Improve Security Using Iga And Pam
Challenges to staying on top of user identity will only continue to grow as the workforce spreads across physical space and insists on using types of multiple devices. In parallel, data assets continue to shift into new hosting modes like cloud and hybrid architectures. The very idea of a user itself is evolving, with automated, AI-driven systems now performing a range of tasks. In this environment, the need for tighter controls over user identity is essential. IGA and PAM working together provide a solution. They give administrators an agile, efficient way to govern user identity and access rights.
Interested in learning more about the WALLIX Bastion PAM solution and how it can connect with your existing IGA processes? Get in touch.
Iga And Pam Together: Mutual Reinforcement
Unifying IGA and PAM enables a central locus of policy definition and enforcement for all forms of identity management. With an integrated IGA and PAM approach, a request for privileged access can be managed within the parameters of the organizations IGA policies. All access requests and grants are part of a single access control chain. Both basic user and privileged user access becomes more easily auditable.
There are a variety of approaches to achieving the mutually-reinforcing relationship between IGA and PAM. The goal should be to build one authoritative identity store. With APIs, the two solutions can facilitate automated workflows to process all access requests, including requests for privileged access.
Iga Is Only Relevant To Big Businesses
Thats inaccurate. Managing access controls and having a robust process for managing access to your systems is important regardless of your size. For small businesses that are looking to scale and grow their customer base, implementing IGA processes can ensure that they are proactively compliant with regulations that might target larger companies.
Don’t Miss: Government Loans For College Students
The History And Evolution Of Identity Governance And Administration
The need for identity governance and administration solutions emerged alongside stringent data regulations such as the Sarbanes-Oxley Act and the Health Insurance Portability and Accountability Act , which required improved transparency and data management. Supporting organizations in these efforts, IGA systems were designed to give organizations better visibility into identity and access privileges and provide better controls with which to detect and prevent inappropriate access to their resources.
The importance of IGA security was recognized when, in 2012, Gartner named it the fastest-growing sector of the identity management market. Then, in 2013, the analyst house launched its first Magic Quadrant for Identity Governance and Administration, which merged its two existing Identity Governance and Identity Administration categories, further solidifying it as an area of priority for organizations.
The Role Of Identity Management In Data Governance
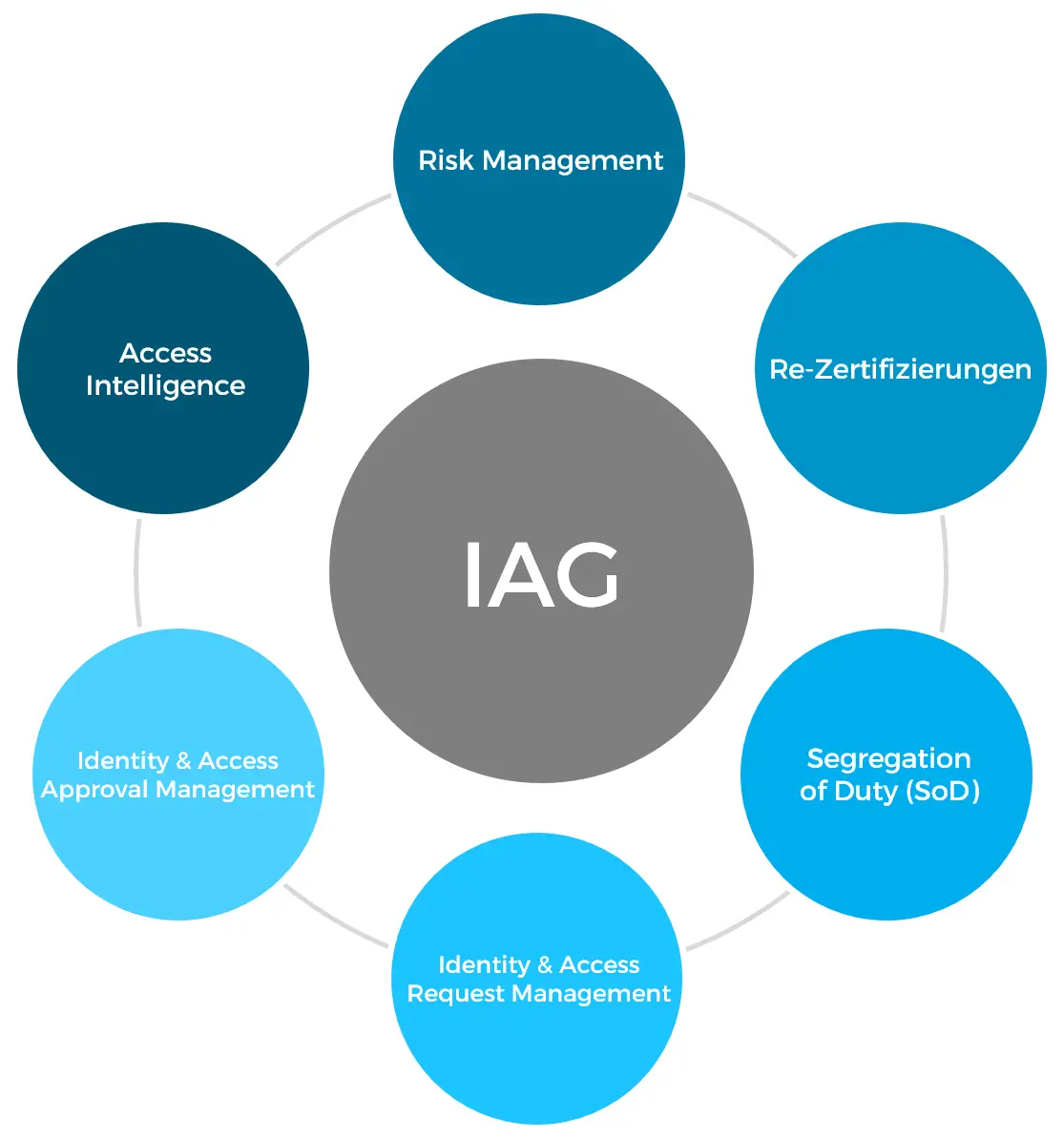
Data governance is the sum of policies, processes, standards, metrics, and roles that ensure that data is used effectively to help an organization realize its objectives. Data governance establishes the responsibilities and processes which ensure that the data being used across the organization is not only of high quality but is also secure. As such, it defines who takes what actions, on what data, in which situations, and using what methods.
