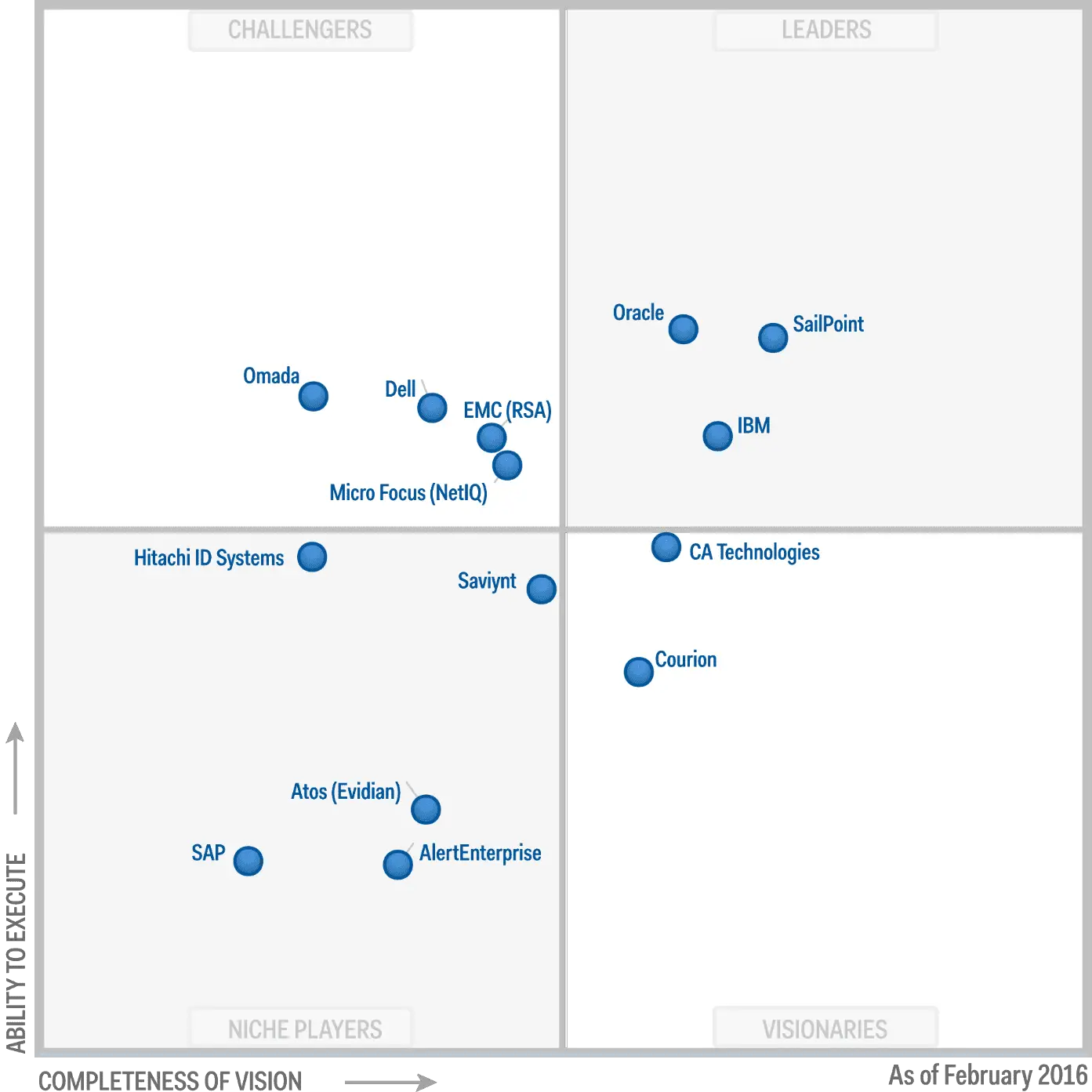
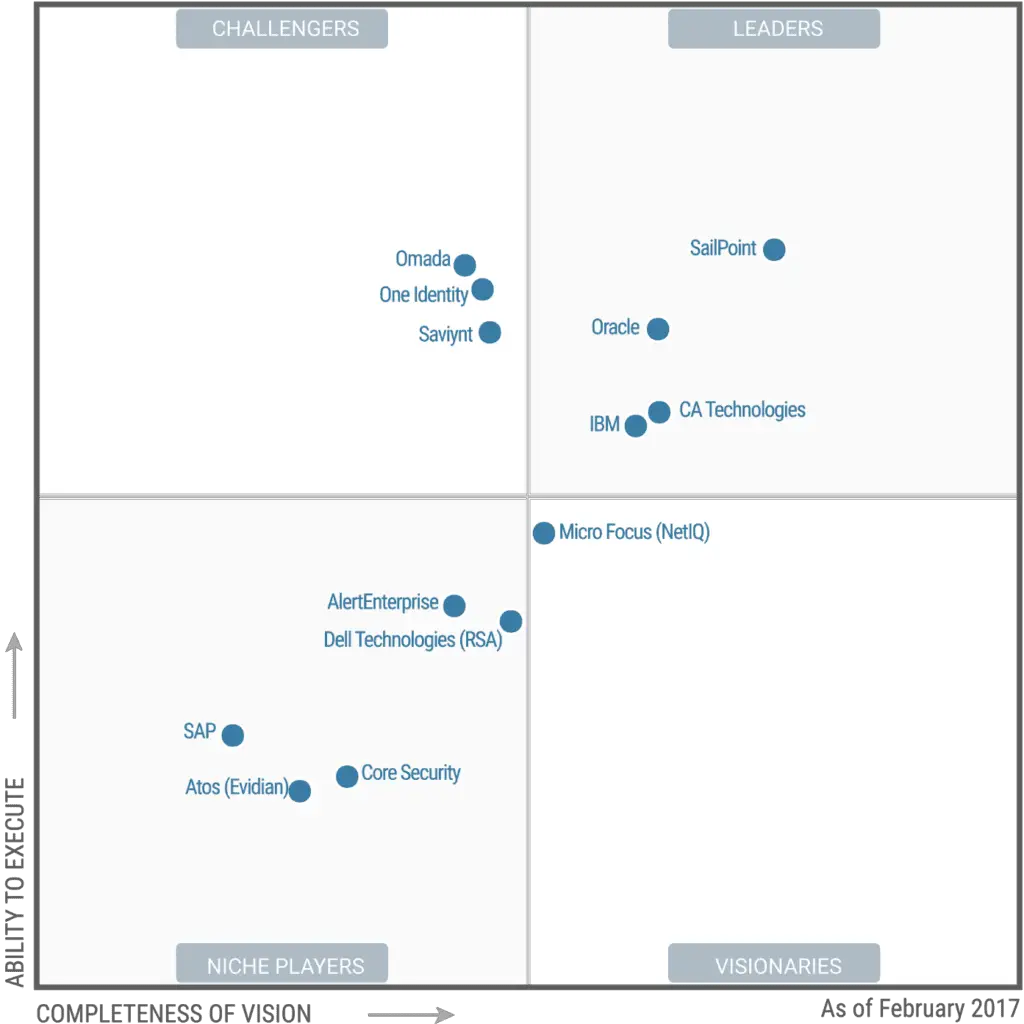
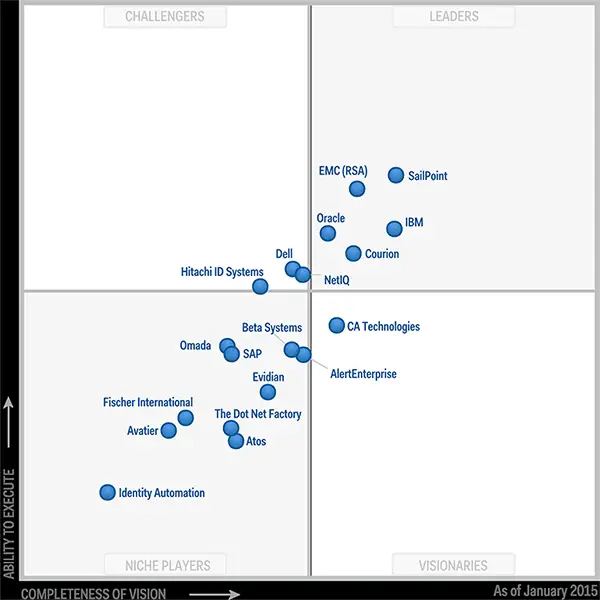
Context For The Gartner Magic Quadrant Report
According to the 2019 Gartner Magic Quadrant for Identity Governance and Administration, the IGA market is mature after six years of existence. Now, IGA solution providers focus on delivering in-demand cloud solutions and fulfilling different business requirements also, Gartner notes that many IGA vendors focus on midsize to global enterprises. Indeed, IGA clients largely rely on their solution providers for successful deployment as only a well-staffed IAM team can deploy it on their own.
