Improve Compliance And Audit Performance
Identity governance and administrations alloworganizations to verify that the right controls are in place to meet thesecurity and privacy requirements of regulations like SOX, HIPAA and GDPR. They provide consistent business processes formanaging passwords as well as reviewing, requesting and approving access, allunderpinned by a common policy, role and risk model. With role-based accesscontrol, companies significantly reduce the cost of compliance, while managingrisk and establishing repeatable practices for a more consistent, auditable andeasier-to-manage access certification efforts.
Lack Of Enforcement On Iam Controls
Efficient access to resources is provided to employees as your organization grows, its quick and easy to provision and de-provision access to resources en masse, rather than dealing with each machine individually. However, this efficiency creates chaos as you have non-people identities created without visibility into who or what has access to them. This increased risk will create a compliance and security headache.
Could Automation Replace Manual Access Reviews
The fact that policies are already commonly used for things such as Access Management, and the fact that there is no audit standard requesting roles or static entitlements, means that most auditors are used to polices and could well accept the elimination of manual reviews.
The likelihood that auditors will accept that organizations are meeting the requirement of common audit standards is even greater where organizations create, approve, manage, and review policies in structured, well-defined, and well-documented processes. This position can be bolstered even further by adding good processes around identity information quality to ensure the data is always correct.
Although it is unclear how universally the elimination of manual reviews will be accepted by auditors, in the meantime, organizations should aim to achieve as much policy-based automation as possible. This approach will undoubtedly improve the quality of access reviews because there will be far less to do and therefore it will be much easier to do it correctly and efficiently.
While there are other things that can be done to simplify the access review process, such as introducing time-restricted entitlements, policies and automation are the first and most important step towards making IGA simpler as well as more efficient and effective.
