Iga Systems Implementation Workflow
The implementation of the Identity Governance and Administration solution, like any IT system that automates business processes, cannot be done without serious changes in the business processes of the organization. Moreover, here we are talking mostly about personnel management, including identity and access management. The maturity of these processes directly affects the quality of the implementation of the IGA system. Organizations planning to implement and further develop IGA system should systematize and structure these processes in advance. Already at this stage, distortions can be identified, which are to be fixed best before the IGA system implementation itself.
At the preliminary stage of implementation, the organization must go through external or internal consulting, the results of which should formalize the appropriate access management processes, and refine the existing information systems, first, the personnel management infrastructure. A good result at the end of the consulting stage is the development of a role-based access control model.
Assessing the relevance of the system to the existing IT landscape in the organization, its functionality and flexibility are the key principles to be considered when selecting an IGA system. The price factor is also important.
The need to introduce IGA in the organization is subject to certain criteria, as follows:
Strengthen Your Business With Iga
An identity governance and administration solution can help businesses to overhaul their security approach by reducing risk, strengthening their identity access management, and improving their compliance and audit performance. It can also help them become more efficient and productive, and reduce their costs by minimizing the time spent on administrative and automating labor-intensive tasks.
To learn more about identity governance and administration, check out our Identity 101 page.
Managing The Fulfillment Process
Fulfillment target configuration, application setup, and catalog update setup by the Global or Fulfillment Administrator drives how requested changes are fulfilled. The changes can be fulfilled manually, by a help desk service, or sent to Identity Manager, which automatically makes the changes or initiates external workflows. For manual fulfillment processes, the Global or Fulfillment administrator specifies individuals or groups as fulfillers responsible for making the requested changes. For example, your Help Desk group might be assigned to fulfill the changeset.
Fulfillment Administrators also monitor the fulfillment process, and reassign manual fulfillment items if needed. Identity Governance provides the following status conditions for fulfillment items:
-
Error or time out
-
Ignored
-
Retry
When the fulfiller confirms the fulfillment activities, Identity Governance updates the status of the fulfillment item. After the administrator collects and publishes application sources, Identity Governance again updates the status of these fulfillment items. Global and Fulfillment Administrators and Auditors can access the Fulfillment Status page to view the status of all fulfillment items. For more information about fulfillment targets and fulfillment status, see Section 14.0, Setting up Fulfillment Targets and Fulfilling Changesets.
Recommended Reading: How Do I Get A Grant To Start A Trucking Company
Efficiency And Operational Cost Reduction
Evidian Identity Governance and Administration allow customers to manage easily their users Identity Life Cycle without imposing tedious and time-consuming administration tasks tasks that can also lead to human errors.
Organizations can speed up the delivery of access to business applications with the solutions automatic provisioning capabilities, and improve user productivity by simplifying access to authorized applications wherever they may be. Process automation and self-service features allow to reduce administration costs and optimize the return on investment of the solution.
Evidian Identity Governance and Administration also supports hybrid environments in a secure and cost-effective way.
Customers can manage accounts without having to worry about synchronization delays between the on-premises and Cloud identity sources.
Moreover, since applications licenses are also managed through the security policy, Evidian Identity Governance and Administration customers can also manage license costs and take advantage of the reporting features for auditing costs.
How Do Users Interact With Oracle Identity Governance
Oracle Identity Governance provides an end-user interface, called Identity Self Service, and a system administrator interface, called Identity System Administration. Both end-users and system administrators use the web browser to log on to Oracle Identity Governance.
The interface for end-users is used:
-
To manage your user profile, passwords, challenge questions, and account passwords.
-
To view, request, and approve access for self and others, certify users, and process policy violations and manual provisioning tasks.
-
To setup organizations and administration roles and to configure delegated administration. It is also used by delegated administrators to create and manage users, organizations, and password policies.
The interface for system administrators is used:
-
To define workflow policies, home organization policies, and user capabilities
-
To manage the schema of system entities, such as user, role, and organization
-
To manage provisioning end-points and the schema of the supported objects
-
To import/export Oracle Identity Manager configuration objects
-
To install/uninstall/upgrade connectors
You can also use the REST services to either create your own user interface or to integrate other applications with Oracle Identity Manager.
Developers can also use:
Also Check: City Of Las Vegas Government Jobs
Reviewing User Access Requests
The access request/review/certification process often leads to unauthorised access arising from overwhelmed IT administrators and managers who automatically approve all requests or rubber stamp requests. Under the NY SHIELD Act, an organisation can determine that the unauthorised access posed no risk to the individual. Using intelligent analytics and automation allows you to create risk-based, context-aware access controls that use best practices ABAC. Using these policies, intelligent analytics can create designated approver notifications, delegation rules, SOD rules, and escalations that streamline NY SHIELD Act compliance.
