Risk Quantifiable Metrics And Aligning With Business Objectives
Contributed by Padraic OReilly
Risk management is the new foundation for an information security program. Coupled with necessary compliance activities to support ongoing business operations, risk management centers upon identifying and working to mitigate risks associated with a given organization. As more enterprises embrace digital technology, the relative importance of risk over compliance has grown with the growing variety of technologies that organizations are adopting, baseline compliance is necessary, but still only a basic step to ensuring that the organization is secure.
Cybersecurity Specialization: Governance Risk And Compliance
Acquire the skills to design a system of governance to enforce compliance with laws, regulations, and company policies.
In an ever-changing political and criminal landscape, there is an increasing need for people with specialized and up-to-date knowledge of current cybersecurity laws, regulations, and best practices. The skills gap this need creates in an organization exposes the organization to liability.
Cybersecurity Specialization: Governance, Risk, and Compliance will give you an understanding of the current laws and regulations that drive the creation of a governance system of rules, practices, and processes by which a company is directed and controlled. Understanding the fundamentals of the implementation of a risk management strategy will help your organization achieve compliance through policy management, control creation, and assessment of the effectiveness of controls. In this course, you will learn to set up processes to enforce compliant behaviors in your organization, including the enforcement of a systemic culture of documentation, verification, audits, remediation, follow-through, responsibility, and authority.
The course uses a challenge-based design focusing on what a learner should be able to do at the end of the course and back on the job. The practice opportunities and challenge activities resembleas much as possibletasks the learner would be asked to perform in a real-life situation.
Your Trusted Security Partner
Contact our cyber security customer service desk and technical support agents here:Contact Us or call toll free at . The service desk oversees support to our customers with their IT, Cybersecurity and Regulatory Compliance needs.
Use the search to find the security services you are looking for, or call the number above to speak with a security professional
Cyber Security Operations Consulting is an innovative cybersecurity consulting services firm, providing cyber security consultants and managed security services, empowering businesses since 2001. CyberSecOp’s Cybersecurity Service provides Information and Cyber Security Strategy & Design Consulting services to give your business a better cyber security posture. Our IT Security Services shield your enterprise against cyber threats and strengthen your cybersecurity defenses. You can depend on us to provide comprehensive Information and Cybersecurity as a Service and Security Solutions. Our IT & cybersecurity consulting service protects you from cyber criminals in myriad ways, from implementing a cyber security program, which include a written information security program, cyber Incident response, and cybersecurity assessment services to offering the best-in-class cybersecurity consulting and IT security solutions which can be managed by our managed security services. CyberSecOp is an CMMC-AB RPO& ISO 27001 Certified Organization – join thousands of businesses by putting your security in our hands.
Read Also: Free Government Grants For New Businesses
Grc Platforms For Regulatory Framework Compliance
Finally, regulatory compliance with various required cybersecurity and legal frameworks is an area that also spans IT and cybersecurity into physical safeguards and overall governance. Suppose your company operates within or adjacent to a particularly vulnerable industry or one that is a frequent and lucrative target of cybercrime. In that case, it may need to comply with one or more frameworks.
GRC approaches to compliance are revolutionary for combining the wide-reaching elements of compliance and compliance advisory services into one simplified package. In the past, in the absence of a GRC approach, companies would often need to implement compliance for many different frameworks operating independently of each other and irrespective of all their other governance and risk management concerns. GRC facilitates compliance across all frameworks.
What Is A Governance Risk And Compliance Platform
Work-from-home mandates have accelerated an already growing trend toward mobile, remote working solutions. This extended the office and all cybersecurity concerns into the home or other networks. Companies now have less visibility and control, creating complex issues for information technology governance, risk, and compliance .
GRC software is a critical tool to simplify these increasingly complex cybersecurity problems. Read on to learn how it can help.
Read Also: Secret Bank Account From Government
Governance Processes And Automation
Contributed by Jerry Layden
Any enterprise operating at scale understands the need for standardization and strong corporate governance. Having served Fortune 50 companies for decades, I have seen the importance that strong governance can have for ensuring that an organization grows in a secure fashion. These business processes can inform how an organization approaches security as well as provide structure to how each line of business embraces certain growth strategies.