Also Check: Concur Government Travel Phone Number
Sailpoints Identity Governance And Administration Solutions
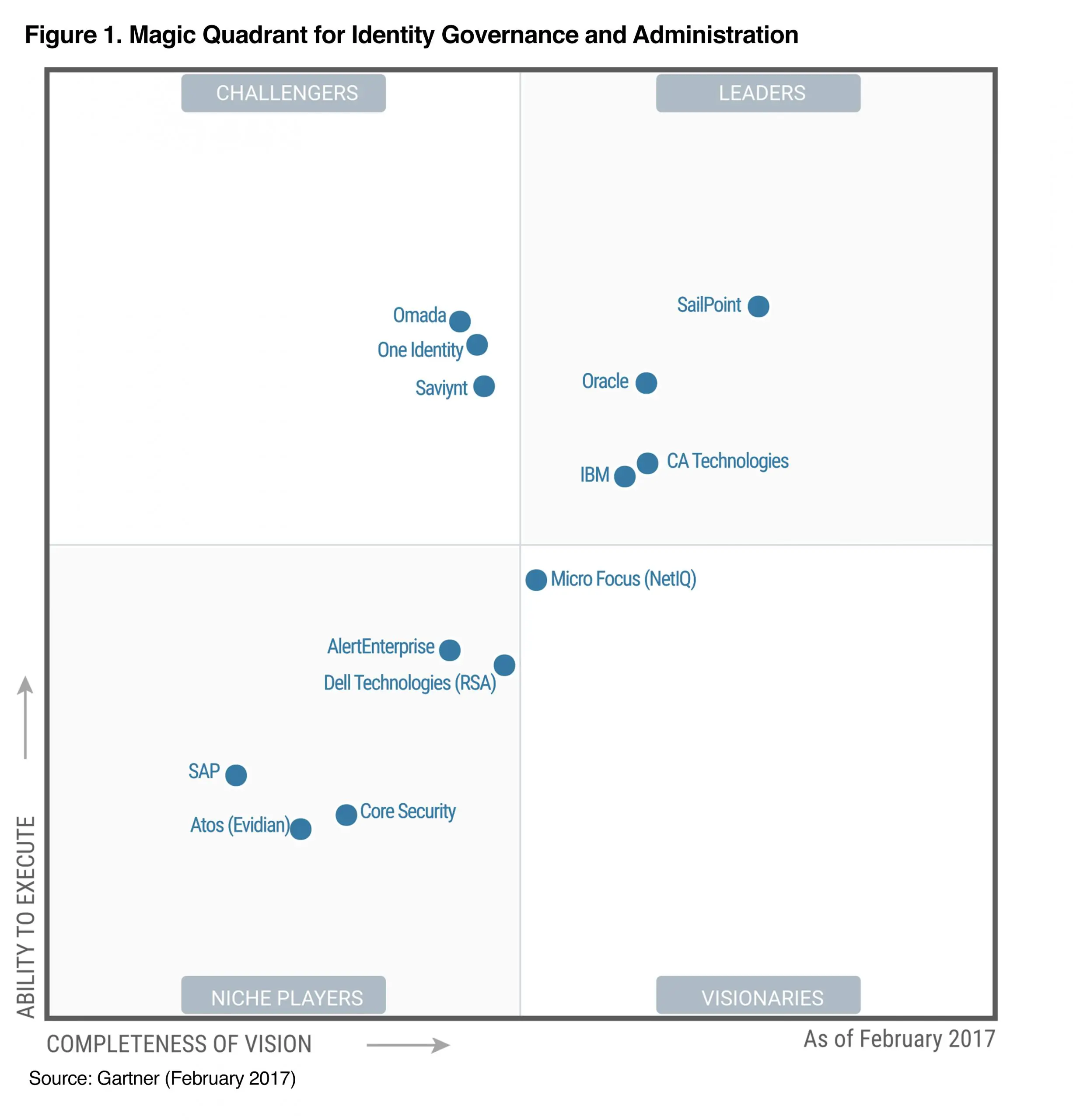
In March, we were recognized as the 2020 Gartner Peer InsightsCustomers choice for IdentityGovernance & Administration . This distinction recognizes the vendorswho are top-rated by their customers, based on a series of customer-submittedreviews.
When it comes to identity governance, no company is better suited to help you solve your unique security and compliance challenges. Learn how we can help you protect your sensitive data, wherever it lives.
Identity Governance in Action
Whats Cloud Identity Governance?
Cloud-based identity governance offers the same security, compliance and automation delivered by traditional enterprise-class identity solutions, coupled with a lower total cost of ownership and faster deployment. Put simply, identity provides the power to make the cloud enterprise secure.
Cloud is transforming the way we work.Organizations must effectively address todays complex business challenges, andtodays enterprise is becoming a cloud enterprise. While companies are becomingmore comfortable with moving strategic and mission-critical applications intothe cloud, it can feel overwhelming to consider solutions like identity as aservice . They often avoid identity governance because they believe theylack the budget, time or skilled identity resources required to implement it.However, these are no longer inhibitors to reaping the benefits of identitymanagement.
Isnt identity governance software only available on-premises?
Is IGA only for big businesses?
Key Capabilities Of Your Identity Governance And Administration Solution
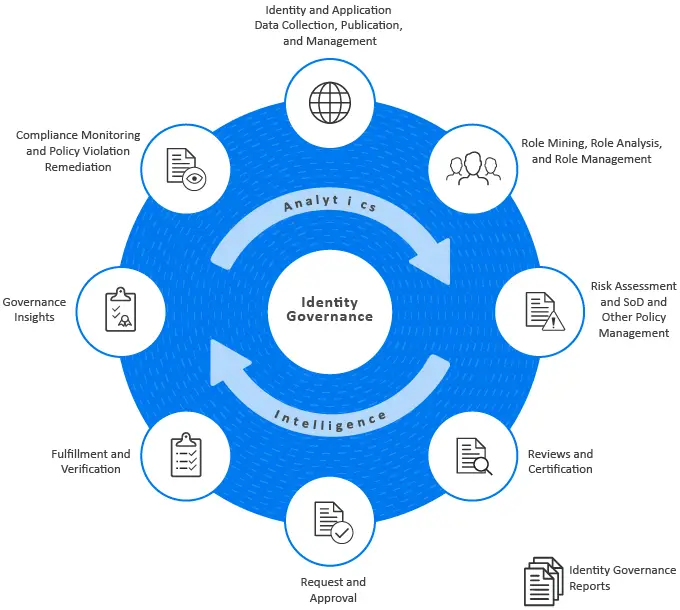
According to research firm Gartner, identity governance and administration solutions are defined as a means to manage digital identity and access rights across multiple systems and applications. That may sound simple on the surface, but the sheer size of the modern enterprises digital environment requires a similar level of complexity from your identity governance and administration solution. IGA is necessary to correlating and monitoring the disparate identity and permission data throughout your enterprises network, especially the granting and removal of permissions of employee identities.