Thus, a well-designed data governance strategy is critical for any business that works with a lot of data, as it ensures that the organization benefits from consistent processes and responsibilities.
Today, most organizations work with big data which comprises of sensitive customer and company information. And because a lot of people may have access to this data, it is imperative that you have data and identity management policies to avoid this information falling into the wrong hands or being used for unintended purposes. Cyber-crime is on the rise and is costing organizations millions to mitigate its effects. Effective data governance ensures the privacy of this information as it flows through the company.
Also Check: What Is Government Mortgage Relief Program
The Early Years: User Provisioning And Mounting Regulations
To understand IGA, its important to understand what provisioning is and how user data was initially stored. User provisioning is the process that ensures that user accounts are created with the proper permissions. IT administrators use provisioning to monitor and control access to systems and applications.
In the early years of the digital age , user provisioning was rather straightforward as it focused solely on users within an organization. Access to users outside an organization, like customers or citizens, was not common. Additionally, there werent as many systems within an organization to manage access to, making the provisioning process relatively manageable.
During this time, servers housed user accounts and identity data centrally on on-premises systems within the enterprise. However, in the mid-late 1990s as the .com market rapidly took off and external user access to systems and applications became ubiquitous, more sensitive user data such as name, address, social security number, country code, email address, bank account number, etc. were collected by global organizations. The need to protect this personally identifiable information , the systems and applications that hosted this information quickly became critical. To address these requirements, new regulations were enacted that mandated stricter security protocols for user access permissions, required improved controls and policies to prove to auditors that the protocols had been implemented.
Forgerock Identity Governance And Administration
The ForgeRock Identity Governance and Administration solution is an integral part of ForgeRocks comprehensive identity platform. It allows you to establish policies for user access rights and continuously monitor their proper implementation from a centralized location. Through a periodic access review process tied to a powerful workflow engine to ensure closed-loop remediation and built-in risk management and reporting you can strengthen your security posture and automatically drive regulatory compliance.
Learn more about identity governance and administration and ForgeRock IGA by watching the webinar The Evolution and Modernization of Identity Governance or contact us today.
Also Check: California Government Tort Claim Form
Reduce Risk And Strengthen Security
Compromised identities caused by weak, stolen ordefault user credentials are a growing threat to organizations. Centralizedvisibility creates a single authoritative view of who has access towhat, allowing authorized users to promptly detect inappropriate access,policy violations or weak controls that put organizations at risk. Identitygovernance solutions enable business and IT users to identify risky employeepopulations, policy violations and inappropriate access privileges and toremediate these risk factors.