Maximise Investments And Integrate Discreet Silos Of Information To Enable Strategic Decision
While cyber security is at the forefront of many senior executivesâ minds, IT and security teams must capitalise on this opportunity by demonstrating prudent risk management measures and proactive support of business initiatives.
This may involve cyber transformation initiatives, and KPMGâs Cyber Governance, Risk & Compliance practice is positioned to help.
Our team helps organisations to work with prominent GRC technology vendors to maximise their investments, and to integrate discreet silos of information to enable strategic decision-making.
You May Like: List Of Government Grants For Individuals In Usa
Foundational Frameworks Transcend Compliance
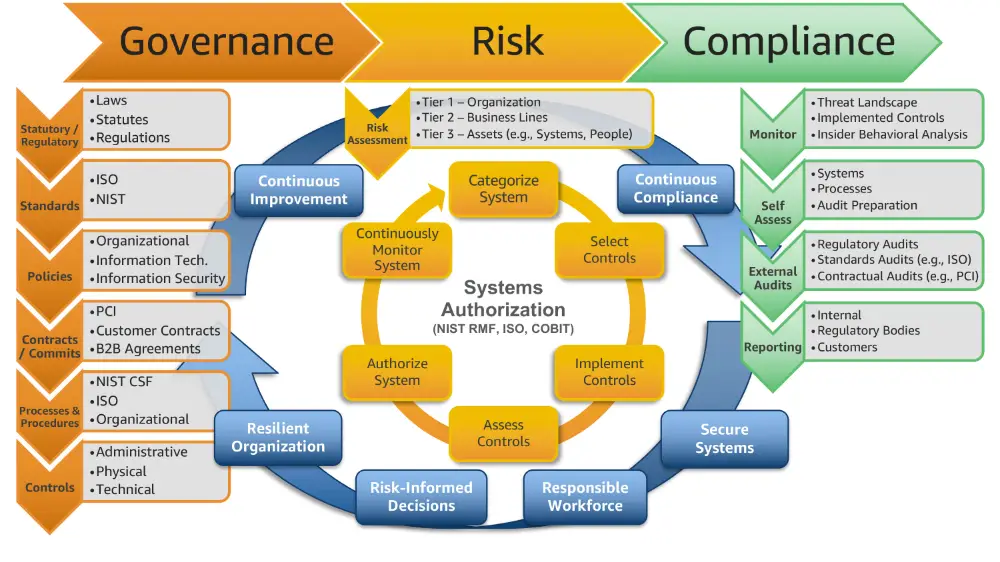
We have covered before how the continued rise of compliance standards is overtaxing cybersecurity teams. Reacting to each new framework and standard as it emerges leaves organizations reeling. The strategy to integrate compliance activities for a cybersecurity program begins with a guiding, foundational framework. In most cases, I recommend the NIST Cybersecurity Framework as that north star. The reason is that, frequently, the requirements that make up these standards are based on the CSF. When security leaders focus on the foundational principles – the CSF – rather than each compliance requirement, the result is significantly less menial effort spent meeting new demands. The optimal way to futureproof your cyber program from new compliance requirements is to focus on the foundational framework that informs them.
How To Scale A Grc System
One size doesnt fit all when it comes to GRC and it doesnt have to The depth and breadth of the systems will vary from business to business. However, regardless of the complexity of a system, it can be transformed or scaled for the adoption of cloud services, emerging technologies, and future innovations, provided you follow best practices.
Also Check: Federal Government Subsidized Student Loans
Unified Governance Risk Management And Compliance
To recap, an integrated GRC platform or GRC software solution is a comprehensive approach to governance, risk management, and compliance, three essential elements of a companies IT or cybersecurity management.
Here at RSI Security, we offer various IT and cybersecurity solutions, including pre-packaged GRC and other bundled services and a la carte services like cybersecurity technical writing or IT and cybersecurity awareness training. To see just how powerful your companys GRC approach can be or optimize your cyberdefenses, contact us today!