Additionally, Gartners researchers share their predictions for the Identity Governance and Administration market. First, they predict the importance of cleanup analytics in future ROIs by 2022. Second, researchers say over half of IGA solution providers will offer predictive and recommendation engines leveraged by machine learning. Currently, less than 15 percent of vendors offer these capabilities.
The 2019 Gartner Magic Quadrant for Identity Governance and Administration warns enterprises against using the vendors positions in the graph as the sole tool for determining a shortlist. In fact, IGA vendors often provide a general set of IGA capabilities that may suit individual use cases.
The 2019 Gartner Magic Quadrant for Identity Governance and Administration is the seventh iteration of the report. According to researchers, IGA began when user administration and provisioning merged with identity and access governance solutions.
Rsa Identity Governance And Lifecycle
Otherwise known as SecurID, RSA Identity Governance and lifecycle is the leading solution for companies hoping to protect their accounts and information in a growing digital landscape. The premium solution is offered as part of the SecurID suite, which helped RSA to earn a position as a leader in the Gartner Magic Quadrant for IT risk management.
The SecurID suite also comes with access to a comprehensive forum and knowledgebase, full of valuable tools and solutions to help you make the most of your governance efforts. You can even access partner training videos and guidance on how to set up certain parts of your ecosystem.
Cybersecurity Mesh Architecture 101
Felix Gaehtgens, VP Analyst, Gartner
With many IT assets now outside traditional enterprise perimeters, IT leaders must rethink security. Enter the cybersecurity mesh architecture with a composable and scalable approach that fosters tighter integration between security controls by creating connections between them. This enables them to share information, intelligence and to act more like a collaborative team in protecting distributed assets.
Tuesday, March 21, 2023 / 12:00 PM – 12:30 PM CDT
Recommended Reading: Government Grants For Home Improvements For Senior Citizens
Enable User Access Without Compromising Security
Built on a foundation of artificial intelligence and machine learning, the SailPoint Identity Security Platform delivers the right level of access to the right identities and resources at the right timematching the scale, velocity, and changing needs of todays cloud-oriented, modern enterprise.
Unmatched Intelligence
Built-in artificial intelligence provides 360-degree visibility, insight, and remediation, so you can adapt and ensure the security of every identitys access.
Frictionless Automation
Customizable workflows automate and streamline identity processes to better discover, manage and secure your users access. This frees your users to focus on innovation, collaboration, and productivity.
Comprehensive Integration
Seamlessly connect your entire ecosystem through thousands of integrations extending your ability to embed identity context across your hybrid environment and centrally manage and control access.
Identities managed
Weaponize Risk Appetite To Drive Risk Decisions
Paul Proctor, Distinguished VP Analyst, Gartner
Risk appetite fails when it is expressed in fuzzy, imprecise terms. Repositioning risk appetite in the context of investment and value delivery creates a measurable scale of risk that powers a new type of governance. Concrete assertions of risk appetite make executive decisions binding.
Tuesday, March 21, 2023 / 02:00 PM – 02:30 PM CDT
Also Check: Paper Application For Free Government Phone
Recognized In Industrial Iot
With a long history stretching to the early days of IoT technology, Microsoft remains committed to providing the evolving infrastructure that companies need to excel with IoT deployments. Our IoT technology is embedded in everything from inspecting vehicle build quality, to monitoring and shifting energy across utility grids, to recycling surplus manufacturing materials.