Evolve Iga To Support Higher Levels Of Automation
Identity governance and administration is the largest investment that most identity and access management programs will make. Its also the highest risk IAM technology to deploy.
IGA deployment efforts are about 80% business process automation, yet organizations continue to take tool-centric implementation approaches and underestimate efforts involving people and processes.
Hyperconnected digital business environments are forcing organizations to manage large numbers of users across many different applications, platforms and operating systems. Most organizations struggle to handle this proliferation of identities and systems. Implemented carefully, todays increasingly cloud-delivered IGA solutions can help you successfully rein in digital era identity challenges.
Critical Capabilities for Identity Governance and Administration
IGA tools help organizations control access risks, achieve and maintain compliance, and improve efficiency by managing user accounts and entitlements in infrastructure systems and applications. Security and risk management leaders responsible for IAM should evaluate critical capabilities during IGA tool selection.
You May Like: How To Apply For Government Subsidized Housing
What Are The Challenges And Risks Of Implementing Iam
Despite IAMs presence up and down an organizations security stack, it doesnt cover everything. One issue is how users birthright access policies evolve. These are the access rights that are given to new users when they begin working at a company. The options for how new employees, contractors, and partners are granted this access touch on numerous different departments, and delegating this to the right people and managers becomes an issue, says Cser. IAM systems should be able to detect access rights changes automatically, but they often dont.
This level of automation becomes important, particularly if we consider automated on and offboarding of users, user self-service, and continuous proof of compliance, Steve Brasen, research director at EMA, wrote in a blog post. Manually adjusting access privileges and controls for hundreds or thousands of users isnt feasible. For example, not having automated leaving processes will almost guarantee that unneeded access rights havent been completely revoked.
You cant do this with Excel spreadsheets or other manual methods, says Cser, but underlying complexity of user onboarding hasnt gotten any better over time, even as IAM products have gotten better at handling workflows and business processes.
Security Risks Are Evolving Are You Keeping Up
More cloud infrastructure and apps come online every day. With breaches increasing in severity and number, organizations need a cloud-architected solution to control access, protect critical assets, and minimize risk.
Powered by a comprehensive identity warehouse and user experience to drive frictionless access, Saviynt Identity Governance and Administration enables Zero Trust in your hybrid and multi-cloud environment.
Don’t Miss: Government Bank Owned Foreclosed Homes In Polk County
Why Iga Is Important To The Business