RSI Security
RSI Security is the nations premier cybersecurity and compliance provider dedicated to helping organizations achieve risk-management success. We work with some of the worlds leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. With a unique blend of software based automation and managed services, RSI Security can assist all sizes of organizations in managing IT governance, risk management and compliance efforts .RSI Security is an Approved Scanning Vendor and Qualified Security Assessor .
Advanced Degrees And Certification: Educating It Professionals And Executives On The Principles Of Risk Management
The current level of attention to governance and risk management is not something that has come easy to corporations and governments and has required adjustments at every level. Fortunately, many advanced degrees being offered today for both business and technology professionals include guidance on risk management and compliance principles.
Governance issues are a key part of the curriculum in graduate degree programs related to information systems, and it is considered a standard domain when studying cybersecurity at the masters level.
For IT staff that do not otherwise require advanced degrees, certification programs are now beginning to offer specific modules or domains dealing with information security risk management and governance.
The Certified Information Systems Security Professional track has a knowledge domain specifically dedicated to Information Security Governance and Risk Management, which covers:
- Risk management frameworks
- Risk analysis procedures
- Loss/risk assessment formulas and asset valuation
At all levels, IT departments can expect increased interaction with executive boards and corporate risk management specialists in order to adapt cybersecurity policies to address both technical and legal vulnerabilities.
Don’t Miss: Open Enrollment Government Health Insurance
Ciso An Integral Part Of Business Enablement Process
The CISO is an integral component of any business enablement process, even though most companies are still not used to the role. The responsibilities of a CISO goes beyond IT functions to include every aspect of a business function.
A CISOs business enablement responsibility includes the following components
- Cloud computing
- Strategic Planning, Finance, Procurement, and Vendor Manage
Sign-up now to begin your information security journey!
If youre contemplating whether to take the CCISO training program or not, heres why you should. Aside from the reason that the CCISO is written for information security executives that want to be CISOs through improving their skills and knowledge to integrate information security programs with business objectives and goals, the CCISO is essential for the following reasons:
Accredited by ANSI
In case youre not aware of it, the EC-Councils CCISO certification program is accredited by the American National Standards Institute , which is one of the many certification authorities primarily focused on guaranteeing that the information security expert meets the ANSI/ISO/IEC 17024 Personnel Certification Accreditation standards.
Acknowledges the Value of Real-World Experience
Focused on C-Level Management through the Five Domains
For more information, visit our program page now!
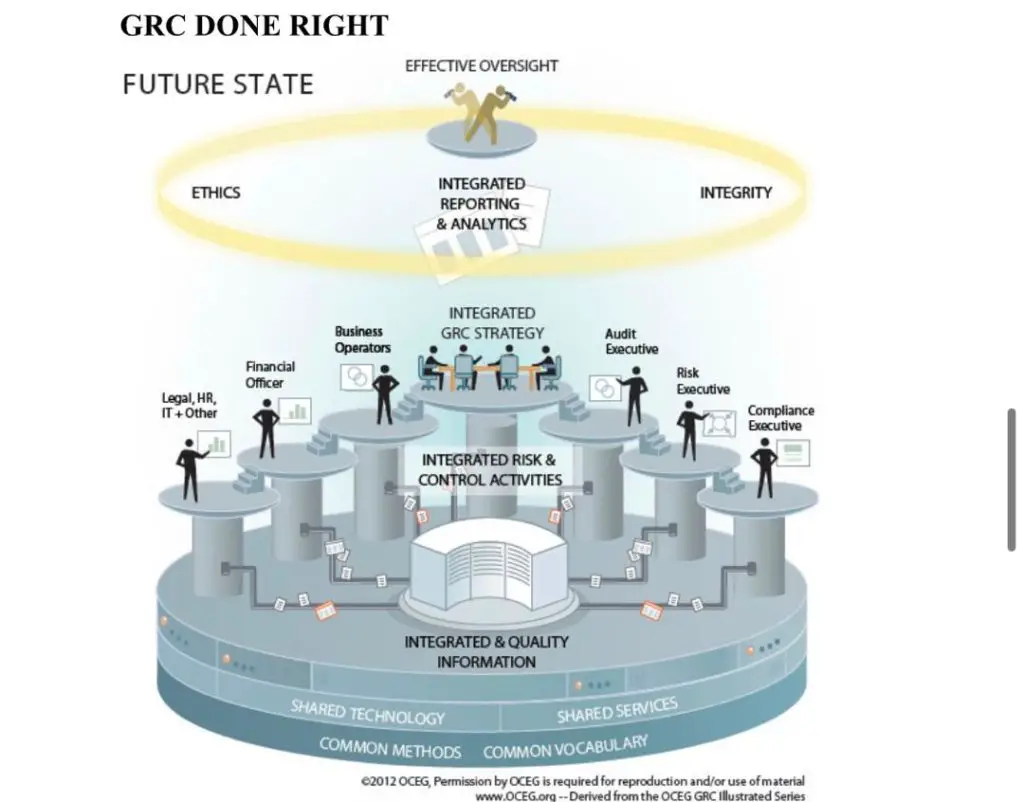
Integrated Risk Management /governance Risk And Compliance