To continue our position on IoT technology and applications, were especially focused on supporting key areas that customers are prioritizing:
IT/OT convergence: Digital transformation in the industrial sector is increasingly bringing together ITsystems to collect and analyze data to manage processeswith operational technology , which is dedicated to detecting and controlling physical processes. This IT/OT convergence allows for more direct and real-time monitoring, analysis, and control of industrial processes and enables increased automation, faster responses to challenges, and shifts in manufacturing or production rates. With Microsoft Azure IoT, operators can move toward this convergence with system openness and visibility, as well as security.
Workshop: Sharpen It Influence In The Board Room With Risk Value And Cost
Paul Proctor, Distinguished VP Analyst, Gartner
Technology investments in a business context create better business outcomes. Balancing risk, value and cost is central to all business decision-making and a powerful lens to drive IT priorities and investments. Gartners RVC model and outcome-driven metrics help the modern CIO link technology investments back to business outcomes.
Tuesday, March 21, 2023 / 10:30 AM – 11:00 AM CDT
Read Also: Data Governance Process Flow Chart
The State Of Access Management 2023
Michael Kelley, Sr Director Analyst, Gartner
Access management tools are offering an array of increasingly converged technologies. This session will cover the progression and maturity of access management tools and how they will help you achieve identity first security strategies.
Monday, March 20, 2023 / 12:30 PM – 01:00 PM CDT
Technical Insights: Identity Fabric From Here To There
In a world where identity is the only perimeter, more effective identity and access management is now an imperative. IAM must be deployed more cohesively as a composable, distributed, resilient identity fabric. This session will explain the 10 identity fabric principles that should guide IAM decisions.
Wednesday, March 22, 2023 / 10:30 AM – 11:15 AM CDT
Also Check: Government Grants For Personal Need
What Is Identity Governance
The Gartner Magic Quadrant for Identity Governance and Administration isnt just a set of market predictions and vendor profiles its also an excellent tool for defining this distinct and powerful cybersecurity tool.
Identity Governance is a critical component or subsection in the larger identity and access management field. It is responsible for the distribution and monitoring of roles and permissions within your enterprises IT environment. Identity governance can tell you which employees have what access in your network, who is responsible for granting those permissions, and when employees use those permissions to access enterprise assets or databases.
This capability is essential not only for fulfilling regulatory compliance mandateswhich it canbut also for protecting your digital assets. Insider threats have a higher chance of success bringing financial and legal repercussions to your businessif they are allowed to operate in digital darkness. Identity governance prevents that from happening by providing visibility on precisely who can do what and when they do it, allowing your IT security team to adjust permissions on the fly if they constitute a security risk.
Microsoft Named A Leader In The 2022 Gartner Magic Quadrant For Global Industrial Iot Platforms
Posted on December 19, 2022
As industrial Internet of Things matures and transforms critical business functions, Microsoft continues to innovate and invest in this area and engage with a large ecosystem of solution partners.
The Microsoft Azure IoT platform can help industries improve their operations to become more efficient, agile, and sustainable. And industrial-focused IoT technologies from Microsoft are especially important for enterprises looking to do more with less in the current macro-economic environment.
Were focused on enabling industrial IoT solution providers and customer operations to be successful, and we believe those efforts havent gone unnoticed. For the third year in a row, Gartner has positioned Microsoft as a Leader in the 2022 Gartner Magic Quadrant for Global Industrial IoT Platforms.
Also Check: Government Programs For Troubled Youth
How To Combat Inflation During Vendor Negotiations Using Gartner’s Four
Jo Ann Rosenberger, Distinguished VP, Advisory, Gartner
Inflationary times create added complexity when negotiating with vendors. Gartner’s four-step approach to proactively plan for new and renewal deals can help assess the fairness of increases as well as use data points from economic indicators such as CPI and ECI to customize “should cost” models to use during vendor negotiations. This session will demonstrate these steps by walking through two case study scenarios.
Tuesday, March 21, 2023 / 04:30 PM – 05:00 PM CDT
Kuppingercole Leadership Compassidentity Governance & Administration
Avatier has been named a Leader in the KuppingerCole Leadership Compass for Identity Governance and Administration. The report evaluatesIAM solutions that offer identity governance and provisioning.