Furthermore, identity governance and administration solutions are also important for fulfilling regulatory compliance mandates. Granting inappropriate access and permissions to employees can lead to expensive and exhausting violations and leave you open to security vulnerabilitiesand even more expensive data breaches.
But what are the key features of an identity governance and administration solution? What should your enterprise prioritize in the selection process? What are the key capabilities an identity governance and administration solution needs to offer to be in the running as the right choice for you?
An enterprise-level identity governance solution must have:
Don’t Miss: Digital Transformation In Government Harvard
Iga Vs Iam: What’s The Difference
Because of overlap in identity, access-based, and governance solutions, many wonder about the difference between IAM and IGA. They also question how IAM differs from privileged access management , which is a more specific type of IAM access that focuses on privileged users. Broader IAM focuses on authenticating users identities and authorizing them to access data. Authentication relates to how systems verify users based on identifying criteria, from passwords to multi-factor authentication or biometrics. Authorization relates to how administrators control access to data within apps.Broader still, IGA encompasses the processes and enforcement mechanisms of IAM. It includes the policies that firms use to monitor security in their information systems, addressing business, legal, regulatory, and technological challenges. In contrast, IAM refers to the technologies companies use to manage access to their systems. IAM is based on privileges and comprises the tools leaders use to carry out their broader identity governance and administration priorities.
Streamline Identity Governance And Administration With Sonrai Dig
With organizations accelerating workloads to the cloud, Sonrai Security can help you mitigate cloud risk related to overly permissioned identities. Sonrai can help your organization work towards the least privileged model. Sonrai Security provides actionable visibility to cloud identity and entitlement exposures so organizations can take corrective action. The solution makes identifying and reducing risk simple by offering trust relationship visualizations for cloud identities, roles, permissions, and resources. With Sonrai, security teams see excess permissions that areleveraged to create kill chains and attack paths, move laterally, and maintain persistence within the public cloud environment.
Don’t Miss: Names Of Free Government Phones
Reduce Risk And Strengthen Security
Compromised identities caused by weak, stolen ordefault user credentials are a growing threat to organizations. Centralizedvisibility creates a single authoritative view of who has access towhat, allowing authorized users to promptly detect inappropriate access,policy violations or weak controls that put organizations at risk. Identitygovernance solutions enable business and IT users to identify risky employeepopulations, policy violations and inappropriate access privileges and toremediate these risk factors.
Streamlined User Identity Lifecycle Management
User management has evolved dramatically as many organizations have relaxed work-from-home policies users used to primarily be in the office every day which allowed for easy, secure access to their devices. When onboarding and offboarding, managers and IT personnel typically had direct physical access to the resources that they needed to manage and change, but now thats not necessarily the case. This means that new solutions need to be leveraged to maintain the proper level of control over users, devices, networks, and other IT resources, and this is where an IGA solution becomes integral.
An IAM solution with IGA capabilities can provide the following benefits:
Also Check: Government Benefits For Seniors Over 60
What Is Identity Governance And Administration
Identity Governance and Administration , also known as identity security, is at the center of IT operations, enabling and securing digital identities for all users, applications and data. It allows businesses to provide automated access to an ever-growing number of technology assets while managing potential security and compliance risks.
Identity Governance in Action
Lack Of Visibility Into Entitlements
Every enterprise needs to know what their user and machine identities can access and what they can do with their access. Managing entitlements or permissions for identities must extend beyond people. Each identitys effective, end-to-end permission should be known regardless if it is a person or non-person identity. IGA focuses only on the persons identity, which can leave massive blind spots. Can it take on or assume another identity? If it can, it now takes on the permissions of that identity. What can it do with these new permissions? If we looked only at the first level request, we would be blind to everything else. This is where organizations get into trouble and where Cloud Infrastructure Entitlement Management is crucial.