GRC is an organization’s coordinated strategy for managing the broad issues of corporate governance, enterprise risk management, and corporate compliance with regard to regulatory requirements. It describes technology platforms and business processes applied to monitor, inform, and manage an organization’s: 1) governance relative to specific legal, contractual, internal, social, and ethical parameters, 2) comprehensive risk management efforts 3) compliance with relevant industry regulations.
IRM is an approach to risk management that integrates risk activities from across an organization to enable better and more sustainable strategic decision making. Gartner coined the term in 2016 to describe the evolution of technologies and processes beyond what the firm now considers to be legacy GRC approaches. Gartner differentiates IRM from GRC by suggesting GRC is primarily compliance-focused, confined within organizational silos and used by technical practitioners. By contrast, IRM is risk-focused, comprehensive, and used by business leaders. IRM considers comprehensive operational and IT risk posture to drive strategic decision making.
Also Check: Government Jobs No Experience Necessary
Cyber Security And Governance Risk And Compliance
Now before you all start moaning and complaining and leave the post, this post will hopefully explain a few things about keeping your business secure and reducing risk within the business, whilst helping to mature your information security programme.
Now this GRC topic is massive and today were only going to touch the edges of it. So if you want to know more, please drop a comment below the video and let mw know that you want to know more about this.
Now getting into GRC and cyber security within the business, if you didnt already know, both topics go hand in hand with each other and help to form a mature information security programme. Or, if you dont currently have an information security programme, will help to formulate and lay the foundations of an information security framework.
But what exactly is cyber security and GRC?
The Foundation To A Forward
While traditional GRC practices are guided by checkbox compliance activities, integrating governance risk and compliance activities requires doing these activities in tandem. Customizing a risk management program to the enterprise–rather than to general compliance standards–is critical. Structuring goals around a deeper understanding of enterprise risk enables an organization to both prioritize specific risks and threats to the business continuity, as well as convey that information to management.
Also Check: Government Help For Senior Housing
Governance Risk Management And Compliance Management
ISO27001
Our team is fully trained and qualified in ISO27001, which is the international standard for managing information security. This means you can be sure of your compliance, and your customers can feel safe that you are handling their information securely and responsibly.
ASD Essential 8
The Australian Signals Directorate lays out eight essential mitigation strategies as a baseline for your security mitigation. Implemented correctly, the ASD claims that ASD Essential 8 will mitigate up to 85% of the most common cyber threats.
NCSC Cyber Essentials
Cyber Essentials is a Government-backed scheme that provides fundamental controls to protect your businesses from 80% of the most basic cyber security breaches. The five controls include firewalls, secure configuration, user access control, malware protection and security update management.
PCI DSS
The Payment Card Industry Data Security Standard is implemented to ensure your business adheres to the global standard of Visa and MasterCard management to reduce the risk of a card data breach.