Fill out the form to receive access to the KuppingerCole Leadership Compass today
AIMS solutions are easy to configure and deploy at a low cost in comparison to other IGA vendors.
Read Also: Government Grants To Start A Farm
Avoid The Breach With Identity Threat Detection And Response
Henrique Teixeira, Sr Director Analyst, Gartner
Conventional IAM and security prevention controls are not sufficient to protect your identity system itself from cyberattacks. Learn how to enhance your cyberattack preparedness with the emerging discipline of ITDR.
Tuesday, March 21, 2023 / 10:30 AM – 11:15 AM CDT
The State Of Customer Iam 2023
Demand for customer IAM has increased, due to its importance in converging UX, security and privacy for high-assurance interactions. How is CIAM technology continuing to evolve to meet these new challenges? We will talk about what is available today, and what kinds of things can you expect to take advantage of in the near future.
Tuesday, March 21, 2023 / 10:30 AM – 12:00 PM CDT
Also Check: Sba Loans Backed By Government
Go Passwordless Whenever You Can Wherever You Can
Ant Allan, VP Analyst, Gartner
To improve security and enhance UX, many organizations are already implementing various styles of passwordless authentication across a variety of use cases. This session will look to address the following questions. How can IAM leaders choose among the many passwordless approaches? Which approaches are most effective? Which approaches are feasible in which use cases? How do you deal with legacy applications? How can you craft a cohesive strategy across multiple use cases?
Monday, March 20, 2023 / 04:00 PM – 04:30 PM CDT
So What Exactly Is Iga And How Is It Different From Access Management
David Collinson, Sr Director Analyst, Gartner
This is a session to introduce what IGA is and is not, and how it differs and interacts with access management tools. Ideal for individuals that are being asked to take on responsibilities in this area or for senior leaders to be given a high-level introduction in to these capabilities.
Monday, March 20, 2023 / 04:00 PM – 04:30 PM CDT
Recommended Reading: Is The Government Giving Out Free Money
Ask The Expert: User Authentication
Ant Allan, VP Analyst, Gartner
This interactive session enables attendees to ask the Gartner expert and learn from others about any authentication or adjacent topic. Topics covered include requirements definition, the pros and cons of different technologies, passwordless authentication trends, the shift towards continuous adaptive trust, synergies with identity proofing, user experience and life cycle management.
Tuesday, March 21, 2023 / 03:45 PM – 04:15 PM CDT
Why Hasnt Gartner Released A Statement
We can think of a few reasons why Gartner may choose to hold on making a statement. First, the coronavirus outbreak continues to take up a lot of national and global attention releasing a statement now would probably see it buried in the flood of other conversations.
Second, Gartner may want to wait until they release a 2020 IGA Market Guide before they speak to why they chose to retire the IGA Magic Quadrant.
Third, they may also wait until the release of the Access Management Magic Quadrant before they make any official announcement. Gartner chose to fold its previous IDaaS Magic Quadrant into its Access Management MQ report and may do so for IGA as well.
We will continue to report on this as news develops.
Also Check: How Do You Know If The Government Owes You Money
Ask The Expert: Discovering Managing And Controlling Workload Identities
Erik Wahlstrom, Sr Director Analyst, Gartner
Come to this session prepared to ask questions about workload identities. How should identities, secrets, keys and certificates be discovered, managed and maintained for applications, services, containers and VMs in an hybrid and multicloud environment?
Monday, March 20, 2023 / 12:30 PM – 01:00 PM CDT
Ask The Expert: Ciem Itdr And Identity Immune Systems
Henrique Teixeira, Sr Director Analyst, Gartner
Cloud infrastructure entitlement management plays an important role in identity security posture management, with identity threat detection and response adding protection mechanisms against ongoing attacks to the identity infrastructure. Ask me anything about how ITDR and IDSP can be combined to create identity immune systems.
Tuesday, March 21, 2023 / 10:30 AM – 11:00 AM CDT
Read Also: Government Free Mortgage Relief Program
What Is Identity Governance And Administration
IGA is both a policy framework and set of security solutions that enable organizations to more effectively mitigate identity-related access risks within their business. IGA automates the creation, management, and certification of user accounts, roles, and access rights for individual users in an organization. This means companies can streamline user provisioning, password management, policy management, access governance, and access reviews within their business.