IGA is a key element of any organisations IAM architecture, covering identity lifecycle management and access governance. IGA is essentially the ability to reduce the risk that comes with excessive or unnecessary user access to applications, systems and data.
This is achieved by enabling policy-based centralised orchestration of user identity management and access control, and by working with other IAM processes to automate workflows and meet compliance requirements.
Business drivers for improving IGA capabilities include improved competitive advantage, easier partnering and reduced costs. Effective IGA is key to improved IAM, which enables businesses to deliver better services tailored to customer requirements.
How Iga Supports Iam
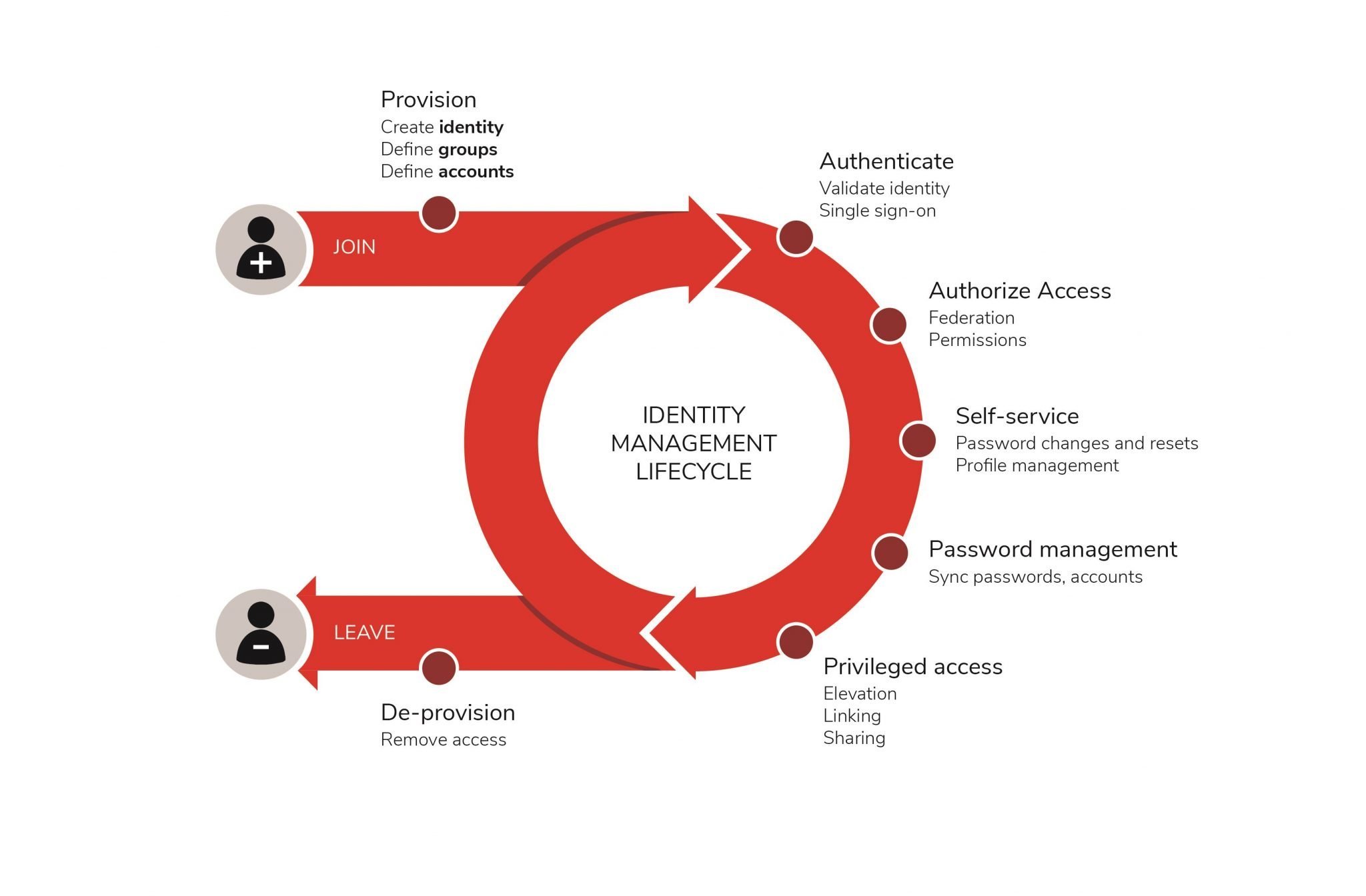
Writing in Computer Weekly, Kuppinger Coleâs Warwick Ashford notes that IGA is at the heart of an enterprise IAM strategy.
IGA is essentially the ability to reduce the risk that comes with excessive or unnecessary user access to applications, systems and data. This is achieved by enabling policy-based centralized orchestration of user identity management and access control, and by working with other IAM processes to automate workflows and meet compliance requirements.
Ashford recommends that enterprises consider the following when evaluating IGA solutions:
â¢Support for a broad range of IT infrastructure and business applications.
â¢Management of non-human entities, including robotic processes.
â¢Alignment with applicable regulatory requirements for consent management, access request, access review, and segregation of duties.
â¢Management of access rights and governance for privileged accounts.
â¢Hosting in the cloud to enable shorter deployment, faster upgrade, and lower cost of ownership.
Identity and Access Management White Paper
Build a Culture of Governance with Clear Skye IGA on ServiceNowIdentity and Access Management
Also Check: Government Assistance Child Care Texas
Identity Governance And Role
Role-Based Access Control is a model of assigning system access to people based on their roles in an organization. In the Identity Governance tool used at U-M, a Business Role defines the specific access that is needed for a group of people who share common job responsibilities.
Selection criteria within an IG Business Role identify users who match specific identity attributes in the organization, such as a set of similar job titles and department IDs. Then, the IG tool can automatically assign the collection of access to each person who fits the selection criteria. The access may be to multiple systems depending on which systems are integrated with the IG tool.
Identity attributes are used to automatically assign access across various systems. The manual work of requesting, approving, and granting access may only be needed for exceptions to the framework established with IG. This also ensures that:
- People receive access quickly, unless the access is an exception to the normal rules defined by an IG Business Role.
- System security is improved when access is promptly removed from people who no longer match the selection criteria of an IG Business Role.