What Is Identity Governance
Identity governance is a framework that caters to businesses’ needs of gaining better visibility of user identities and access controls while complying with standards like the Sarbanes-Oxley Act , Health Insurance Portability and Accountability Act , and other regulations.
Identity governance merges with identity administration to constitute the identity governance and administration approach, which caters to credentials and entitlement management, and de-provisioning while providing support in auditing and compliance requirements. Usually, IG systems are deployed above identity and access management solutions, helping organizations define, manage, and review identity and access management policies. They enable you to adhere to compliance requirements by mapping IAM functions to regulatory standards and conduct user access audits.Identity governance solutions enable you to have a distinctive overview of identities and access privileges of users, associated risks, and the possible impact of a policy violation.
IGA systems allow administrators to:
- Segregate the duties of a user to prevent an individual from having access to privileges that may pose a risk.
- Streamline the process of reviewing and verifying user access to different applications and services.
- Define and manage user access based on their roles in the organization.
- Analyze reports to better understand the issues, optimize, and adhere to compliances.
You May Like: How To Get A Grant To Start A Trucking Business
Take Advantage Of Automated Micro
Access reviews and certifications should be more than just periodic events across your organization. They should occur continuously to ensure you are monitoring for policy violations in between audit cycles. Micro-certifications are essential to organizations that manage a complicated landscape of user rights, permissions, and accounts. And they enable companies to ensure that users have the right accessat all times. Make sure you know who has access to your organizational systems, data, and applications by using micro-certifications to better meet compliance mandates, deter insider threats, and more effectively manage access within your company continuously.
How Does Identity Governance Work
Your job as an IT professional involves balancing two competing objectives. On the one hand, you must support productivity with quick access to appropriate files. On the other, you must defend your company’s private and sensitive documents. And you must work quickly, so you keep the trust and support of your superiors.
Identity governance solutions make your job easier.
Think of identity governance as an umbrella term that encompasses many smaller processes. They all work together to offer robust security while maintaining access.
Identity governance products typically contain features such as:
- Administration. You determine valid users within the system, and you can delete them as needed.
- Analytics. Reports help you understand when pieces of your network are accessed, when they are changed, and who is doing the work.
- Identity management. You ensure that people verify that they are who they claim to be before they gain access.
- Role-based administration. Access to large swaths of the system is determined by the work people do within specific job titles.
When complete, your system helps you understand who has access to what within the server. Rules come from that understanding, and they help you spot early warning signs of security failure. Your system also helps you build strong rules regarding approval processes and oversight roles.
You could use your identity governance system to provide reports regarding:
Don’t Miss: City Of Las Vegas Government Jobs
Enable Stakeholders To Make Informed Decisions
IGA approach enables stakeholders to gain visibility on a user’s activities in terms of access to applications and databases. It empowers stakeholders with metrics related to information and application usage and allows them to control access permissions and modify them whenever needed. You have to keep track of roles and access privileges consistently with every change in a user’s lifecycle within your organization. This is where role-based access control is important as people switch jobs, get promotions, and so on. For instance, if an employee transfers to a different vertical in a company, their access privileges, and permission should reflect the same without any delays.
Configurable Logging Analytics And Reporting
Lots of activity related to identity and access management happens within your companys systems every day. People log in to applications, access information, and perform all sorts of transactions. Identity governance and administration systems with a highly complete set of features will capture information from various log files and perform analytics and reporting to help summarize and interpret this activity for you. In practice, this set of functionality overlaps quite a bit with log management systems .
Don’t Miss: Government Jobs In Las Vegas Nevada
Request And Approve Access To Resources
Keep teams productive by providing accurate, timely access to applications and data across your diverse IT landscape. With Identity Governance, your IT team and application owners no longer need to manage entitlements in each application and platform. You’ll have a user-friendly, self-service access request and approval system, backed by automated fulfillment for the most commonly used applications.
What Is Identity Management
Identity management is the organizational process for ensuring individuals have the appropriate access to technology resources.
This includes the identification, authentication and authorization of a person, or persons, to have access to applications, systems or networks. This is done by associating user rights and restrictions with established identities.
Managed identities can also refer to software processes that need access to organizational systems. Identity management can be considered an essential component for security.
Identity management includes authenticating users and determining whether they’re allowed access to particular systems. ID management works hand-in-hand with identity and access management systems. Identity management is focused on authentication, while access management is aimed at authorization.