You May Like: How To Refinance Government Student Loans
Identity Governance & Administration With Strongdm
StrongDMs identity management helps organizations control the chaos of provisioning new users and platforms. It provides centralized identity management, allows for an expanded suite of automations, and ensures auditable access for all, exactly when they need it. StrongDM combines the auditing organizations’ need for compliance with identity management solutions made simple. Compliance officers can view controls, assemble evidence, and save time when compiling access logs for compliance certification. IT specialists can automate access management, freeing up time to create more business value, all while eliminating unauthorized access.
Provide A Variety Of Options For Self

The Gartner IGA Magic Quadrant recognizes enterprise password management software as critical to an identity management solution. The IGA password management examines password management solutions based on help desk ticketing integration, self-service password reset capabilities, enterprise password synchronization, event logging, and compliance reporting.
The Avatier Identity Management Software Suite automates help desk ticketing. AIMS offers a variety of self-service password reset options. It lets business users simultaneously synchronize password for enterprise accounts and cloud subscriptions.
The AIMS IGA Magic Quadrant password management solution internationalizes to 30 languages and dialects. It connects to over 90 enterprise systems, applications and databases. AIMS makes mass enrollment, immediate user adoption and security possible.
Don’t Miss: Government Grants For Hot Water Heaters
Does Your Org Need More Than An Iga Solution
As traditional provisioning solutions struggled to keep up with increasing identity demands and regulations, many organizations turned to identity management solutions to address these challenges. The digital landscape was evolving rapidly as the introduction of software-as-a-service applications, and digital solutions began sweeping through the enterprise landscape. The transition to these technologies means that internal user identities are now used to access new external cloud-based applications and systems outside the enterprise network. The result was a tangled web of access to internal and external systems, a disorganized mass of accounts for the workforce, consumers, and partners, and varying access levels across multiple environments.
Because of these new and ever-growing challenges, identity management solutions do not meet compliance regulations to ensure user access is reviewed, allowed, and/or revoked periodically. As a result, organizations would manually create and check user access certifications via spreadsheets distributed by email to business line managers annually or biannually for review and approval. Yet, with the exploding number of internal and external user identities, systems, and cloud applications, this process was no longer a scalable or viable option. A new approach was needed, with pressure mounting on organizations to achieve regulatory compliance.
Now an approach with both person and non-person identities is possible.
Importance Of Identity Governance And Administration
The importance of identity governance and administration is paramount in highly regulated industries where there is a need to prove compliance e.g. large corporates, financial institutions, law firms and healthcare providers. However, it is a mistake to think that it is only big companies and those with compliance requirements that need identity governance and administration. These days data breaches are all too common, and are as likely to happen in smaller businesses or non-regulated industries. As data managers, organizations of all sizes need to ensure the personal details of employees, customers and other stakeholders are kept in a safe and secure way. Having a robust, automated identity governance process can provide the backdrop by which businesses can take back control and satisfy the need for regular monitoring and auditing. Utilising specially designed identity governance software can greatly reduce the amount of IT hours spent on these tasks and ensure that human error is removed from the process.
Also Check: Us Government Jobs For Green Card Holders
Enterprise Identity Cloud Scores The Highest Possible Scores In 5 Of 7 Competitive Criteria Categories Evaluated
Saviynt Enterprise Identity Cloud unifies five core identity security capabilities onto a Converged Identity Platform that enhances and simplifies identity management for organizations looking to modernize their existing identity program or implement their first. By adopting a unified identity strategy, organizations can see dramatic productivity gains while boosting the user experience and easing administrative headaches.
Since its introduction as the industrys first SaaS-based IGA solution, Saviynts continuing advancements in IGA capabilities continue to be recognized in the industry.
Identity Governance And Administration
Complete, business-driven governance for identity, data andprivileged permissions
See how you can implement enhanced identity governance and administration capabilities to better manage all users for your on-prem, hybrid and cloud environments. Satisfy audit and compliance initiatives, and easily provide management with a clear view of your governance posture. Meet attestation and recertification requirements with ease. Quickly access data about internal, external and privileged accounts that have access to your on-premises, cloud and hybrid applications to easily pass audits.
Read Also: Free Government Car History Report
Create A Strategic Plan
Once you’ve inventoried your identities and mapped their access pointsa process infinitely more efficient if it’s automatedyou need to make decisions about which permissions to keep and which to change.
