Security Costs:A comprehensive IAM solution helps administrators to consolidate, control, and simplify access privileges for the critical applications that are hosted in traditional data centers, private/public clouds, or a hybrid combination of all these spaces. Utilizing a single IAM platform to manage all user access allows administrators to perform their work more efficiently.
How IAM benefits an organization?
Read Also: Entry Level Government Jobs Las Vegas
What Is Iam Identity And Access Management Definitions
IAM is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. By assigning users with specific roles and ensuring they have the right level of access to corporate resources and networks, IAM improves security and user experience, enables better business outcomes, and increases the viability of mobile and remote working and cloud adoption.
Create An Iam Integration Strategy
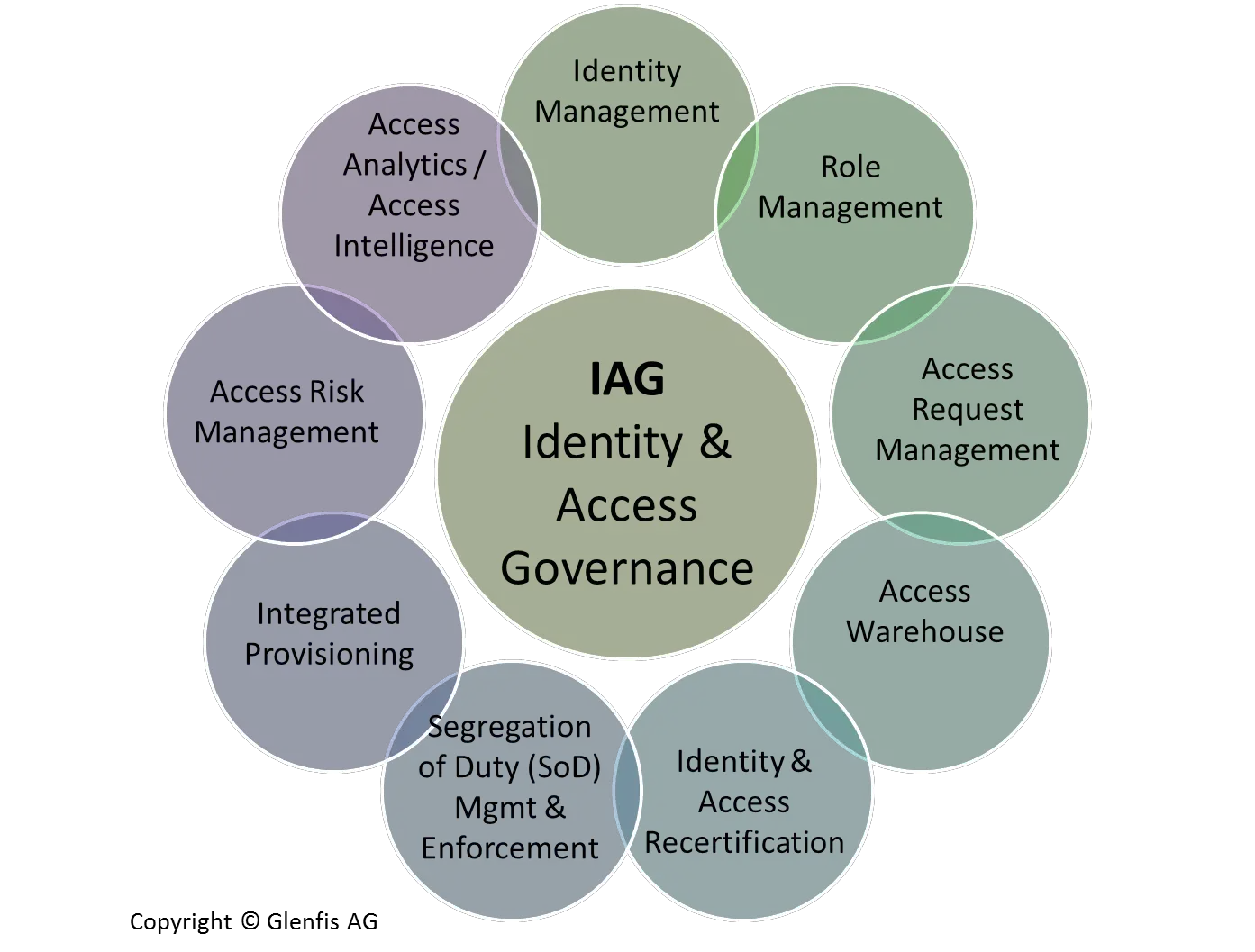
Common risks associated with implementing IAM are integrating the solution with existing solutions, making the move to the cloud, and employees using products and tools not approved by the organization, also known as Shadow IT. These can be avoided by fully embracing the move to IAM, putting the time and effort into establishing a cohesive identity management strategy, and encouraging collaboration across the business.