Don’t Miss: City Of Las Vegas Government Jobs
Elements Of Iga Systems
Identity governance and administration tools help handle user identity lifecycle management. IGA systems generally include these elements for identity administration:
- Password management Through tools like password vaults or, more often, Single Sign-On , IGAs ensure users dont have to remember many different passwords to access applications.
- Integrations Connectors to integrate with directories and other systems that contain information about users and the applications and systems they have access to as well as their authorization in those systems.
- Access request management Workflows that make it easier for users to request access to applications and systems and get approvals.
Bringing Iam Components Together
Its important to recognize that many of the IAM components explained above often overlap. For instance, an IAM solution providing single sign-on ties together account management, access controls, authentication, and password management:
- Account Management: An end user requires accounts for the SSO solution and all connected resources based on their current job role. The SSO solution may also provide self-service for a user to request accounts for and access to additional systems and applications.
- Access Controls: The end user may access specific IT resources from the SSO solutions dashboard based on the rights associated with their digital identity. Access controls may also enforce when and how the end user may access those resources.
- Authentication and Password Management: To access their SSO dashboard, the user must verify themselves at an initial authentication Once authenticated, the SSO solution verifies the users identity to all connected systems and applications. While this is typically carried out via secure SSO protocols and tokens, the encryption of credentials for some connected resources is one element of password management.
Ultimately IGA and IAM go hand-in-hand and are critical to every organization. Even without automated solutions or dedicated efforts, IGA and IAM still exist in practice to enable employees, increase security, and reduce the risk of compliance violations.
Don’t Miss: Government Jobs Vegas
Policy Enforcement And Segregation Of Duties
Segregation of duties is the desire to prevent a person from performing a combination of risky activitiesfor example, initiating and approving a wire transfer of money from your company to their own bank account. Identity governance and administrations that have this functionality provide the ability to create rules that prevent defined types of access from being granted to the same person. Many products also perform discovery of violations based on these rules to help you know when a segregation of duties conflict needs to be remediated.
In practice, segregation of duties is very difficult to implement and enforce because you need to have a lot of information about the specific business functions that entitlements allow people to perform, as well as a broad business knowledge across systems of which actions should not be combined. The ability to execute segregation of duties varies significantly across IGA systems and is largely dependent on the applications your organization uses and the level of business process understanding you have.
Identity Governance And Administration Compliance For Ny Shield Act
20 September 2019
How are New York organizations preparing for NY SHIELD Act to better protect private and personal information?
To increase theft prevention for New York State consumers, the legislature enacted the New York Stop Hacks and Improve Electronic Data Security Act. Referring to the previous data breach notice law as outdated, the new regulatory compliance requirement becomes effective in 2020. Creating a holistic approach to Identity Governance and Administration with intelligent analytics can ease the burdens associated with meeting the NY SHIELD Act compliance mandates.
Also Check: Government Grants To Start Trucking Business
Health Insurance Portability And Accountability Act
HIPAA establishes national standards for processing electronic healthcare transactions, requires covered entities to implement secure electronic access to health data, and mandates compliance with privacy regulations set by the U.S.
Department of Health and Human Services . The HIPAA omnibus rule provides guidelines for business associates of covered entities.
IAM can assist organizations in ensuring HIPAA compliance with access and identity management. That includes the use of federated identities, single sign-on , least privileges, regular credential rotation, multifactor authentication, and role-based policies for account provisioning and de-provisioning.
Processes Become More Scalable
After seeing how IGA solutions streamline user identity lifecycle management and reduce risk while improving compliance and security, its easy to see how they can help your organization scale over time. Those two main benefits working together allow for scalability that wouldnt exist otherwise. Sticking to manual processes and having little to no visibility into your IT systems doesnt provide any good opportunities for scaling properly, and if youre going to scale, whether its now or later, you need to have the processes, workflows, and automations in place before doing so successfully.
Some ways that IGA solutions facilitate organizational scaling are through:
- Reduced operational costs due to automated processes that require less of a time commitment from IT admins
- Efficient access to resources is provided to employees, meaning that as your organization grows, its quick and easy to provision and deprovision access to resources en masse, rather than dealing with each machine individually
- Inherent compliance improvement is found within IGA tools, and tools that improve compliance and reduce risk are ones you want to keep on deck as you grow, as compliance only gets more difficult as your organization gets larger and harder to manage
Recommended Reading: Government Jobs For History Majors
Importance Of Identity Management
The main goal of identity management is to ensure only authenticated users are granted access to the specific applications, systems or IT environments for which they are authorized. This includes control over user provisioning and the process of onboarding new users such as employees, partners, clients and other stakeholders.
Identity management also includes control over the process of authorizing system or network permissions for existing users and the offboarding of users who are no longer authorized to access organization systems.