This compliance framework ensures you have implemented sufficient information security protections and applies to the Australian financial services industry. At The Missing Link, our team will take measures to ensure your business is resilient against cyber security attacks by managing your security capabilities.
Information Security Manual
Victorian Protective Data Security Framework
Grc Software For It And Security Governance
Governance within a company comprises elements at multiple levels and spans nearly all departments. To understand governance more intuitively, its helpful to break it down into the 4 Ps: People, Purpose, Process, and Performance. People are the parties in control over the companys structure and direction, often represented by or in the C-suite of the companys chief executives. Purpose is the companys objective, usually denoted by policies or agendas. Process concerns how the company intends to achieve its purpose, while Performance is the analysis of that process.
When concerning IT, governance typically refers to the overall management of architecture implementation and the guiding principles by which the team approaches and practices cyberdefense.
Using a unified GRC platform or software solution integrates IT governance into all aspects of its daily operations. The software provides administrative and C-suite stakeholders optimal visibility and control over the most nuanced and intricate IT operations. It also helps ensure that IT integrates with other governance concerns .
Don’t Miss: Government Assistance For Single Person
How To Select A Third
There is a growing need for a consistent third-party governance framework as companies are becoming more decentralized. Nevertheless, your selection of a third-party risk management framework would be dependent on your organization’s use of third-parties, compliance requirements, regulatory requirements, business processes, acceptable level of risk, joint ventures, and the general risk management policy.
Translating Cyber Risk To Stakeholders
Arguably, the most important aspect of risk management is leveraging information to improve the resiliency of the organization. For many business-side leaders, cyber risk is unknown. Yet, in todays digital world, CEOs and Boards must have the ability to integrate cyber risk into the overall enterprise risk profile. This is where risk quantification becomes critical.
This is driving security leaders to examine various risk quantification methodologies. The goal is to match the proper methodology to specific business and reporting requirements and to provide the most value. The optimal risk quantification method will ideally be based upon how senior management is used to seeing risk – business, operational, strategic – to help them roll cyber risk into that mix.
Also Check: Low Interest Government Home Loans
The Objective Of A Security Program
A security program aims to provide a documented set of an organization’s cybersecurity standards, policies, guidelines, and procedures. Your information security program must guarantee the integrity, confidentiality, availability, and nonrepudiation of your client and customer data via efficient security management controls and practices.
How Can Security Ratings Help
Although GRC is more than software, digital tools are often used to keep GRC operations organized and processes streamlined. Large organizations are complex and may often have to meet many compliance requirements, often taking into account quickly-changing regulations.
Similarly, risk changes quickly as well, and IT leaders may need to make decisions about risk quickly having a digital tool that allows IT and cybersecurity leaders to see all risks in real time is important to good decision making.
SecurityScorecard Ratings, for example, allow you to present your organizations business leaders with the most important cybersecurity KPIs for your extended enterprise. Our security ratings use an A-F scale across 10 groups of risk factors and automatically generate a recommended action plan when any issues are discovered. The easy-to-understand ratings scale enables you to provide your C-Suite with the necessary documentation to prove governance over your risk management program to meet increasingly stringent cybersecurity compliance requirements.
You May Like: Government Grant Programs For Individuals
Cipher Offers 20 Years Of Experience To Help You Enhance Your Cybersecurity Posture Reduce Your Information Security Risk And Facilitate Compliance
We can deliver a wide range of capabilities from risk assessments to regulatory and standards compliance around PCI DSS, GDPR, ISO 27001, FFIEC, SOX, HIPAA and many others. We provide our clients with comprehensive recommendations to meet regulatory and compliance requirements, helping to make the entire process more efficient.
Our team of Security consultants work with your organization to develop an actionable plan for optimizing IT resources, ensuring your organization is protected and compliant. We provide detailed reports of any security consulting or assessment performed and use best practices to recommend the next steps.
Our security consultants bring deep and broad industry expertise to help you minimize your investments and build a solid foundation for your strategic cybersecurity programs. We work as part of your internal security team, adjusting our services to fit your needs.