Another definition of identity governance, as defined by Tech Target, is the policy-based centralized orchestration of user identity management and access control, indicating the function helps support enterprise IT security and regulatory compliance. Put into simpler terms, IGA means leveraging the most intelligent and efficient path to mitigating identity risk in your business.
Considered part of Identity and Access Management, Identity Governance and Administration offers organizations increased visibility into the identities and access privileges of users, so they can better manage who has access to what systems, and when. Identity governance empowers organizations to do more with less, enhance their security posture, and meet increasing auditor demands, while also scaling for growth.
Ask The Expert: Leading Practices For Authorization And Access Policy Management
Every organization does authorization, but managing authorization well remains a substantial challenge across industries. In this session Gartner analyst Nathan Harris will answer questions related to authorization and access policy management approaches that are working well and where companies are finding the best overall value. Specific topics included are RBAC, ABAC, run time vs. admin time authorization and externalized authorization.
Monday, March 20, 2023 / 12:30 PM – 01:15 PM CDT
Don’t Miss: Free Government Phones With Data
What Is Privileged Access Management
Now that weve examined IAM and IGA, lets take a look at Privileged Access Management. PAM is considered a critical security control that enables organizations to simplify how they define, monitor, and manage privileged access across their IT systems, applications, and infrastructure.
Because administrator accounts have elevated privileges that can access valuable data and execute applications or transactionsoften with little or no tracking controlit can be very difficult to manage privileged accounts. PAM solutions centralize management of administrator profiles and ensure least privilege access is enforced to give users only the access they need.
Of each of the three areas discussed here, PAM is the most narrowly defined, but has the significant responsibility for mitigating identity-related access risks related to privileged access. While IAM and IGA focus on wider levels of user access for resources, systems, and applications across the organization, PAM primarily defines and controls access for privileged users. Lets take a look now at some .
How Servicecontrol Helps
We specialize in Identity and Governance Administration solutions that deliver user administration, privileged account management, rich audit trail, enhanced security and compliance to on-premise, hybrid and cloud environments. Our IGA solutions help customers manage identity and access life cycles across multiple systems in their heterogeneous environment.
Our unified management portal replaces the need to deal with multiple proprietary management portals, providing secure delegated account management, provisioning and moving tasks to non-technical front-line staff
Our solutions help medium to large enterprise clients secure access to on-premises and cloud applications while improving operational efficiencies. This is achieved by allowing non-technical staff to receive authority to reset passwords, release intruder lockout, create accounts, create distribution lists, enable/disable accounts, manage group memberships and email distribution lists across multiple cloud services and on-premises application with a full audit trail.
Also Check: Michigan Schools And Government Credit Union Cd Rates
Outlook For Privacy 2023
Bernard Woo, VP Analyst, Gartner
Privacy has been the biggest catalyst for change in data governance over the past five years. This session will dive into the top trends and technologies, and separate the hype from substance. Come get a sneak peek into the future of privacy and what you should watch out for in coming 12 months.
Wednesday, March 22, 2023 / 10:30 AM – 11:00 AM CDT
Gartner Keynote: Outlook For Identity And Access Management 2023
Homan Farahmand, VP Analyst, Gartner
Digital identity requirements and importance are growing, as organizations are migrating their infrastructure and apps to the cloud. Enterprises anticipate innovations to enable continuous, dynamic, and intelligent IAM controls, while bracing for emerging decentralized identity impact and potential Web 3 business model disruption. This session discusses key trends and IAM outlook in the coming years.
You May Like: Government Contract Work From Home
Keynote: Lead Like A Wolf
Tina Nunno, Distinguished VP Analyst, Gartner
As a leader, are you a predator or prey, and what should you aspire to be? Technology executives are more visible now than ever before, this can be both an opportunity and a challenge. This session will explore how being a wolf can make you a better leader for your team and a great asset for your organization. Before this session find out yours at Gartner.com/wolfcio and learn more about what your results mean during the keynote.
Monday, March 20, 2023 / 11:00 AM – 11:30 AM CDT