You May Like: Full Time Jobs In Warner Robins Ga
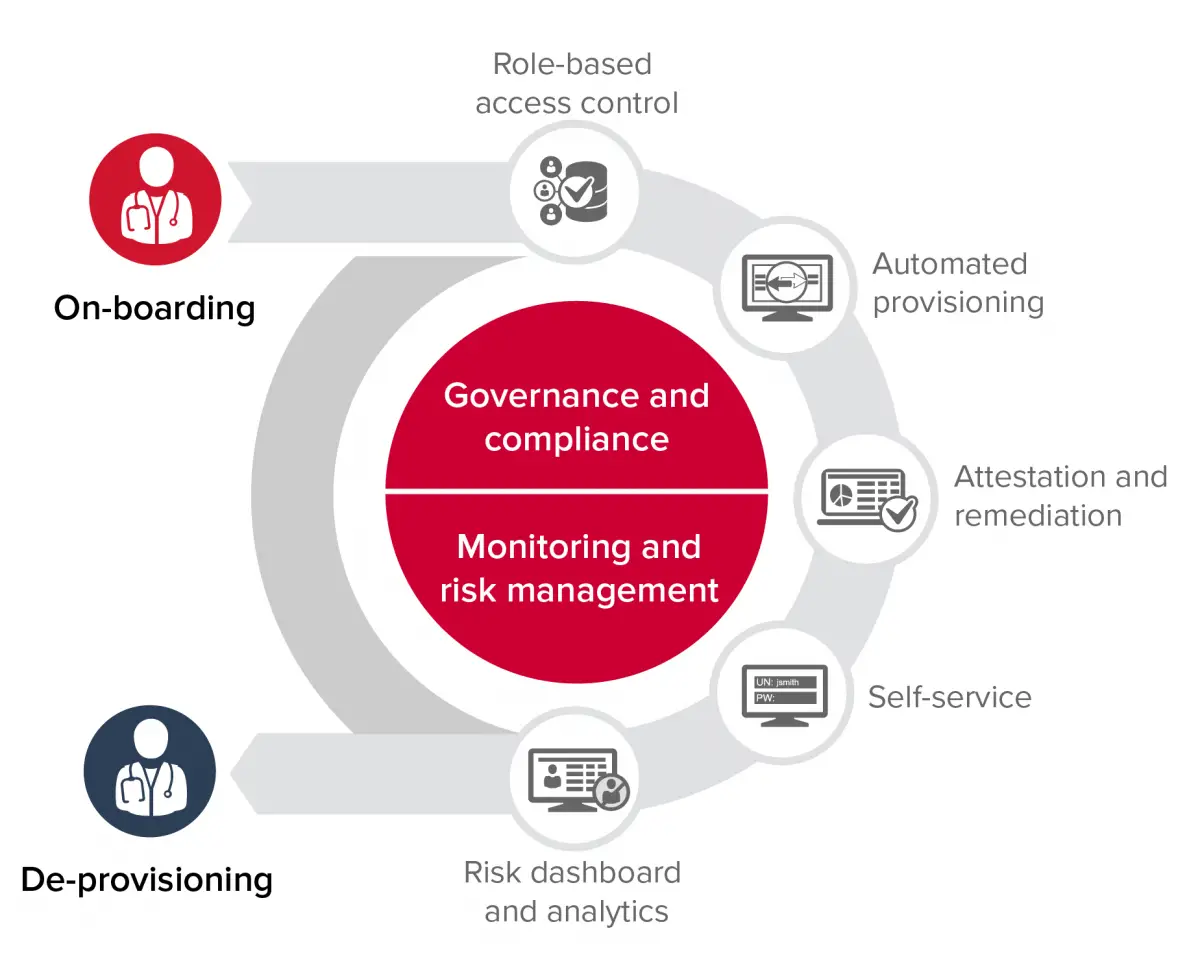
Identity Governance And Administration
When we combine access governance protocols with identity administration, we get identity governance and administration systems. These systems have become essential as internal and external threats to an organizations security continue to grow in both number and complexity. In fact, according to the 2019 Gartner Magic Quadrant for Access Management report, offering IGA through a SaaS model is now emerging as the industry standard.
From a governance perspective IGA systems allow businesses to create rules to prevent giving users too much access to sensitive data conduct access review functionalities implement role-based management and deploy tools that log activities and generate reports on authentication and authorization activities.