ID management determines whether a user has access to systems and sets the level of access and permissions a user has on a particular system. For instance, a user may be authorized to access a system but be restricted from some of its components.
Identity governance, the policies and processes that guide how roles and user access should be administered across a business environment, is an important aspect of identity management. Identity governance is key to successfully managing role-based access management systems.
Identity Governance And Administration
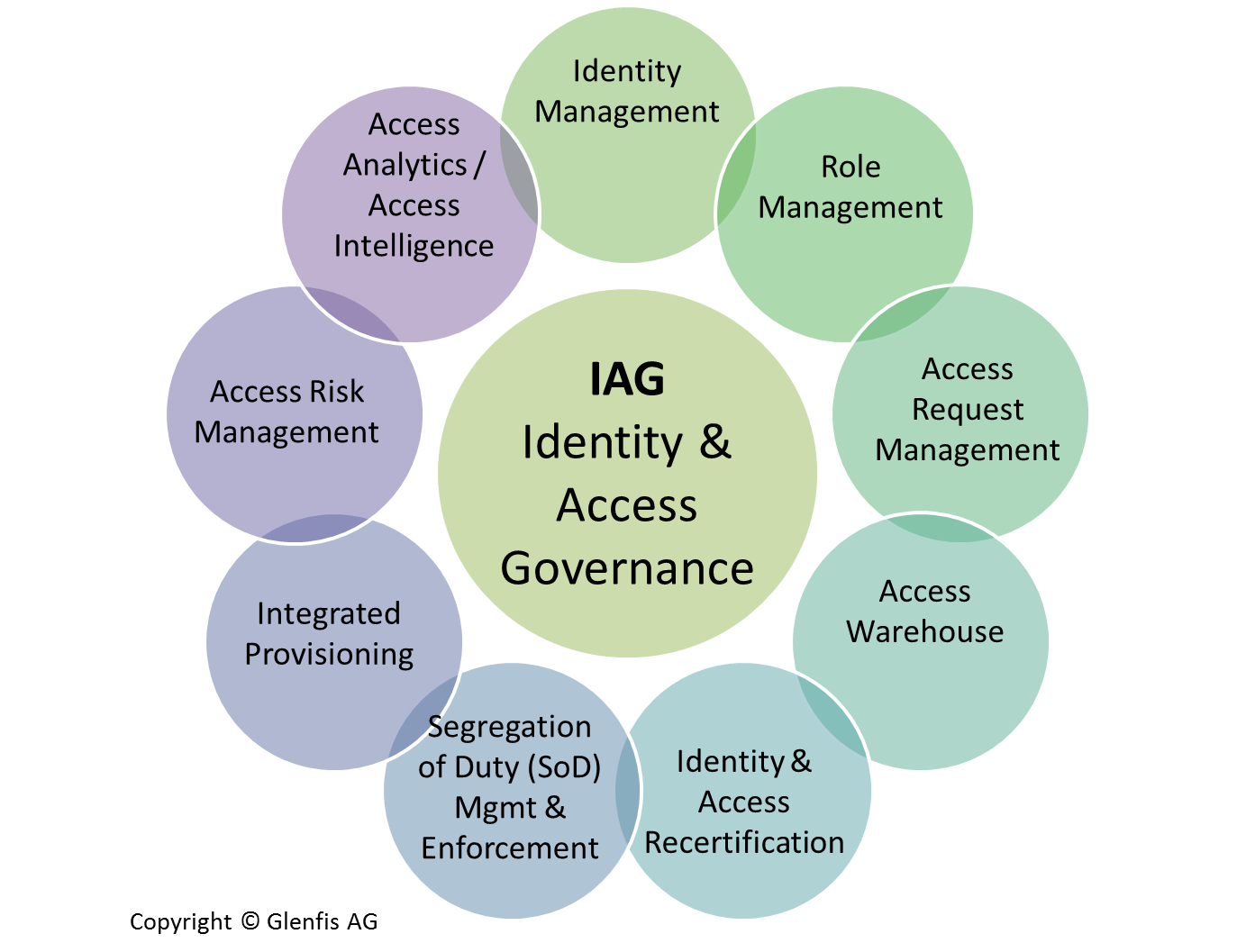
Complete, business-driven governance for identity, data andprivileged permissions
See how you can implement enhanced identity governance and administration capabilities to better manage all users for your on-prem, hybrid and cloud environments. Satisfy audit and compliance initiatives, and easily provide management with a clear view of your governance posture. Meet attestation and recertification requirements with ease. Quickly access data about internal, external and privileged accounts that have access to your on-premises, cloud and hybrid applications to easily pass audits.
Don’t Miss: Government Jobs For History Majors