Processes Become More Scalable
After seeing how IGA solutions streamline user identity lifecycle management and reduce risk while improving compliance and security, its easy to see how they can help your organization scale over time. Those two main benefits working together allow for scalability that wouldnt exist otherwise. Sticking to manual processes and having little to no visibility into your IT systems doesnt provide any good opportunities for scaling properly, and if youre going to scale, whether its now or later, you need to have the processes, workflows, and automations in place before doing so successfully.
Some ways that IGA solutions facilitate organizational scaling are through:
- Reduced operational costs due to automated processes that require less of a time commitment from IT admins
- Efficient access to resources is provided to employees, meaning that as your organization grows, its quick and easy to provision and deprovision access to resources en masse, rather than dealing with each machine individually
- Inherent compliance improvement is found within IGA tools, and tools that improve compliance and reduce risk are ones you want to keep on deck as you grow, as compliance only gets more difficult as your organization gets larger and harder to manage
Also Check: City Of Las Vegas Government Jobs
Iam’s Role In The Organizations Security Stack
IAM plays a series of critical roles at several places in an organizations security stack, but it isnt often thought of that way because these roles are spread out across different groups, such as development teams, IT infrastructure, operations managers, the legal department and so forth. IAM teams are no longer making all the related decisions about IAM, said Gartner in its planning guide.
First, IAM techniques are just the beginning of managing a secure network. They requires companies to define their access policies, specifically outlining who has access to which data resources and applications and under which conditions they have access.
Many companies have evolved their access control policies over time, and the result is that they have overlapping rules and role definitions that are usually outdated and, in some cases, provisioned incorrectly. You have to clean up your identities and revoke all the extra privileges that users dont need so that you dont migrate a mess, says Cser. This means spending more time on upfront design.
Sailpoints Identity Governance And Administration Solutions
In March, we were recognized as the 2020 Gartner Peer InsightsCustomers choice for IdentityGovernance & Administration . This distinction recognizes the vendorswho are top-rated by their customers, based on a series of customer-submittedreviews.
When it comes to identity governance, no company is better suited to help you solve your unique security and compliance challenges. Learn how we can help you protect your sensitive data, wherever it lives.
Identity Governance in Action
Whats Cloud Identity Governance?
Cloud-based identity governance offers the same security, compliance and automation delivered by traditional enterprise-class identity solutions, coupled with a lower total cost of ownership and faster deployment. Put simply, identity provides the power to make the cloud enterprise secure.
Cloud is transforming the way we work.Organizations must effectively address todays complex business challenges, andtodays enterprise is becoming a cloud enterprise. While companies are becomingmore comfortable with moving strategic and mission-critical applications intothe cloud, it can feel overwhelming to consider solutions like identity as aservice . They often avoid identity governance because they believe theylack the budget, time or skilled identity resources required to implement it.However, these are no longer inhibitors to reaping the benefits of identitymanagement.
Isnt identity governance software only available on-premises?
Is IGA only for big businesses?
Also Check: Suing The Federal Government For Constitutional Violations
What Is Identity Governance And Administration
Identity Governance and Administration , also known as identity security, is at the center of IT operations, enabling and securing digital identities for all users, applications and data. It allows businesses to provide automated access to an ever-growing number of technology assets while managing potential security and compliance risks.
Identity Governance in Action
Role Of The Identity And Access Management Team In Data Governance
Because data governance is mainly about data and access management, the identity and access management team ensures accountability through the implementation and documentation of certain security protocols. This can be done through:
- Data Segmentation This involves identifying the types of data flowing through your organization and segmenting depending on what needs protection.
- The Principle of Least Privilege This involves which roles need access to what data and setting permissions around those needs.
- Access Request Process This involves establishing data request processing outside of the normal scope.
Data governance is essential for any organization today. It not only allows for the effective flow of data within the company to enhance productivity, but it also ensures that data does not fall into the wrong hands. Increasing regulations and contractual agreements are forcing companies as the primary drivers to think about data governance. Do you have a data governance strategy in place? If not, it might be time to implement one.
You May Like: How To Get Fund For Startup From Government
Benefits Of Unifying Iga And Pam
- A single point of control for provisioning all identity access in the organization.
- Confidence that privileged access sessions will be performed within identity governance policy.
- Easier audit discovery of inconsistencies in access authorizations, including segregation of duties violations and other role-based access restrictions common in compliance.
- Streamlined process of onboarding and off-boarding all users, both internal and external.