Each organization needs to determine its priorities. You should consult with all stakeholders and create a strategic plan for identity management, making sure you include all of your systems, cloud-based and on-premises. Create a common decision-making framework based on risk.
Many companies like to start with privileged accounts, including root accounts, which belong to administrators and can get into your critical systems and make changes. Because these accounts can do so much, they are a high-value target for attackers.
Privileged accounts should be limited in both number and scope. Many organizations learn the hard way that they are not. At a healthcare company we work with, a root account holder working on the claims database made an error that shut down the company’s operations for an entire day.
It was just a mistake, but it led the company to look into access privileges. It found 100 other account holders who could get into this same sensitive databasefar more than necessary.
Any account with unneeded access privileges is a security liability. The more sensitive the information they can get to and the more they can do with it, the higher the risk.
Who determines whether someone should have access to an application or database?
Sap Cloud Identity Access Governance
SAP is a multinational software corporation that develops enterprise software designed to simplify the management of business operations and customer relations. SAP has a history of offering IGA-based products, including SAP Cloud Identity Access Governance which is SAPs latest innovation in access governance. This is a multi-tenant solution built upon the SAP Business Technology Platform and SAPs proprietary HANA database.
This solution includes a range of useful key capabilities, including the ability to continually run access analysis and to support access compliance management through the use of real-time insights. Admins can also leverage configurable, predefined policies and rules regarding access, as well as dynamically update user access as business needs change. The solution lets admins more accurately assign user access and easily alter access dynamically. It also offers guided remediation for risk management and dashboard-driven management interfaces, analytics, and intelligent and visual prompts to pinpoint business critical issues.
With SAP Cloud IAG, organizations can extend their control and risk management capabilities, including extending access control to enterprise users and applications from any location and on any device. The solution also allows admins to detect and remediate segregation of duties and any critical risk to on-premises and cloud systems, as well as simplify the process of managing compliance using preconfigured audit reporting.
Also Check: Government Land For Sale Montana
Manage Identities Access Provisions And Business Services With An Online Store
Avatier Identity Management Software Suite offers a holistic solution for enterprise identity management operations. AIMS automates regulatory compliance and IT audit reporting while enabling self-service user provisioning, access governance and password management.
AIMS position in the Gartner IGA Magic Quadrant showcases how organizations, educational institutions and government agencies deliver a unified solution. For fulfilling access requests, identity audits and compliance reviews, Avatier offers a comprehensive toolset to enable workflow automation and self-service delegated administration across enterprise systems, applications and cloud computing services.
With its innovation leading vision combined with proven execution, Avatier demonstrates how to lower operational costs and enhance security through more efficient operations.
Strong Iga Starts With Strongdm
Today’s organizations rely on a complex landscape of cloud-based applications and global employees. These changes have benefited businesses and introduced risk, just as they have added to an evolving glossary of infrastructure access terminology. Ultimately, IGA solutions address the access-management needs of a cloud-based architecture as they embrace this complex, expanding ecosystem. Explore how easy it can be to manage cloud access and maintain compliance with a free, 14-day StrongDM trial.
Read Also: Government Funded Pre Kindergarten Programs
What Specific Value Does A Complete Identity Governance And Administration Environment Have Over Other Solutions
While identity governance and administration manage entitlements and deliver strong attestation for the security auditors, it has the potential to be a foundational component of an organization’s identity and access management infrastructure:
- Entitlement management is the fundamental element of any organization’s least privilege strategy. Least privilege security helps protect against internal threats as well as limit damage when someone’s credentials have been compromised and exploited. When done correctly, it can be used to guide and invoke identity life cycle actions rather than work independently of it.
- One of the steps of onboarding resources on a governance platform is defining their risk and risk criteria. Proper risk definitions of sensitive resources provide accurate information to the approvers and reviewers. They can also be consumed by the risk service to direct adaptive access management actions. Too often, criteria used for session-based access controls for potential authentication and authorization actions are limited to the user’s context . Factoring in the risk of the resource itself offers a more granular and effective approach to adaptive access that can increase security while optimizing the user’s experience. By limiting the number of times, a user is interrupted for multi-factor authentication, friction is reduced, and the user’s experience is optimized.