How Iam Can Be Limited
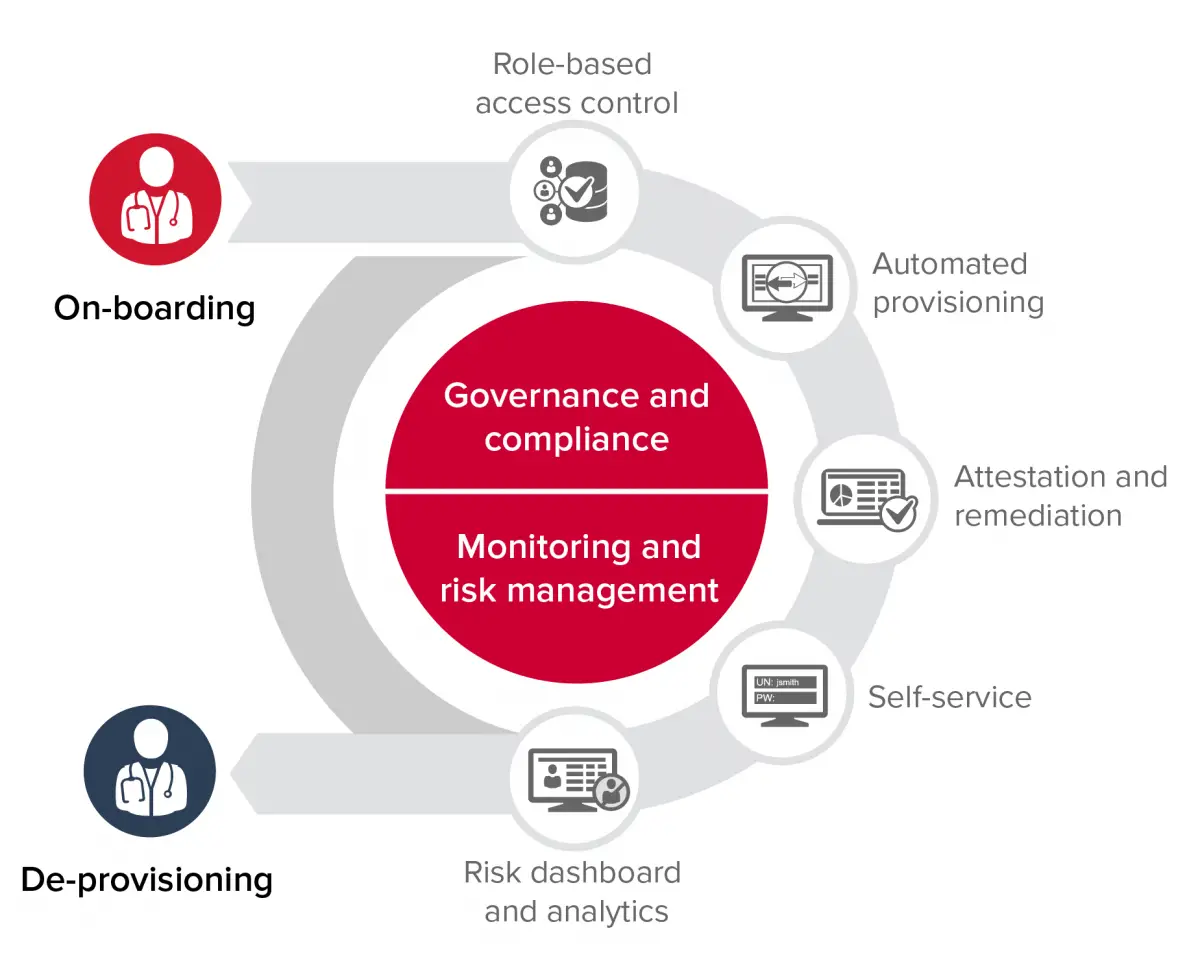
Many IAM solutions are restricted to a single enterprise system or business line â managing access only for Human Resources assets, for example, or only for the customer relationship management system.
This presents a clear limitation. IAM may exist in a silo, but knowledge workers do not. In any given day, they may need to interact with a dozen business systems â not just HR and CRM but also email, finance, supply chain management, Help Desk, and so on.
An individual userâs âidentityâ is connected to all these systems. When IAM solutions are restricted to a single system, enterprises are forced to manually manage, audit, and update user identity and access. This creates an inefficient and error-prone process that could lead to security vulnerabilities or failed compliance audits.
Read Also: Federal Government Day Care Centers